16 June 1997
Source:
http://www.atsc-army.org/cgi-bin/atdl.dll/query/download/FM/100-6/fm100-6.zip
(1.11MB - Full document text and images)
27 AUGUST 1996
By order of the Secretary of the Army:
General, United States Army
Chief of Staff
Official:
JOEL B. HUDSON
Administrative Assistant to the
Secretary of the Army
DISTRIBUTION:
Active Army, USAR, and ARNG: To be distributed in accordance with DA Form 12-11E, requirements for FM 100-6 (Qty rqr block no 5425).
Field Manual
No. 100-6
Department of the Army
Washington, DC, 27 August 1996
INFORMATION OPERATIONS
Contents
Chapter 1 OPERATING ENVIRONMENT
-
Geostrategic and Technological Environment
Threats to the Information Infrastructure
Challenges
Information Dominance: The Response to the Challenges
-
Cognitive Hierarchy
Strategy
Components of Information Operations
Information Activities
-
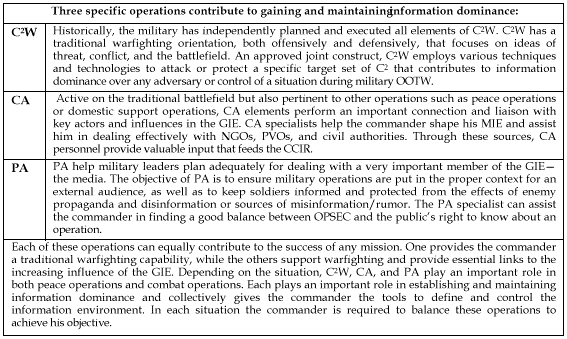
Command and Control Warfare
Civil Affairs Operations
Public Affairs Operations
Chapter 4 RELEVANT INFORMATION and INTELLIGENCE
-
Relevant Information
Intelligence
-
Functions
Role
Signal Support
Future Technology
Security
Management
Chapter 6 PLANNING AND EXECUTION
-
Planning
Execution
[Separate files below]
Appendix A PLANS AND ORDERS (34K)
-
Annex A Major Operations Plan Model: Operational Level
Annex B Sample C2W Annex
Appendix B RESPONSIBILITIES OF SUPPORTING AGENCIES (16K)
-
Joint Command and Control Warfare Center
Land Information Warfare Activity
Appendix C PLANNING CONSIDERATIONS (17K)
-
Support Planning Principles
Signal Support Requirements
C2W Planning Process
Appendix D STAFF ORGANIZATION AND TRAINING (8K)
-
Organization
Training
GLOSSARY (29K)
REFERENCES (12K)
INDEX (63K)
Preface
This manual addresses the operational context of information operations (IO), relevant terminology, and the environment of information operations. It supports battle command and provides guidelines for commanders that conduct IO to support all phases of the force-projection operating environment, including planning and executing early entry and force-projection operations in joint and multinational settings.
Military operations occur in peace and war. The traditional focus when discussing information and C2 was electronic warfare (EW), electronic countermeasure (ECM), and electronic counter countermeasure (ECCM) operations that take place during war. The focus of this manual is on command and control warfare (C2W), public affairs (PA), and civil affairs (CA). All are operations that the Army currently uses to gain and maintain information dominance as well as effective C2. Successful operations require effective C2 to transform military capabilities into applied military power. The more effective the force's C2 system, the more completely its capabilities can be realized in peace or war.
As the Army's capstone doctrine for IO, this manual supports soldiers and leaders that execute IO to support military operations. Not only does the doctrine herein provide commanders and their staffs with guidance to conduct information operations, it also serves as the foundation for development of US Army tactics, techniques, and procedures (TTP) manuals. It is also the foundation to refine existing training support packages (TSPs), mission training plans (MTPs), training center and unit exercises, and service school curricula. The manual provides a basis to examine organizations and materiel developments applicable to IO.
This doctrine applies to the total Army--active and reserve components and Army civilians. It is specifically oriented at the operational and tactical levels of military operations. It may be useful to other services, nonmilitary agencies, and allies involved in such operations.
The proponent of this manual is HQ TRADOC. Send comments and recommendations on DA Form 2028 directly to Commander, US Army Combined Arms Center, ATTN: ATZL-SWW-L, Fort Leavenworth, Kansas 66027-1352.
Unless this publication states otherwise, masculine nouns or pronouns do not refer exclusively to men.
Introduction
The Army is embracing a new era characterized by the accelerating growth of information, information sources, and information dissemination capabilities supported by information technology. This new era, the so-called Information Age, offers unique opportunities as well as some formidable challenges. New technology will enhance the Army's ability to achieve situational dominance on land, where the decisive element of victory for our nation has always been critical. At the same time, it will enable adversaries to employ many of these same capabilities. This new technology also allows the Army to transform itself.
The Army is changing the way it does business in the foxhole; in its schools and training centers; and in its doctrine, training, leader development, organizations, materiel development, and soldier development. Responding to the challenges and opportunities of the Information Age, the Army is preparing the warfighter for operations today as well as in the twenty-first century. Information and the knowledge that flows from it empower soldiers and their leaders. When transformed into capabilities, information is the currency of victory.
Information operations integrate all aspects of information to accomplish the full potential for enhancing the conduct of military operations. Information operations are not new. In their simplest form they are the activities that gain information and knowledge and improve friendly execution of operations while denying an adversary similar capabilities by whatever possible means. Effects of IO produce significant military advantage for forces conducting such operations.
Information is an essential foundation of knowledge-based warfare. It enables commanders to coordinate, integrate, and synchronize combat functions on the battlefield. To gain the relative advantage of position (maneuver) and massing of effects (firepower), commanders must act while information is relevant and before the adversary can react. Targeting an adversary's information flow to influence his perception of the situation or prevent him from having or using relevant information contributes directly to decisive operations. As the commander targets the adversary's information systems (INFOSYS), he protects his own. Realizing that absolute and sustained dominance of the information environment is not possible, commanders seek to achieve information dominance at the right place, the right time, and in the right circumstances. They seek information dominance that defines how the adversary sees the battlespace, creating the opportunity to seize the initiative and set the tempo of operations.
- The accuracy, lethality, and range of modern weapons have forced commanders to disperse their formations, decentralizing control and execution. Massing the effects of these dispersed systems depends on accurate information. Disruption of the flow of information or corruption of the information itself can negate the effects of weapons and systems. Instead of being limited to the physical destruction of people or war machines as the only path to battlefield success, armies now can target information or an adversary's INFOSYS to alter the battlefield chemistry and yield battlefield success.
- The speed and pervasiveness of data transmission in the Information Age are causing a revolutionary change in the nature of military operations and warfare. Targeting information extends beyond the battlefield and involves more than attacking an adversary's information flow while protecting the friendly information flow. It also requires awareness of, and sensitivity to, information published by nonmilitary sources. These information sources are able to provide tactical-level information in near real time to audiences throughout the world, with the potential of profoundly influencing the context of those operations.
- IO define the operational situation by generating understanding, providing context, and influencing perceptions. They enable and protect friendly INFOSYS; synchronize force application; connect hierarchical and nonhierarchical systems; link sensors, shooters, and commanders; and degrade, disrupt, or exploit adversary operations by attacking the adversary's command and control (C2). Units conduct IO across the full range of military operations, from operations in garrison, through deployment, to combat operations, to redeployment. IO greatly expand a commander's battlespace, including interaction with the media, industry, joint forces, multinational forces, and computer networks worldwide.
- Within the context of joint and/or multinational operations, the Army must be able to dominate the information environment in order to perform its missions in any contingency or conflict. The Army's force-projection capability is based upon accurate and timely information. IO can significantly enhance the Army's ability to deter aggression, to effectively execute the full range of operations, and to win decisively in combat.
Notwithstanding the synergy possible with the power of information and information technology, fog and friction will remain; the challenge of sorting out the signals from the noise amidst a mass of expanding data will also remain. Many solutions to the dilemma of uncertainty for the commander are technical. But there can be no information revolution without the human influence and understanding of soldiers and commanders who link and integrate information, technology, and action. IO do not offer any panaceas. Perfect knowledge is not the objective. The military objective remainsóto enter an operational theater capable of achieving superior relative combat power against an enemy, or to establish situational dominance in operations other than war (OOTW).
The Army's keystone doctrine in FM 100-5 describes how the Army thinks about the conduct of operations. This manual, while designed to enhance and enable the operations in FM 100-5, reaches out to accommodate and leverage newly emerging information technologies, especially digitization.
As the Army's capstone publication for information operations, this manual supports the National Military Strategy and explains the fundamentals of IO for the Army. IO doctrine reflects, and goes beyond, the joint military strategy of command and control warfare (C2W), which implements Department of Defense (DOD) information warfare policy. This manual --
- Identifies information as a major influence on operations at the tactical, operational, and strategic levels.
- Enables commanders to successfully integrate information, INFOSYS, and their effects across the full range of military operations. Such integration enables and enhances the elements of combat power.
- Creates synergy, which contributes to increased lethality, survivability, and tempo in combat, as well as highly credible and capable forces in OOTW.
This publication provides Army capstone doctrine and facilitates the transition to the Information Age.
Operating Environment
Army forces today are likely to encounter conditions of greater ambiguity and uncertainty. Doctrine must be able to accommodate this wider variety of threats. In so doing, the Army is prepared to respond to these worldwide strategic challenges across the full range of possible operations as part of a joint and combined team.
Commanders and their staffs operating in the Information Age face an increasingly complex environment. Commanders and staffs at all levels will encounter an expanding information domain termed the global information environment (GIE). The GIE contains those information processes and systems that are beyond the direct influence of the military or even the National Command Authorities (NCA), but nevertheless may directly impact the success or failure of military operations. The media, international organizations, and even individuals represent a partial list of GIE players.
This chapter describes the GIE domain and introduces the concept of information dominance as the key element for operating effectively within this new environment. To achieve information dominance, the commander must be able to dominate both the traditional maneuver-oriented battlefield and the military information environment (MIE), defined as that portion of the GIE relevant to his operation. To achieve the latter, the commander directs the acquisition, use, and management of friendly and enemy information and conducts command and control warfare (C2W) attack and protect operations.
GEOSTRATEGIC AND TECHNOLOGICAL
ENVIRONMENTS
Because of rapid advances in technology, especially in the information arena, the geostrategic environment of today has become increasingly complex and will become even more so in the future. Global communications accelerate and expand collective awareness of events, issues, and concerns. They ignite passions, spark new perspectives, crystallize deeply held beliefs, and compel people, nations, organizations and institutions everywhere to examine, define, and act on their interests. While many effects of this phenomenon may be benign and beneficial, others will create turbulence, confusion, chaos, and conflict. Such conflict may extend beyond the traditional battlefield to encompass espionage, sabotage, terrorism, economic competition, and efforts to shape public perceptions.In the Information Age, the United States is in the forefront of exploiting modern information technology to harness the explosive potential of rapid dissemination and use of information. The US economy, social and civil structures, and federal, state, and local governments have become dependent upon the rapid and accurate flow of information. At the same time, America exerts extraordinary influence throughout the world through its multinational media and commercial and entertainment industries. To a lesser degree, America is influenced by similar phenomena exerted from outside its borders. The global information infrastructure (GII) electronically links organizations and individuals around the globe and is characterized by a merging of civilian and military information networks and technologies.Developments in information technology will revolutionizeand indeed have already changedhow nations, organizations, and people interact. The rapid diffusion of information, enabled by technological advances, challenges the relevance of traditional organizational and managerial principles. The military implications of new organizational sciences that examine internetted, nonhierarchical versus hierarchical management models are yet to be fully understood. Clearly, Information Age technology and the management ideas it fosters greatly influence the armed forcesorganizations, equipment, how they train, how they fight, how they protect the force, or how they assist in resolving conflict.
Global Information Environment
- The global information environment includes--
All individuals, organizations, or systems, most of which are outside the control of the military or National Command Authorities, that collect, process, and disseminate information to national and international audiences.
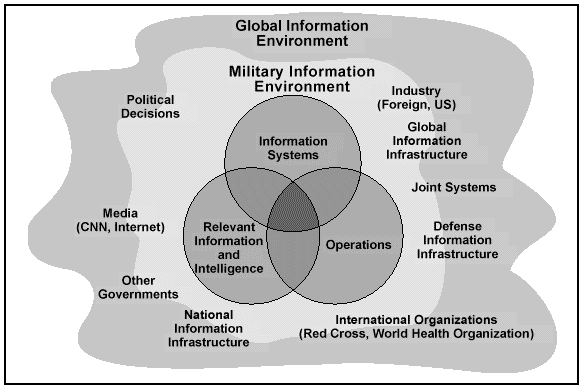
All military operations take place within the GIE, which is both interactive and pervasive in its presence and influence. Current and emerging electronic technologies permit any aspect of a military operation to be made known to a global audience in near-real time and without the benefit of filters. With easy access to the global or national information network, suppression, control, censorship, or limitations on the spread of information may be neither feasible nor desirable (see Figure 1-1).
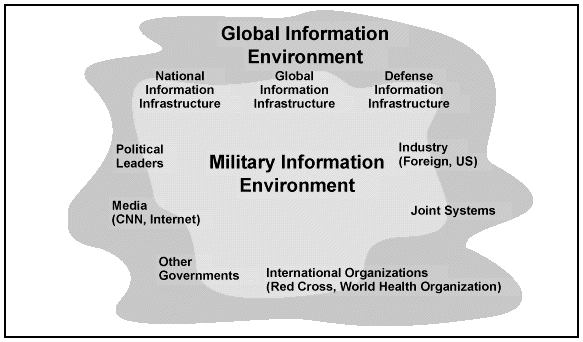
Figure 1-1. Information Environments (GIE and MIE)
Adversaries and other non-DOD organizations, including many actors, agencies, and influences outside the traditional view of military conflict, intrude into the MIE. Adversaries, perhaps supported by nonaligned nations, will seek to gain an advantage in the GIE by employing battlespace systems and organizations. In addition, the media, think tanks, academic institutions, nongovernment organizations (NGOs), international agencies, and individuals with access to the information highway are all potentially significant players in the GIE. These entities can affect the strategic and operational direction of military operations before they even begin. Independent of military control, their impact is always situationally dependent. Their activities may cause an unanticipated or unintentional effect on military operations. Such actors include--
- Government agencies such as the Department of State (DOS) or Federal Emergency Management Agency (FEMA).
- NGOs.
- Private voluntary organizations (PVOs).
- International agencies that provide a commercial service, such as the European Space Agency.
- Agencies that coordinate international efforts, such as the International Committee of the Red Cross or World Health Organization.
- Social and cultural elements, including religious movements and their leaders.
- Intelligence and military communications systems of other services, allies, and adversaries.
- Individuals with the appropriate hardware and software to communicate with a worldwide audience.
As technology enables ever greater numbers of individuals, groups, organizations, and nation states to be linked to the world through the GIE, these actors can be expected to pursue their interests by attempting to manipulate and control the content and flow of information within the MIE.
NEWS MEDIA
The role of the news media will continue to expand. The number of news organizations and their means to gather, process, and disseminate information is increasing exponentially. From the 147 reporters who accompanied the D-Day invasion in World War II, to the 800-plus reporters in Panama during Just Cause, to the 1,300 reporters in the Kuwaiti theater in Desert Storm, the ability and desire of the news media to cover US military operations is a given. Likewise, the demand by the US and international public to know what is happening, consistent with security and propriety, is also a given.
FM 100-5 observes that the impact of media coverage can dramatically affect strategic direction and the range of military operations. Clearly, the effect of written, and, more importantly, visual information displayed by US and international news organizations directly and rapidly influenced the nature of US and international policy objectives and our use of military force in Rwanda, Somalia, and in the former Yugoslavian republic.
INFORMATION INFRASTRUCTURES
Within the GIE, an intricate set of information infrastructures have evolved to link individuals, groups, and nations into a comprehensive network that allows for the increasingly rapid flow of information to all elements having access to the network. In practice, subelement labels are misleading as the information environment has no discrete boundaries. Each subelement is inextricably intertwined, a trend that will only intensify with the continuous application of rapidly advancing technology. This worldwide telecommunications web transcends industry, the media, and the military. It includes both government and nongovernment entities, the GII, the national information infrastructure (NII), and the defense information infrastructure (DII).
Global Information Infrastructure
An interconnection of communications networks, computers, data bases, and consumer electronics that puts vast amounts of information at the user's fingertips. The GII is a term that encompasses all these components and captures the vision of a worldwide, seamless, dynamic web of transmission mechanisms, information appliances, content, and people. Global accessibility and use of information in the GII is especially critical, given the increasing globalization of markets, resources, and economies. The GII--
- Includes more than just the physical facilities used to store, process, and display voice, data, and imagery. It encompasses a wide array of ever-expanding capabilities, including cameras, scanners, keyboards, fax machines, and more.
- Electronically links organizations and individuals around the globe and is characterized by a merging of civilian and military information networks and technologies.
National Information Infrastructure
All nations' NIIs are an integral part of the GII. The composition of the NII mirrors the GII, but on a reduced scale. The NII is--
- A series of components, including the collection of public and private high-speed, interactive, narrow and broadband networks.
- The satellite, terrestrial, and wireless technologies that deliver content to home, businesses, and other public and private institutions.
- The information and content that flows over the infrastructure, whether in the form of data bases, the written word, television, or computer software.
- The computers, televisions, and other products that people employ to access the infrastructure.
- The people who provide, manage, and generate new information and those that help others to do the same.
Defense Information Infrastructure
DII encompasses transferring information and processing resources, including information and data storage, manipulation, retrieval, and display. The DII connects DOD mission support, command and control (C2), and intelligence computers and users through voice, data imagery, video, and multimedia services. It provides information processing and value-added services to subscribers over the Defense Information Systems Network (DISN).
Military Information Environment
The sphere of information activity called the military information environment is defined as--The environment contained within the GIE, consisting of information systems (INFOSYS) and organizations--friendly and adversary, military and nonmilitary, that support, enable, or significantly influence a specific military operation.
The MIE, at a minimum--
- Reaches into space from the home station to the area of operation (AO).
- Reaches into time, from the alert phase through the redeployment phase.
- Reaches across purposes, from tactical missions to economic or social end states.
- Includes people, from deployed soldiers and families at home to local or regional populations and global audiences.
Within the context of the MIE, Army leaders exercising battle command will face many new challenges. They will also have many new operational opportunities. To realize these opportunities, information operations (IO) need to become an integral part of full-dimensional operations. The intertwined relationship between geopolitical strategic factors, technology, and management requires the adoption of a new perspective.
The proliferation of INFOSYS and the global information explosion brings more actors into the battlespace, implies new ways of managing force and forces, compresses the traditional levels of war in time and space, and gives operations a simultaneous and continuous character. A commander's battlespace now includes global information connectivity. As a result, tactical military actions can have political and social implications that commanders must consider as they plan, prepare for, and conduct operations. Know the situation now requires additional focus on nonmilitary factors. Commanders can best leverage the effects of new technology on their organizations by employing new and emerging automated planning and decision aids and new or different methods and techniques of control and management.
THREATS TO THE INFORMATION
INFRASTRUCTURE
The threats to the information infrastructure are genuine, worldwide in origin, technically multifaceted, and growing. They come from individuals and groups motivated by military, political, social, cultural, ethnic, religious, or personal/industrial gain. They come from information vandals who invade INFOSYS for thrill and to demonstrate their ability. The globalization of networked communications creates vulnerabilities due to increased access to our information infrastructure from points around the world. Threats against computers, computer systems, and networks vary by the level of hostility (peacetime, conflict, or war), by technical capabilities, and by motivation (see Figure 1-2). The bottom line is that threats to all forces, from strategic to tactical, exist from a variety of new and different sources, and they exist on a continuing basis even during periods of relative peace.
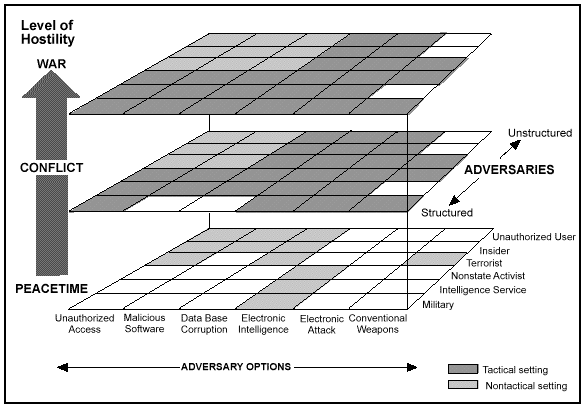
Figure 1-2. Threats to Information Systems
Adversaries have several options to influence or attack opposing INFOSYS and services. Attacks can be designed with a delayed effect, such as corrupting a data base or controlling program as well as immediate actions to degrade or physically destroy. Examples include--
- Unauthorized access, either to gain information or insert data.
- Inserting malicious software to cause a computer to operate in a manner other than that intended by its users. This category includes computer viruses, logic bombs, and programs designed to bypass protective programs.
- Corrupting data through use of malicious software, alteration of data, or use of electronic attack (EA) to make data misleading or useless.
- Collecting electronic intelligence, whether signals, radiation, or data.
- Conducting EA actions such as jamming, broadcasting false signals, or generating bursts of electromagnetic pulse (EMP).
- Using psychological operations (PSYOP) and deception to influence or oppose friendly INFOSYS.
- Attacking to physically destroy, degrade, or disrupt military communications and control networks or civilian systems upon which military operations rely. Weapons employed in such efforts range from terrorist bombs to artillery, missiles, and direct air attack.
- Using jamming and deceptive transmissions (EA) to attack commercial communications systems on which the Army relies. In such cases, more than communications can be disrupted. Sensors at all levels of operation can be jammed or triggered to produce misleading information. Both commercial systems and sensors are particularly vulnerable to the effects of EMP.
The effectiveness of military operations can be degraded if the user's confidence in the quality of the data can be eroded. Spurious data or false signals could be transmitted to erode confidence in the accuracy and effectiveness of such critical systems as the global positioning system (GPS).
Sources of Threats
Threats come from a range of sourcesfrom individuals (unauthorized users or insiders) to complex national organizations (foreign intelligence services and adversary militaries). Boundaries between these groups are indistinct, and it is often difficult to discern the origins of any particular incident. For example, actions that appear to be the work of hackers may actually be the work of a foreign intelligence service. Sources include unauthorized users, insiders, terrorists, nonstate groups, foreign intelligence services, and opposing militaries or political opponents.
UNAUTHORIZED USERS
Unauthorized users such as hackers are the source of most of the attacks against INFOSYS in peacetime. While to date, they have mainly targeted personal computers, the threat they pose to networks and mainframe computers is growing.
INSIDERS
Individuals with legitimate access to a system pose one of the most difficult threats from which to defend. Whether recruited or self-motivated, the insider has access to systems normally protected against attack. While an insider can attack a system at almost any time during its lifetime, periods of increased vulnerability for a system include design, production, transport, and maintenance.
TERRORISTS
Terrorists are increasing their use of commercial INFOSYS. Their actions range from unauthorized access, to an information network, up to direct attacks against the infrastructure (bombing, and so forth). Terrorist groups have also been identified using computer bulletin boards to pass intelligence and technical data across international borders.
NONSTATE GROUPS
New players, ranging from drug cartels to social activists, are taking advantage of the possibilities offered by the Information Age. They can acquire, at low cost, the capabilities to strike at their foes' commercial, security, and communications infrastructures. Moreover, they can strike with relative impunity from a distance. Besides attacking opponents directly, these actors use the international news media to attempt to influence global public opinion and shape perceptions of a conflict. They even attempt to inflame dormant issues into conflicts that otherwise would not arise.
FOREIGN INTELLIGENCE SERVICES
Active during periods of both peace and conflict, foreign intelligence services take advantage of the anonymity offered by computer bulletin boards to hide organized collection or disruption activities behind the facade of unorganized hackers. Their primary targets are often commercial and scientific networks rather than direct attacks on the military.
OPPOSING MILITARIES OR POLITICAL OPPONENTS
While the adversary's activities are more traditionally associated with open conflict or war, his manipulation of the news media during peacetime may help frame the situation to his advantage prior to the onset of hostilities.
Level of Hostility
The level of hostility generally reflects the scope and scale of an adversary's actions against friendly INFOSYS. In peacetime, unauthorized access to and use of computers, computer systems, and networks is the greatest current threat. Deliberate use of malicious software by an adversary could be used against communications, transportation, banking, power, and computation systems upon which both industry and the military might depend. We can expect an adversary to use malicious software to assess the vulnerability of our information networks.
As the crisis moves toward overt conflict or war, more direct and far-reaching attacks can arise against information and INFOSYS. Targets can include both units and their supporting infrastructures. Deployed tactical units may face the results of earlier intrusions and insertions, allowing embedded malicious software to cripple systems or degrade communications. By the time a unit is engaged in combat, it could have been subjected to a variety of overt and covert attacks against its INFOSYS.
On the battlefield, reliance on an extensive and potentially fragile communications infrastructure presents a vulnerability that entices exploitation. The initial candidates for attack could be vital information nodes or links such as CPs and communications centers. In addition to striking battlefield information nodes, adversaries can also strike the supporting infrastructure, both on and off the battlefield. Central system support assets such as power sources can be very difficult to repair or replace. Artillery, tactical ballistic missiles, and air power provide the major attack systems for most adversaries today. The ability of an adversary to strike will only grow as more capable systems, such as cruise missiles and precision-guided munitions, proliferate. This ability to strike with precision will be enhanced by the spread of such technologies as GPS, unmanned aerial vehicles (UAVs), and near-real time imagery satellites. If INFOSYS or facilities cannot be destroyed, they can be made untenable through contamination by chemical or biological weapons.
CHALLENGES
Commanders and national leaders face significant and interrelated challenges in dealing with and anticipating the effects of the global visibility of operations and rapid changes in information technology and their impacts in the GIE.
Information security
Two commonly recognized facts address why information security (INFOSEC) is an important challenge. First, the Defense Information Systems Agency (DISA) reports that over 95 percent of DOD communications during peacetime travel over the relatively unprotected public switch network (PSN) and are largely outside the direct control or influence of the military. In addition, a significant amount of open-source intelligence is carried by commercial means.
Continuous Operations
Because of the pervasive and intrusive nature of the MIE, preparation for dealing with IO must not wait until a unit receives a warning order to deploy. By that time, the commander and his staff must have already developed plans and procedures for dealing with the myriad aspects and influences in the MIE or risk being rapidly overcome by events.
Policy and Public Opinion
With global visibility, dramatic information displays and expert analyses of military operations in progress can rapidly influence public opinion and, therefore, policy related to the conduct of military operations. The population that receives and potentially reacts to this coverage includes the US public, decision makers, alliance or coalition partners, and other nations. It also includes potential or actual adversaries of the US. The news media will most likely provide 24-hour coverage of all perspectives on the operation.
Global visibility of operations can also affect a commander's decision-making. When the information in the GIE is inaccurate, incomplete, not presented in context, based on rumor or the result of purposeful misinformation or disinformation efforts, a commander may react in haste, make an emotional decision, or make choices that are inconsistent with the real situation, up to and including a termination of an ongoing operation. Effective commanders anticipate how the adversary might attempt to manipulate the news media in order to prevent a potential foe from setting the terms of the conflict in the public arena.
Morale
The global visibility of operations impacts a command's combat power by either enhancing or degrading soldier morale. Soldier spirit and perseverance, the will to win, dedication to the cause, and devotion to fellow soldiers and the unit can be rapidly undermined by what is being said in the GIE. The instant communications capabilities of these INFOSYS often disseminate information to soldierswhether accurate or inaccuratefaster than the military chain of command. Bad news, misinterpretation, inaccurate information, and misinformation (or disinformation) impact families and communities as well as soldiers, affecting their morale and commitment to the objective at hand and potentially undermining the critically important human psychological dimensions discussed in FM 100-5. Nevertheless, Americans on and off the battlefield will continue to have free access to radio, television, and the press and be aware of events and circumstances.
Legal Considerations
Relatively few rules and laws govern the use of or access to many new INFOSYS or technologies. For that reason, IO confront legal challenges and other constraints such as rules of engagement (ROE) or status of forces agreements/status of mission agreements. Tension exists both in peace and during times of conflict. Collection of intelligence, or, simply, information in peacetime, is often limited by policy and/or law. Many policies and laws for using nonmilitary computer systems and other information networks during peacetime are yet to be determined. For example, the control or regulation of access on the internet to protect sensitive information or critical network nodes is largely unaddressed. What are the ROE for the INFOSYS in peace? In war? Close coordination with the supporting judge advocate is critical in confronting IO challenges based on legal considerations.
Because many of the actors and influences in the MIE are outside friendly military control, contracts or legal restrictions may prevent the military from controlling or influencing the use of civilian assets by an adversary. As an example, during hostilities an allied coalition force may depend upon an international agency to change the access codes for an imagery satellite to protect critical information in the area of responsibility (AOR). Without the change, the imagery is available in the open market. An adversary could, under commercial contract, download critical satellite imagery of the geographic region in near-real time as the satellite passed over the ground station.
INFORMATION DOMINANCE:
THE RESPONSE TO THE CHALLENGES
Information dominance is defined as--The degree of information superiority that allows the possessor to use information systems and capabilities to achieve an operational advantage in a conflict or to control the situation in operations short of war, while denying those capabilities to the adversary.
As we have come to recognize and depend on air superiority as a key condition for military success, information dominance has taken on a similar importance for military operations. This means that friendly knowledge and understanding of the situation must be more certain, more timely, and more accurate than the adversary's, revealing to the friendly commander the conditions that will lead to success. Creating information dominance has two equally important facets:
- Building up and protecting friendly information capabilities.
- Degrading enemy information capabilities.
The friendly commander achieves information dominance by gaining a knowledge advantage over an enemy.
The knowledge advantage generated by commanders using innovative technical and human techniques permits the force to more readily seize or retain the overall initiative and increase its lethality and survivability. Building a knowledge advantage requires a highly developed sense of what information is required and an ability to manage the use and dissemination of that knowledge to the right place, at the right time, for the desired purpose.
Successful leaders use the knowledge advantage by combining technical and human information capabilities with a broad intent statement and a clearly articulated concept of operation. Like air power, a ground commander can enjoy levels of knowledge advantage ranging from information supremacy to information parity. An enemy can also achieve a knowledge advantage at our expense. Information also vary dominance can change over space and time; it can by echelon. An Army may achieve information dominance at the operational level but lose it at the tactical level. The notion of information dominance is not new. Throughout history, commanders have sought to leverage the temporary opportunity that comes from an information advantage, whether it comes from knowledge of terrain or satellite imagery.
HISTORICAL PERSPECTIVE
For nearly two hours a succession of young officers, of about the rank of major, presented themselves. Each had come back from a different sector of the front. They were the direct personal representatives of the Commander-in-Chief, and could go anywhere and see anything and ask any questions they liked of any commander, whether at the divisional headquarters or with the forward troops. In turn, they made their reports and were searchingly questioned by their chief to unfold the whole story of the day's battle. This gave Field Marshal Montgomery a complete account of what had happened by highly competent men whom he knew well and whose eyes he trusted. It afforded an invaluable cross-check to the reports from all the various headquarters and from the commanders. I thought the system admirable, and indeed the only way in which a modern Commander-in-Chief could see as well as read what was going on in every part of the front.
Triumph and Tragedy, 1953
Directed Telescope
High-performing units are in large part distinguished from other units by their ability to effectively acquire and use information. Historically, high-performing units often gained the information advantage by using nontraditional means and methods. One such method is often referred to as the directed telescope. In concept, the directed telescope acquires information by supplementing the routine information flow, normally by-
- Going outside the traditional command and its hierarchical information channels.
- Using special operations units, reconnaissance teams or officers, and special communications networks.
These techniques are still valid and in use today. Modern technological innovations potentially make the advantages gained via the directed telescope technique almost routine. Innovations in sensors, processors, communications, and computers can give commanders immediate access to enemy and friendly situation information and thus a subsequent operational knowledge advantage.
Battlefield Visualization
Creation of an operational knowledge advantage supports the commander's battlefield visualization. Battlefield visualization is the process whereby the commander--
- Develops a clear understanding of his current state in relation to the enemy and environment.
- Envisions a desired end state that represents mission accomplishment.
- Visualizes the sequence of activity that will move his force from its current state to its end state.
A key step toward achieving information dominance is reached when one commander's level of battlefield visualization is significantly greater than his opponent's.
In the past, leveraging a knowledge advantage to decisively achieve a desired end state has been largely an intuitive process. Truly exceptional commanders have almost always possessed this trait; less successful commanders often have not. Information technologies now hold a potential for making this grasp of the battlespace, and the inherent opportunities it affords, more accessible to every leader, from field army to rifle platoon. The effect of these changes will be to enhance battlefield visualization by better supporting leaders with a deliberate and systematic information process based upon building blocks of raw data parsed and collated by both man and machines, synthesized into a coherent whole, and focused upon drawing understanding from the chaos of battle. Additionally, by linking commanders at different echelons, this same technology will enhance situational awareness and promote synchronized operational planning and execution. Ideally, the command will see and think as one.
Situational Awareness
A critical aspect of achieving a knowledge advantage over your adversary is the achievement of a condition of situational awareness throughout the force. Situational awareness includes--
- A common understanding of the commander's assessment of the situation.
- The commander's intent.
- The commander's concept of operation, combined with a clear picture of friendly and enemy force dispositions and capabilities.
IO potentially assure situational awareness appropriate to every level of an organization, down to the individual soldier. Systems being tested and fielded today offer commanders at all levels the potential of a collective, shared understanding of the battlespace. The commander's assessment of the situation, his intent, and the concept of operation provide the framework that applies throughout the organization. This framework fosters increased cohesion and unity of effort in the execution of operations. Figure 1-3 illustrates this relationship.
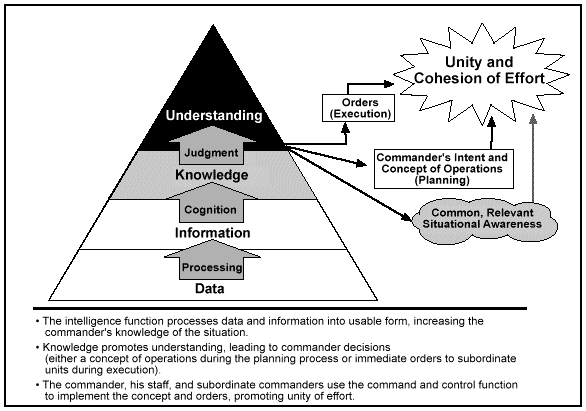
Figure 1-3. Situational Awareness
Situational awareness is inherently local, providing immediate context and relevance for the interpretation and use of new information as it is received by a soldier in a particular situation. The local situation relevant to each level and individual is developed within the common framework and shared vertically and laterally as appropriate. This situation not only retains the advantage of hierarchical structure (common framework and intent) but also adds the advantage of nonhierarchical INFOSYS that enable decentralized adaptation and action to local situations throughout the command.
Developing the flexibility of a nonhierarchical structure places a greater obligation on the commander to clearly articulate his intent and concept of operations. Traditionally, commanders ensured that both intent and concept were understood two echelons up and down in a hierarchical structure. Information technology now makes it possible for a senior commander's intent and concept to be relatively easily shared throughout the command whenever doing so will enhance the operation. The art of command requires clearly stating a common framework with sufficient freedom for local adaptation and application. Proliferation of that understanding, potentially to all leaders on the battlefield, gives the force a singular perspective and a clarity of focus that optimizes its combat power against an opponent or enables it to control a situation in other operations. Denying an adversary a similar capability, such as degrading his situational awareness, is an equally important objective and is addressed in Chapter 3 under C2W.
Expanded Vision
Our traditional operational vision must expand to take full advantage of the potential contribution of IO to dominate the enemy while protecting friendly forces. Before any mental constraints are placed on intent or operational concept, commanders at every level assess those actors and elements that can affect upcoming operations, to include informational aspects. The commanders' assessments include actors and elements both within and outside of their control. The result of this process of thinking about the GIE is a manageable number of informational elements with which commanders decide to deal, which, by definition, constitutes the MIE for a particular operation. This expanded vision of the battlespace can include various combinations of space, time, purpose, and people.
The elements of an IO vision align with the combat functions associated with traditional operations. The MIE equivalent of the tactical advantage of high ground, or the flanking position, might be transformed into an information advantage of local and international recognition that the military operation is legitimate and has international support. Just as successful maneuver gives a commander more options than the enemy, a perception of credibility and support, or an ability to command and control, provides an advantage for informational maneuver. Maintaining this advantage requires constant assessment and adjustment. To this end, PSYOP-supported Special Forces (SF) teams in the countryside, civil affairs (CA) teams in urban areas, reports from PVOs, and media coverage provide a form of reconnaissance and surveillance, just as standard military reconnaissance and surveillance operations provide information that drives subsequent fire and maneuver.
The purpose of firepower in combat is the generation of destructive force against an enemy's capabilities and will to fight. The MIE equivalent of firepower, already included in doctrine, is the employment of lethal and nonlethal, direct and indirect capabilities through C2W. C2W uses deception, PSYOP, electronic warfare (EW), operations security (OPSEC), and destruction to attack an adversary's capabilities. At the same time, C2W protects friendly operations. US armed forces have always employed these capabilities, but they were recently integrated into operations under C2W. This integration improves the friendly targeting process by directing the power of traditional attack, deception, PSYOP, EW, and OPSEC at the adversary's decision cycle, thus gaining control of that cycle and helping generate information dominance.
While the 1993 version of FM 100-5 recognizes the impact of global news coverage on the scope, nature, and duration of major operations, recent events demonstrate that the GIE also affects operations at brigade, battalion, and company levels. Commanders at every level may now find that CA, military police (MP), public affairs (PA), PSYOP, and SF activities that support, enable, or influence operations have become integral to their decision process and operations and require careful coordination and synchronization to achieve maximum effect. Commanders must continue to carefully manage the separation of PA and PSYOP functions to preserve the integrity and credibility of PA operations. The methods of using C2W, PA, and CA together to enhance operations is discussed in detail in Chapter 3.
Activities that affect how operations are seen and perceived by different audiences are an increasingly prevalent and required calculation of battle command and a prerequisite for effectively visualizing battlespace. The requirement to identify the critical audiences, messages, and communications means is not new to leaders. However, it is gaining major significance for successful operations.
HISTORICAL PERSPECTIVEDuring the course of the Gulf War, the combined operations of the allied coalition effectively isolated, both physically and psychologically, a large element of Iraqi forces on Faylaka Island. Rather then reduce the island by direct assault, a tactical PSYOP team from the 9th PSYOP Battalion, aboard a UH-1N helicopter, flew aerial loudspeaker missions around the island with cobra gunships providing escort. The message told the adversary below to surrender the next day in formation at the radio tower. The next day 1,405 Iraqis, including a general officer, waited in formation at the radio tower to surrender to the Marine forces without a single shot having been fired.
Open Media Coverage
Besides forcing a broader view of the environment, IO imply closer attention to the media and the global visibility of operations. DOD and Army policy for principles of combat coverage require Army commanders to provide open and independent coverage by the news media as the standard means of providing the American public information about the employment and capabilities of their armed forces. This policy gives commanders and leaders at all levels the clear mission of preparing their soldiers to effectively deal with the media before, during, and after all operations.
The commander's primary tool at division-level and above for dealing with the news media is PA. PA addresses issues that are integral to all levels of war. Below division level, however, the commander has no special staff to discharge this responsibility. Often, brigade and smaller units have to house, support, and escort reporters. Commanders must understand and train their soldiers, as well as themselves, to plan for the presence of media and provide effective interviews to communicate legitimate information to the public, strengthen soldier morale and unit cohesion, and enhance their ability to accomplish their mission.
While the clear intent of this doctrine is to require commanders to pay closer attention to the media and its potential impact upon military operations, it is also clear that doctrine does not sanction in any way actions intended to mislead or manipulate media coverage of military operations. To the contrary, the Army accepts and fully endorses the healthy tension that exists between the normal desire of the media to inform the public as much as possible about military operations and the normal desire of commanders to control the information environment about those same operations to the greatest possible degree.
Information Management
Information management takes on increasing importance in meeting the challenges of global visibility, rapidly changing information technology, and their impact on the GIE. Mountains of data must be acquired and quickly translated into knowledge and understanding. Accomplishing this challenge requires a continuous, cyclical process. Decision-making has become increasingly dynamic and multidimensional. Decisions about current operations must occur simultaneously with decisions and planning about future operations. Decision-making must match the pace with which situational awareness changes.
Information technology now permits the horizontal movement and integration of information and provides a framework for local decision-making, potentially allowing the commander's span of control to increase without losing effectiveness. The dynamics affecting a commander's span of control are critical because the modern battlefield sees forces increasingly separated, leaving large gaps between formations and requiring each cluster of forces to act with greater autonomy within an expanded AO. Dispersion creates more subordinate force clusters, decentralizes decision authority, and creates a major requirement for coordinated effort. The nominal span of control is increased and overall situational awareness is more complicated.
Harnessing the potential of information to transform how the Army operates is critical to its success in the future. However, technology alone cannot provide leaders with automatic battlefield visualization, flawless situational awareness, easily expanded vision, or highly effective information management. In the final analysis, the products of our initiative to harness the potential of information can only support the application of a leader's judgment, wisdom, experience, and intuition to enhance his battle command.
An increase in the amount of information available does not guarantee certainty; in fact, it potentially increases ambiguity. Current staff organizations, procedures, and analytical methods must adjust to master the richer flow, faster pace, and huge volume of information. The challenge is to find better, not just faster, analysis and decision-making procedures.
Fundamentals
While reflecting the increased complexity and lethality of the modern battlefield, Army doctrine recognizes that advanced weapons and technologies are no better than the skill with which leaders and soldiers employ them against the enemy.FM 100-5This chapter outlines the nature of information and the fundamentals of IO by stating what they are, what they apply to, and how they relate to various activities of IO. The chapter discusses the components of IO--operations, relevant information and intelligence (RII), and information systems (INFOSYS). It concludes with a discussion of the six critical activities essential to a sound IO program: acquiring, using, protecting, exploiting, denying, and managing information and INFOSYS.
COGNITIVE HIERARCHY
Information is defined as--Data collected from the environment and processed into a usable form.
A given piece of data is largely meaningless by itself. Only when data is processed, that is, placed into a situational context, does it gain meaning and become, by definition, information. Knowledge is derived from information. Knowledge is information that has been tested and accepted as factual--
- Through cognition--the mental process that receives or develops unverified information (beliefs).
- Through assessment or testing to prove the information.
- By acceptance of the information as factual.
Commanders and their planners must always be sensitive to the difference between beliefs and knowledge. Untested beliefs, even when commonly held, differ from facts and are, in essence, opinions that can later prove to be wrong. Decisions based upon beliefs instead of facts are always at risk.
Understanding is achieved by using judgment to give knowledge relevance within a specific situational context. Ideally, understanding a situation supports a commander in battlefield visualization and creates the conditions from which plans can be formed and effective actions taken. See Figure 2-1.
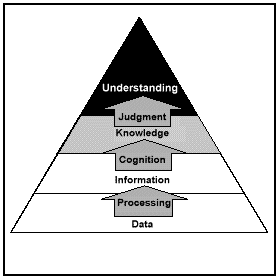
While it is certainly desirable to achieve full understanding of a situation before making decisions, commanders must be fully prepared to make decisions in an operational environment of ambiguity, characterized by imperfect information and incomplete understanding. Command decision-making will remain an art, not a science, even in the Information Age. A goal of IO is to narrow the gap between the art and science of command decision making.
STRATEGY
The National Military Strategy recognizes that information warfare (IW) is one of many capabilities within the US military elements of national power. IW can support the overall US Government strategic engagement policy during peacetime, crisis, conflict, and postconflict. The ability of the US Government to influence the perceptions and decision making of others greatly impacts the effectiveness of deterrence, power projection, and other strategic concepts.
This paragraph introduces and defines information warfare and explains its relationship with the Army's interpretation--information operations. In times of crisis, information can deter adversaries from initiating actions detrimental to interests of the US Government or its allies or detrimental to the conduct of friendly military operations. If carefully conceived, coordinated, and executed, IW--
- Contributes to defusing crises.
- Reduces the period of confrontation and enhances the impact of informational, diplomatic, economic, and military efforts.
- Forestalls or eliminates the need to employ combat forces.
Information Warfare
Information warfare is the term adopted by the Department of Defense (DOD) and the joint staff to recognize a range of actions taken during conflict to achieve information superiority over an adversary. It is specifically defined in CJCSI 3210.01 as--
Actions taken to achieve information superiority by affecting adversary information, information-based processes, information systems, and computer-based networks while defending one's own information, information-based processes, information systems and computer-based networks.
The objective of IW is to attain a significant information advantage that enables the total force to quickly dominate and control the adversary. The strategic goal of IW is to seize and maintain a decisive advantage by attacking an adversary's NII through exploitation, denial, and influence, while protecting friendly INFOSYS. IW offers either side the chance to strike at a distance with relative safety.
The Army, recognizing that IW as currently defined by DOD is more narrowly focused on the impact of information during actual conflict, has chosen to take a somewhat broader approach to the impact of information on ground operations and adopted the term information operations. The Army has adopted this broader approach to recognize that information issues permeate the full range of military operations (beyond just the traditional context of warfare) from peace through global war. IO implement the IW policy for the land component commander.
Information Operations
Information operations integrate all aspects of information to support and enhance the elements of combat power, with the goal of dominating the battlespace at the right time, at the right place, and with the right weapons or resources. IO are defined as--
Continuous military operations within the MIE that enable, enhance, and protect the friendly force's ability to collect, process, and act on information to achieve an advantage across the full range of military operations; IO include interacting with the GIE and exploiting or denying an adversary's information and decision capabilities.
Units conduct IO across the full range of military operations, from operations in garrison, through deployment, to combat operations, and continuing through redeployment upon mission completion.
COMPONENTS OF
INFORMATION OPERATIONS
Activities to support IO include acquiring, using, protecting, managing, exploiting, and denying information and INFOSYS. These activities take place within three interrelated components of IO: operations, RII, and INFOSYS. These components operate within a battlespace established by the MIE. (See Figure 2-2.) Army organizations conduct these IO activities as part of a dynamic, iterative process to support each component in an integrated full-dimensional operation.
Operations
C2W, CA, and PA are the three operations the Army currently uses to gain and maintain information dominance and effective C2.
C2W OPERATIONS
C2W is the warfighting application of IW in military operations. The aim of C2W is to influence, deny information to, degrade, or destroy adversary C2 capabilities while protecting C2 capabilities against such actions. C2W is composed of two major branches:
- Command and control-attack (C2-attack).
- Command and control-protect (C2-protect).
C2W planning is conducted throughout the military operational continuum, from peacetime through termination of hostilities. In the past, the primary warfighting objective was to concentrate physical and destructive combat power against the adversary's personnel and equipment, that is, tanks, airplanes, artillery, air defense. C2W is discussed in detail in Chapter 3.
By 1986, AirLand Battle further evolved this thinking by linking ground and air operations to achieve depth and synchronization. A paramount consequence of AirLand Battle was the intention to strike at reserve, reinforcing, and second-echelon forces. This led in 1993 to an extended operational strategy of deep operations, with long-range weapons and Special Forces. Looking at high-value targets, deep operations strategy sought to destroy, degrade, deny, and disrupt critical C2 nodes as one of its primary objectives.
Today, C2W operations integrate and synchronize the capabilities of PSYOP, deception, OPSEC, and EW to facilitate the application of appropriate systems and forces to execute IO. While C2W has had a primarily offensive focus in the past, it now includes both C2-attack and C2-protect. Although these two disciplines of C2W have been practiced by successful armies since the beginning of recorded history, modern warfare with its emphasis on information and INFOSYS requires a new perspective. Three factors make C2W considerations critical when operating in today's environment:
- Continuous, high-volume information flow dictated by the relationship of modern military technology and military operations.
- Vulnerabilities created by widespread incorporation of advanced technology for INFOSYS and intelligence.
- The radical improvement in INFOSYS and intelligence capabilities resulting from explosive advances in technology.
The complexity and range of today's MIE increases the difficulty of achieving a comprehensive disruption of an adversary's C2 capabilities through any single attack or application of combat power. This places a premium upon the effective integration and synchronization of friendly physical destruction, EW, deception, and PSYOP to achieve maximum results when launching attacks. Likewise, careful integration and synchronization is also required to fully protect our critical INFOSYS/intelligence architecture from adversary attacks. Without the complete and thorough integration and synchronization of the five C2W elements across both C2-attack and C2-protect, operational effectiveness will be reduced and potential vulnerabilities exposed.
C2-Attack
The goal of offensive C2W, specifically C2-attack, is to gain control over our adversary's C2 function, both in terms of flow of information and level of situational awareness. With effective C2-attack, we can either prevent an adversary from exercising effective C2 or leverage it to our advantage.
C2-attack can strike at the adversary's capabilities at all echelons, targeting personnel, equipment, communications, and facilities in an effort to disrupt or shape adversary C2. RII plays a key role in C2-attack planning and operations, with the creation and maintenance of regional data bases on personal, historical, and cultural influences, intelligence-preparation-of-the battlefield (IPB), and battle damage assessments (BDA)--both soft and hard kill. The principal C2-attack approach for influencing the adversary's C2 is the synchronized application of the six information activities.
C2-Protect
C2-protect seeks to maintain effective C2 of friendly forces by negating or turning to a friendly advantage the adversary's efforts to influence, degrade, or destroy friendly C2 systems. C2-protect is divided into active and passive measures and seeks to limit the vulnerability of forces (personnel, equipment, and information) to hostile action, even as deployed forces face ever-expanding threats and adversary capabilities. C2-protect includes countering an adversary's propaganda to prevent it from affecting friendly operations, options, public opinion, and the morale of friendly troops.
CIVIL AFFAIRS OPERATIONS
CA support to IO provides an integral role of interfacing with critical actors and influences in the GIE. Whether in peace, conflict, or war, conducting military operations, consolidating combat power, and seeking information dominance are improved when leveraging CA support. Although conditions differ across the spectrum of conflict, CA activities establish, maintain, influence, or exploit relations among military forces, civil authorities, and the civilian populace in an AO to facilitate military operations. For example, during Operation Restore Democracy, CA activities informed the local populace through the news media, public discussion, and PSYOP informational products and programs about the reestablishment of the legitimate Haitian government. This created an information exchange that promoted understanding of, confidence in, and positive perception of measures supporting military operations.
The civil-military operations center (CMOC) can be established to interact with key actors and influences in the GIE, such as NGOs, PVOs, and local authorities. CA elements support military operations by applying their skills and experience in public administration, economics, public facilities, linguistics, cultural affairs, and civil information and by collecting information relevant to the commander's critical information requirements (CCIR). CA personnel have an intricate and important role in providing information during both the intelligence cycle and the operational planning cycle.
Commanders include CA operations in their planning guidance. CA planners must consider all available support and information to ensure successful completion of the CA mission. CA forces are well-suited to plan, coordinate, support, and, if directed, supervise various operations to support US objectives.
PUBLIC AFFAIRS OPERATIONS
Most military operations are conducted under the full glare of public scrutiny. National and international news media coverage plays a major role in quickly forming public debate and shaping public opinion. The news media serves as a public forum for the analysis and critique of goals, objectives, and actions. It can impact political, strategic, and operational planning, decisions, and mission success or failure. The reality of near real-time information, processed and transmitted at greater speeds and to wider audiences than in the past, has bridged the gap between what occurs on the ground and the goals and objectives of the National Military Strategy. Therefore, the public affairs officer (PAO) monitors public perceptions and develops and disseminates clear and objective messages about military operations. Moreover, commanders must involve themselves also in this dimension of IO. PA personnel--
- Assist the commander by working to establish the conditions that lead to confidence in and support of the Army.
- Support open, independent reporting and access to units and soldiers.
- Seek a balanced, fair, and credible presentation of information that communicates the Army story through an expedited flow of complete, accurate, and timely information.
The commander uses his internal information program (formerly command information) to inform soldiers about where they fit in, what is expected of them, and how they help accomplish the mission. This information also helps soldiers combat the effects of enemy propaganda or misinformation. Commanders, through their PAO, initiate, direct, and emphasize internal information topics and programs. Every soldier must receive information specific to the operation through command channels and world, national, and local news. The media is an important information channel to the American public; however commanders, staff officers, and soldiers must balance OPSEC and other operational requirements when working with the media.
PA personnel support commanders by assessing the information environment and advising them on the PA implications of current and future operations. Leaders understand the importance of achieving a balanced, fair, and credible presentation of information to both internal and external audiences. Leaders integrate PA into their decision-making process by considering it in their assessment of the situation and development of courses of actions, plans, and orders. Commanders ensure that PA operations are synchronized with other combat functions and promote early coordination of PA, CA, and PSYOP functions during the planning process. A continual exchange of information must exist during execution as well. Although each function has a specific audience, information will overlap, making it crucial that messages are deconflicted and coordinated.
Relevant Information
and Intelligence
Leaders have struggled with how to best capitalize on available information throughout the history of organized warfare. The drive to know as much as possible about their own forces--location, combat effectiveness, current activity--and the enemy's--location, disposition, combat effectiveness, intended actions--has been a durable characteristic of successful commanders, regardless of the time period or nationality. Today, commanders operate in an environment increasingly marked by the rapid flow of information and decisions among strategic, operational, and tactical levels. These factors are complicated by an explosive expansion in the opportunities for access and the manipulation of operationally relevant information by the wide array of individuals, organizations, and systems found in the GIE.
Ultimately, effective C2 depends on ensuring that the right person has the right information at the right time. Intelligence, the commander's source of relevant information about the adversary, takes on increased, even crucial, importance in the Information Age. Because IO give battlespace global connectivity, intelligence on current or potential adversaries must be prepared on a global scale. Interaction with the MIE requires timely intelligence about many aspects of current or potential adversaries, to include cultural, political, and commercial aspects.
Commanders must have information to command. Information allows the commander's decision-execution cycle to function and gives direction to actions by the force to accomplish their operational missions.
The collection, processing, and dissemination of relevant information is the key to achieving situational awareness throughout the force, which creates the opportunity for unity of effort toward mission accomplishment. The commander operates within the GIE, adjusting his MIE to enhance his situational awareness as appropriate for the operation at hand.
The commander focuses on RII requirements. The commander's operational requirements dictate the critical information requirements, which in turn dictate the RII collection effort. To be effective, the unit's intelligence cycle must be managed to provide information based on the priorities in the concept of operations. A key to successful IO is an accurate IPB focused on the MIE. During combat operations intelligence analysts must continually perform an information-oriented BDA to ensure IO remain effective. RII support to IO begins in peacetime and must be continuous throughout all phases of an operation or campaign.
Advances in information technology are mandating changes in how RII support is provided. First, communications connectivity allows broadcast dissemination of information. This incorporates direct downlink of raw data from multiple sensors to multiple echelons simultaneously and the broadcast of finished information products from theater, departmental, or national production agencies to deployed forces. Information can be provided on a push or pull mode to deployed units.
IO requires the fusion of information from a variety of sources. Advances in sensors, processors, and communicators are combining to provide detailed, timely reconnaissance and surveillance of almost any place on the globe. Both military and nonmilitary sources provide information that can be used to produce RII. Open-source intelligence or reporting will provide much order of battle (OB) and technical data. An OB focused on command, control, communications, computers, and intelligence (C4I) includes data collection and information processing systems, command systems, and reconnaissance, intelligence, surveillance, and target acquisition (RISTA) systems.
Successful integration of IO requires an IPB grounded in a thorough understanding of an adversary's capabilities and decision-making style. An IPB based on C4I focuses on an adversary's decision requirements. These are selected in relation to the friendly commander's priority intelligence requirements (PIR) and describe in detail the decisions the adversary must make to conduct his battle plan. From there, the focus shifts to the information sources that feed or influence the adversary's decisions such as sensors, the platforms on which they are deployed, and their supporting C3 systems. The results should include data on current operations, capabilities, and vulnerabilities. RII as a component of IO is addressed in detail in Chapter 4.
Information Systems
INFOSYS collect, process, and disseminate information relating to current and future operations. Automation has made great advances in information processing, but human beings remain the most effective system for determining relevance and fusing information. INFOSYS are those means that enable commanders and their staffs to--
- Monitor the current situation.
- Synchronize operations.
- Integrate and synchronize operations across battlefield operating systems (BOSs).
- Coordinate joint air and naval support.
- Update weapon systems targeting parameters.
- Control close, deep and rear operations as one operation.
ARCHITECTURE
INFOSYS are essential to the effective application of military power. The Army's integrated architecture of advanced INFOSYS maximizes the C2 capabilities of land forces in all operating environments. The road map for exploiting current and future information technologies to enhance Army operations is the Army Enterprise Strategy (AES). The AES and other initiatives like C4I for the Warrior are reinforcing the important contributions INFOSYS make to information-based warfare. Of particular importance is the evolution of the Army's comprehensive information architecture with its three supporting initiatives focused on operational, system, and technical architectures. When completed, this initiative will create a common operating environment (COE) of standardized, interactive systems and templates for the collection, storage, and manipulation of all Army data bases.
Operational Architecture
The operational architecture will establish the required connectivity
among processes, functions, information, and organizations. It will show
what we do, what information we need to do it, and how often we need to exchange
information within the force.
System Architecture
The system architecture seeks to identify relationships among C4I components
of systems and create physical connectivity within the information system.
It uses an organizational context to show system allocation and network
structures and helps document engineering decisions, such as specific information
protocols and bandwidth.
Technical Architecture
The technical architecture will establish a set of rules governing the
arrangement, interaction, and interdependence of all the parts and elements
that together constitute our INFOSYS. It specifies the permissible standards
for designing C4I capabilities and is critical to the creation and maintenance
of interactive systems.
INTEGRATION
The integration of INFOSYS--both vertically and horizontally--facilitates tactical and operational agility, initiative, depth, synchronization, and versatility essential to Army success in joint and combined operations.
GLOBAL CONNECTIVITY
Global connectivity is essential for linking strategic, operational, and tactical aspects of IO and the ability to project forces worldwide. INFOSYS support operations globally with communications automation architectures, both space- and terrain-based. However configured, INFOSYS can provide such support with a minimum of physical repositioning to support C2, whether in a strategic deployment phase or moving for a tactical attack. Both military and commercial INFOSYS play important roles in this architecture.
Today, the Army applies information technologies to digitize the battlefield by providing integrated C2 that flows across each level of operation or war. The migration of the current Army Command and Control System (ACCS) to the Army Battle Command System (ABCS) incorporates a common C2 operating environment at all echelons. This integration of modern INFOSYS with our tactical units continues to enhance their connectivity, decision-making, and, ultimately, lethality, survivability, and the ability to control the tempo of operations. Advanced weapons system and sensor technologies based on interoperability, digitization, and spectrum supremacy will contribute directly to improved effectiveness of the force. Chapter 5 discusses the Army INFOSYS architecture in detail.
Any military--like any company or corporation--has to perform at least four key functions with respect to knowledge. It must acquire, process, distribute, and protect information, while selectively denying or distributing it to its adversaries and or allies.Alvin and Heidi TofflerWar and Anti-War: Survival at the Dawn of the 21st Century
INFORMATION ACTIVITIES
IO involves acquiring, using, protecting, exploiting, denying, and managing information and INFOSYS. When effectively executed, these critical activities supplement the human skills of battle command, speed decision making, minimize or eliminate uncertainty, focus combat power, help protect the force, harness organizational capabilities, link the MIE to the GIE, and enhance situational awareness for soldiers and leaders. These activities apply to both information and INFOSYS (hardware, people, organizations, and processes). Although listed sequentially, these activities are concurrent and seamless in their application (see Figure 2-3).
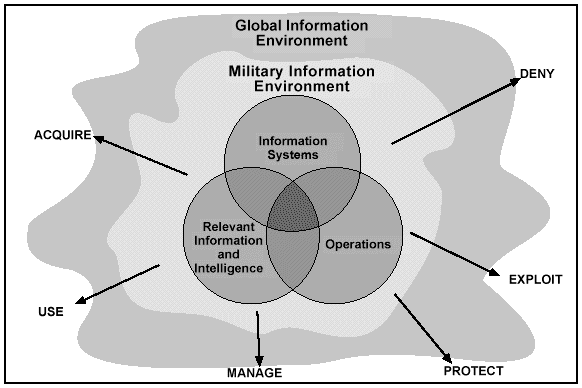
Acquire
Commanders must consider the nature of the information required before allocating resources to acquire it. Initial questions include--
- What information is needed?
- What is the nature of that information?
- How can that information be acquired?
Necessary information includes mission, enemy, troops, terrain and weather, and time available (METT-T) and the basic who, what, when, where, why questions. The nature of that information includes its accuracy, timeliness, and its overall relevance to the situation in consonance with the CCIR. Considering the available information sources and the nature of that information, commanders develop technical and tactical plans to acquire critical information.
Information can be acquired through personnel, technical means, intelligence collection systems, tactical reporting, and intelligence or information disseminated from other DOD or non-DOD agencies at operational, strategic, or national levels. Collection of information about adversaries and the environment is managed through the RII collection cycle.
Commanders determine the critical information for each operation and publish those requirements through their CCIR. The commander alone decides what information is critical based on the mission, his experience, and the higher echelon commander's intent. The staff may recommend CCIR to the commander as--
- Priority intelligence requirements to determine what the commander wants or needs to know about the enemy, his purpose, and/or terrain (how I see the enemy).
- Friendly forces information requirements (FFIR) to allow the commander to determine the combat capabilities of his or adjacent friendly units (how I see myself).
- Essential elements of friendly information (EEFI) to allow the commander to determine how he must protect the force from the enemy's information-gathering systems (how can I prevent the enemy force from seeing me).
The CCIR is normally noted in paragraph 3d of the operations order/operations plan (OPORD/OPLAN). Information about friendly activities and status is coordinated through unit SOPs and OPLANs. Information is also acquired using a more general information collection cycle focusing on gathering relevant information from other sources and influences in the MIE. The information needs of the commander are not answered by a single source, but by--
- A combination of his own electronic systems.
- Operational activities such as reconnaissance and security.
- Human intelligence (HUMINT) activities.
- Strategic or national intelligence.
- Interface with local or international police and news media.
Information is perishable and has a temporal quality that is often controlled by a set of dynamic conditions or decisions. Events can make an item of information irrelevant or so unrepresentative as to portray a highly inaccurate picture of reality. Information beyond a certain age will detract from the commander's situational awareness. Standard operating procedures (SOPs), CCIRs, OPLANs, and collection plans must all be sensitive to perishability of information. Moreover, from a technical perspective, INFOSYS managers must respond by managing the systems and information to enable assured, timely communication and decision making.
Use
The commander is able to see his battlespace through the use of space, air, and ground systems to acquire relevant information and provide a current situation. The commander expands his thinking to include all INFOSYS and organizations accessible in the GIE. Once the data is acquired, analyzed, and collated, the information is used to update and validate a common situational awareness. This common situational awareness provides the basis to refine, continue, or adjust decisions, plans, and operations.
- Information is focused and used by issuing guidance, prioritizing assets, and establishing requirements.
- Staffs then refine the guidance into OPLANS or OPORDS. They seek to integrate information at all echelons and plan the use of all available information, regardless of the source.
The most timely, accurate, or relevant information, particularly in operations other than war (OOTW), may come from sources outside the unit or military channels. A unit must make use of both organic and nonorganic INFOSYS. Nonorganic systems are either DOD governmental or non-DOD (GIE). Use of other US Government systems, (DOD and non-DOD) is coordinated with higher commands. Using systems outside the government is more complex. Units can use some services openly and passively, such as listening to, or subscribing to, broadcast media. Units can also make overt use of services such as communications relays or weather forecasting. However, commanders must be aware of the legal and policy limits on their use of any non-DOD INFOSYS.
How the information nets within an organization are linked together can provide multiple conduits for information. Horizontal internetting of INFOSYS at the lowest possible levels provides a deeper, multidimensional picture than traditional, stovepipe reporting.
Protect
While the proliferation of information and information technology can be a great advantage, it is also a potentially significant risk that must be accounted for in every operation. Protection of soldiers and equipment, although not new, has increased in importance in today's information-rich environment. Friendly information and INFOSYS must be protected throughout the battlespace. Operationally, protecting information requires viewing friendly vulnerabilities from the enemy's C2-attack perspective. Commanders must examine the vulnerability of their soldiers and systems to exploitation or attack by an enemy capable of attacking friendly C2 on a wide front by employing EW, destruction, deception, and propaganda.
In order to stop or delay a weapon or system from functioning, an adversary might attack the information or INFOSYS that enable that system. For example, an adversary might introduce a malicious software code through a communications network directly into the Advanced Field Artillery Tactical Data System (AFATDS) to disrupt the sharing and distribution of combat information with other Army and joint C2 systems. Actions taken to protect the capability to operate unconstrained in the MIE battlespace are considered part of C2W (C2-protect).
Information and INFOSYS must be protected at the electronic, physical, and human levels, as described in relationship to the potential threat--all without impeding the overall operation. Security programs that identify threats to C4I systems also take on increased importance while in garrison because the porous and open nature of the GIE makes the C4I information infrastructure vulnerable to attack or exploitation at any time. As part of planning for both battlespace and garrison operations, the signal officer analyzes the unit's information structure to prioritize critical paths, systems, and data for protection. Everything cannot be protected. Therefore, the operations officer must perform a risk management analysis to identify essential information and INFOSYS that must be kept free from disruption or corruption.
Elements of the infrastructure to be protected are data, computers, communications systems, and support facilities. Planners must integrate elements of the GIE into plans to ensure that commanders consider their impact, or potential impact in any operation. Assessment and vulnerability analysis systems must provide the timely and accurate data needed to identify and target threats and potential threats to friendly INFOSYS.
Protecting computer and communications systems from enemy intrusion, disruption, and destruction is an initial basic step in an overall protection approach. However, commanders must also be sensitive to enemy attempts at deception and propaganda. A resourceful enemy may employ propaganda to predispose a commander and his staff toward a specific course of action and then exploit that mindset with a deception operation. IO may often take place under degraded conditions. Besides adversary or accidental actions, natural phenomena may degrade or disrupt equipment or services. Because of the complexity and fragility of INFOSYS, a unit's plans should include procedures for operating without all the information infrastructure.
Exploit
Joint Pub 1-02 describes exploitation as ìtaking full advantage of any information that has come to hand for. . . military operational purposes.î All information environments and systems surrounding an operation, friendly and adversarial, military and nonmilitary, offer chances for exploitation. Generally, exploiting an adversary's INFOSYS is making use of that adversary's INFOSYS data or communications without his knowledge. A flexible approach to exploitation is preferred. The level of exploitation, whether simply monitoring or corrupting data bases, depends on the situation and the desired objective. It may not always mean directly attacking or degrading an adversary's ability to C2. Exploitation involves--
- Reading the adversary's signals.
- Intercepting communications.
- Analyzing signatures.
- Extracting from data bases.
- Establishing the order of battle.
- Taking action to deny, degrade, or manipulate those information capabilities.
Exploitation depends on a thorough understanding of the adversary and the GIE surrounding a potential AO.
Information-gathering and intelligence work must begin in peacetime to establish the analysis of the AO and how potential adversaries operate. Knowledge of the adversary's information infrastructure is as important as knowledge of a potential adversary's strategies, tactics, techniques, and procedures. Knowledge of the adversary's infrastructure will lead to an assessment of personnel, facilities, sensors, processors, and decision-making process. The assessment model asks the question: ìHow reliant is the adversary on the GIE for information?î This in turn affects how the unit (friendly) interacts with the GIE, to include the media, government agencies, NGOs, and foreign governments. Intelligence gained through exploitation supports C2W planning and operations, especially deception, PSYOP, and physical destruction.
Deny
The offensive aspect of IO, C2-attack, makes possible the goal of attacking an adversary simultaneously at all levels with overwhelming force. C2-attack is intended to prevent an adversary from exercising effective C2 of his forces by denying the adversary information or influencing, degrading, or destroying the adversary's information and INFOSYS.
IO gives the commander the means to attack an adversary throughout the depth of the battlespace, far beyond the range of direct or indirect fire systems. The goal is to degrade the adversary's confidence in either his data or his ability to command and control operations. By attacking or confusing his sense of the battlefield, friendly forces gain information dominance and a subsequent relative advantage in applying combat power or controlling a situation in OOTW.
Information denial operations generally require time and occur over relatively large areas. To blind or deafen an adversary requires that most of his major surveillance and reconnaissance systems be influenced or engaged. Therefore, attacks of adversary INFOSYS are normally planned as a series of engagements, contributing to a larger operation or higher objective. These engagements are normally conducted quickly and against a specific target, such as jamming a receiver or using the Army Tactical Missile System (ATACMS) to destroy an adversary's C2 node.
Adversary space-based systems and UAVs pose significant problems. Because of difficulties in locating or engaging these platforms, commanders may be forced to use indirect means, such as camouflage or deception, to counter them. At echelons below corps level, the commander may lack the assets to perform all C2-attack missions, particularly those involving battlefield deception and PSYOP. However, the value in denying an adversary effective command remains important and commanders at all levels need to be prepared to contribute to achieving that objective. Depending on METT-T, the commander might target an element of the adversary's information flow to blind him or prevent effective response. For example, by targeting RISTA, fire direction, or command nets, a commander can limit the effectiveness of an adversary's indirect fire systems.
Commanders must continually assess exploit and deny capabilities to strike an optimum balance that will achieve the greatest payoff in dominating enemy IO. Multiple attack options in IO will result from analysis and assessment of potential targets. Generally, the earlier an adversary's decision-making cycle is disrupted, the greater the effect it can have on his capabilities. It is often more effective to disrupt the adversary's early sensing or decision-making processes rather than trying to disrupt execution of a decision already made. Operational commanders must weigh the relative advantages to be gained by attacking adversary C2 nodes against the potential loss of intelligence from adversary signatures, radiation, or emissions and the need to protect intelligence methods and sources.
Manage
In order to conduct full-dimensional operations, information and INFOSYS require careful coordination and synchronization. With guidance issued, the staff coordinates and integrates information requirements and INFOSYS to synchronize the critical information flow with the operational concept. Management information and INFOSYS must focus on operational requirements that will derive information from reconnaissance, counterreconnaissance, communications, and security operations. Managing information includes managing the electromagnetic spectrum (EMS); deciding what sources and systems to use; ensuring a reliable flow of information between nodes and levels (horizontal and vertical integration); and resolving differences among information from multiple sources.
Operational requirements guide the management of the EMS. The principal functions using the EMS that require planning and control are--
- Communications.
- Intelligence collection.
- Jamming.
- Resolving electromagnetic interference.
This planning must be an integral part of operations planning--in many cases preceding a decision on a scheme of maneuver or fire support and definitely preceding mission execution.
Effective management of information and assets allows information to flow horizontally and vertically across BOSs to enable effective planning, preparation, decision making, and execution. Information should also flow vertically between echelons to enable concurrent planning. This serves to eliminate duplicate efforts and unnecessary redundancy, which allows systems to deal with time-sensitive, relevant information. It also reduces the signature and noise levels of units in the battlespace. The keys to this effective communications and information flow are connectivity, throughput, and resilience. Units can manage connectivity among their organic assets. The difficulty comes in maintaining horizontal and vertical connectivity outside the unit, particularly when dealing with forces using older or different communications and INFOSYS. Connectivity is accomplished through the maintenance of electronic and human links vertically and laterally outside the unit. When dealing with forces or units less technically capable, teams must be prepared to deploy with specialists or liaison personnel equipped with updated equipment.
Resilience is the ability of INFOSYS, from a technical and management perspective, to provide the necessary connectivity and continuity when INFOSYS are degraded. Additionally, Army leaders and planners must understand how military information and systems interconnect and interact with the GIE. Overreliance on commercial systems, particularly satellites and host nation telecommunications networks, may impose restrictions or limitations. Close management and consistent coordination will help assure the availability, reliability, and timeliness of C4I assets.
Operations
Commanders seek to apply overwhelming combat power to achieve victory at minimal cost. They integrate and coordinate a variety of functions with the elements of combat power to sustain it at the operational and tactical levels.FM 100-5C2W, CA, and PA are interrelated operations that are conducted to support the Army objective of achieving information dominance in any operational environment-combat or peace. This chapter discusses each element of C2W and the functions of CA and PA and how they support achieving information dominance. CA and PA operations provide liaison and connectivity with essential actors and influences in the GIE and interact with specific elements of C2W. Grouping C2W, CA, and PA together as specific IO provides a framework to promote synergy and facilitate staff planning and execution. This idea is reinforced by including the CA and PA staff representatives in the IO cell or on the information operations battle staff (IOBS) in routine staff coordination (see Appendix D). This construct conceptually provides for greater integration and synchronization of CA and PA with the more traditional warfighting elements of C2W.
- Joint Pub 3-13.1 states that beyond the five fundamental elements of C2W "other capabilities in practice may be employed as part of C2W to attack and protect." The Army recognizes that C2W is the joint reference point for IO when working with the joint staff and other services in the realm of IW. However, the Army interprets this new paradigm more broadly and recognizes the more comprehensive integration of other information activities as fundamental to all IO; hence the term operations, which includes specifically C2W, CA, and PA.
HISTORICAL PERSPECTIVE
Major emphasis was placed on C2W, CA, and PA activities during Operations Desert Shield and Desert Storm. Commanders integrated OPSEC, military deception, PSYOP, and EW efforts during Desert Shield to pave the way for successful combat operations. During planning for Desert Storm, the senior leadership recognized that Iraq's C2 was a critical vulnerability whose destruction could enable victory with minimal friendly loss. This is evident from the Secretary of Defense's guidance outlining the military objectives for Desert Storm:
- Neutralize the Iraqi national command authority's ability to direct military operations.
- Eject Iraqi armed forces from Kuwait.
- Destroy the Iraqi Republican Guard.
- Destroy Iraqi ballistic missile and nuclear, biological, and chemical warfare capabilities.
- Assist in the restoration of the legitimate government of Kuwait.
During Desert Storm's air operations, the enemy was selectively blinded by EW and physical destruction to mask friendly force movements and operations. Deception operations continued to enforce erroneous enemy perceptions of the CINC's intentions. EW and precision air strikes against C2 targets were used to disorganize and isolate Iraqi forces. When the ground attack commenced, Iraqi forces were close to disintegration, with numerous formations unable to coordinate their efforts. The need for synchronization was an early lesson learned and demonstrated immediate payoffs. Successfully denying Saddam Hussein the ability to command and control his forces substantially reduced casualties on all sides and significantly reduced the time required to achieve coalition objectives.
Fully aware that the enemy, as well as the public at home, was focused on PA coverage of the confrontation, the coalition used that coverage to confuse the enemy by encouraging speculation on the place, time, and size of the impending attack. At the same time, the coalition learned that immediacy of media attention could have unforeseen consequences for its own strategic, operational, and tactical planning. After the cessation of hostilities, CA elements enhanced the restoration of Kuwaiti governmental and social order and responded promptly and effectively to one of the central unanticipated consequences of the war as Iraqi forces created an enormous refugee crisis in the northern Kurdish provinces of Iraq and in southern Turkey.
COMMAND AND CONTROL WARFARE
To be effective, C2W needs to be fully integrated into the commander's concept of the operation and synchronized with other operations. The synchronization of these actions will require rapid and reliable intelligence support and communications. JFCs [joint force commanders] should ensure that the C2W objectives are part of the planning guidance and priorities.Joint Pub 3-0
C2W directly supports the Army goal of achieving information dominance and winning any conflict or succeeding in any OOTW quickly, decisively, and with minimum casualties. C2W incorporates both the sword against anadversary's C2 system and the shield against the C2-attack actions of the adversary. This combination of both offensive and defensive aspects into an integrated capability provides expanded opportunities for synergy in warfare. C2W allows the Army and individual commanders to accomplish missions with fewer risks, in shorter time frames, and with fewer resources.
Role of C2W
C2W applies to all phases of operations, including those before, during, and after actual hostilities. Even in OOTW, C2W offers the military commander lethal and nonlethal means to achieve the assigned mission while deterring war and/or promoting peace. The offensive aspect ofC2W can slow the adversary's operational tempo, disrupt his plans and ability to focus combat power, and influence his estimate of the situation. The defensive aspects of C2W minimize friendly C2 system vulnerabilities and mutual interference. C2W is defined as--
The integrated use of operations security (OPSEC), military deception, psychological operations (PSYOP), electronic warfare (EW), and physical destruction, mutually supported by intelligence, to deny information to, influence, degrade, or destroy adversary C2 capabilities, while protecting friendly C2 capabilities against such actions. Command and control warfare applies across the operational continuum and all levels of conflict.
C2W Elements
The foundation for C2W is robust and redundant command, control, communications, and computer (C4) INFOSYS, coupled with seamless, national-to-tactical, relevant information and intelligence support. The building blocks, or elements, of C2W include-
- OPSEC.
- Military deception.
- PSYOP.
- EW.
- Physical destruction.
Thesebuilding blocks contribute to protection of the force and mission accomplishment in various ways, depending on the situation. This situation dependence leads to the building blocks that are shown in a constantly changing pattern in Figure 3-1. The integrated employment of these five elements leads to synergy on the battlefield and results in the most effective execution ofC2-attack and/or C2-protect tasks. The commander drives this C2W process to achieve agility by focusing attacks on the adversary's ability to command and control his forces while simultaneously protecting friendly C2.
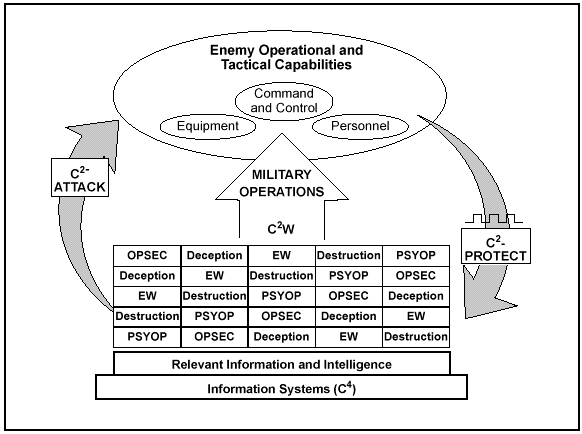
OPERATIONS SECURITY
Operations security is defined as--
A process of identifying critical information and subsequently analyzing friendly actions attendant to military operations and other activities; identifying those actions that can be observed by adversary intelligence systems; determining indicators adversary intelligence systems might obtain that could be interpreted or pieced together to derive critical information in time to be useful to adversaries; and selecting and executing measures that eliminate or reduce to an acceptable level the vulnerabilities of friendly actions to adversary exploitation.
OPSEC is the key to denial. It gives the commander the capability to identify those actions that can be observed by adversary intelligence systems. It can provide an awareness of the potentially friendly indicators that adversary intelligence systems might obtain. Such an awareness could be interpreted or pieced together to derive critical information regarding friendly force dispositions, intent, and/or courses of action that must be protected. The goal of OPSEC is to identify, select, and execute measures that eliminate, or reduce to an acceptable level, indications and other sources of information that may be exploited by an adversary.
OPSEC planning is severely challenged by the new family of global commercial capabilities, to include imaging, positioning, andcellular systems that offer potential adversaries access to an unprecedented level of information against friendly forces. The inevitable presence of the news media during military operations complicates OPSEC. The capability of the media to transmit real-time information to a worldwide audience could be a lucrative source of information to an adversary. OPSEC planners, working closely with PA personnel, must develop the EEFI used to preclude inadvertent public disclosure of critical or sensitive information.
Many different measures impact OPSEC. These includecounterintelligence, information security (INFOSEC), transmission security (TRANSEC), communications security (COMSEC), and signal security (SIGSEC). As more and more of the force is digitized, INFOSEC takes on an ever-growing importance.
MILITARY DECEPTION
Military deception is defined as--
Actions executed to deliberately mislead adversary military decision makers as to friendly military capabilities, intentions, and operations, thereby causing the adversary to take specific actions (or inactions) that will contribute to the accomplishment of the friendly mission.
Military deception is the primary means to influence the adversary commander's decisions through distortion, concealment, and/or falsification of friendly intentions, status, dispositions, capabilities, courses of action, and strengths. The goal of deception is to cause the opposing military commander to act in a manner that serves the friendly commander's objectives.
Historical Perspective
Tactical deception had significant positive impacts on the success of Operation Overlord, and, thus the retaking of the European continent in World War II. Deception worked hand in hand with OPSEC to keep the organization and location of the real Overlord cantonments, training sites, dumps, movements, and embarkations carefully hidden. Unbelievable effort was put into creating mock airfields and ports, phony ships, boats, planes, tanks, vehicles, and troop movements, both real and staged. A new era of deception was introduced-the electronic one. German coastal defense radars were destroyed in a calculated pattern. Deception planners purposely left some intact in the Calais region.
The night the invasion was launched, the Allies began massively jamming German radars with chaff. But they purposely did not completely cover their targets. German radar operators could "see" between Allied jamming curtains. And, what they saw was a ghost fleet of small ships towing barges and blimps headed for Calais at eight knots-or the speed of an amphibious fleet. Powerful electronic emitters received the pulse of the German radar and sent it strongly back to the German receivers. For each repetition of this deception it looked to the German operators like a 10,000-ton ship was out there. The small ships also had the recorded sounds of the amphibious assault at Salerno to play over speakers from 10 miles out. German troops ashore could hear the Allies "getting into their landing craft" for the run into the beach. This information threw German intelligence into chaos for several precious hours and played a major role in delaying German counteractions to the actual invasion taking place at Normandy.
PSYCHOLOGICAL OPERATIONS
Psychological operations are defined as--
Operations to convey selected information and indicators to foreign audiences to influence their emotions, motives, objective reasoning, and, ultimately, the behavior of foreign governments, organizations, groups, and individuals. The purpose of PSYOP is to induce or reinforce foreign attitudes and behavior favorable to the originator's objectives.
PSYOP are based on projection of truth and credible message. PSYOP are an essential tool in both C2-protect and C2-attack operations. The Army has shown considerable strength in applying both PSYOP and deception to military operations. PSYOP can proliferate discrete messages to adversary C4I collectors, enhance joint combat power demonstrations with surrender appeals, and magnify the image of US technological superiority. PSYOP elements must work closely with other C2W elements and PA strategists to maximize the advantage of IO. As an example, the Army has shown considerable strength in applying both PSYOP and deception to military operations.
PSYOP's main objective in C2-protect is to minimize the effects of an adversary's hostile propaganda and disinformation campaign against US forces. Discrediting adversary propaganda or misinformation against the operations of US/coalition forces is critical to maintaining favorable public opinion.
As an early commander of Combined Task Force Provide Comfort, it is my belief that much of the success achieved during Operation Provide Comfort can be attributed to the successful integration of PSYOP in support of the overall humanitarian assistance mission. Over five million PSYOP products were dispersed over northern Iraq and southeastern Turkey in support of the Operation's goals and objectives. PSYOP is a true force multiplier."General John M. Shalikashvili
ELECTRONIC WARFARE
Electronic warfare is defined as--
Any military action involving the use of electromagnetic and directed energy to control the electromagnetic spectrum (EMS) or to attack the enemy. The three major subdivisions within electronic warfare are electronic attack (EA), electronic protection (EP), and electronic warfare support (ES).
Electronic Attack
EA is the use of jamming, electronic deception, or directed energy to
degrade, exploit, or destroy the adversary's use of the EMS. EA can attack
the adversary anywhere-from his tactical formations, back to his national
infrastructure.
Electronic Protection
EP is the protection of the friendly use of the EMS. EP covers the gamut
of personnel, equipment, and facilities. EP is part of survivability. As
an example, self and area protection systems can interfere with the adversary's
target acquisition and engagement systems to prevent destruction of friendly
systems and forces.
Electronic Warfare Support
ES is conflict-related information that involves actions tasked by or
under the direct control of an operational commander to search for, intercept,
identify, and locate sources of intentional and unintentional radiated
electromagnetic energy to detect immediate threats. ES is the embodiment
of combat information and capitalizes on the timeliness of sensor-to-shooter
systems.
PHYSICAL DESTRUCTION
Physical destruction is defined as--
The application of combat power to destroy or neutralize enemy forces and installations. It includes direct and indirect fires from ground, sea, and air forces. Also included are direct actions by special operations forces.
The destruction of a hostile C2 target means that adversary C2 capabilities are degraded for a period of time or, if necessary, permanently shut down. Physical destruction is used only after a full, comparative assessment-strategic-through-tactical perspectives-of the trade-offs between preserving the target versus its destruction.
Historical Perspective
On April 14, 1943, US intelligence experts intercepted and decoded a message revealing that Admiral Isoroku Yamamoto, Commander-in-Chief of Japan's Navy, would be flying to Bougainville in four days. When analysis determined that Bougainville lay just within the extended range of US P-38 fighters at Henderson Field on Guadalcanal, Allied planners recognized the opportunity to strike at the heart of Japanese command and control and strategic planning in the Pacific.
In less than 48 hours, Admiral Chester W. Nimitz's forces planned and coordinated an operation to shoot down Yamamoto's plane and obtained approval from Secretary of the Navy Frank Knox and President Roosevelt.
Yamamoto was known to be invariably punctual, and American planners were confident that his plane would appear over Bougainville on schedule-9:39 am, April 18. At that moment, 16 carefully positioned P-38s from Henderson Field spotted the two Japanese Betty bombers of Yamamoto's party and attacked.
Both aircraft were quickly sent plummeting to the ground, completing a classic information operation that took less than four days from start to finish and rendered irreparable damage to Japanese command and control. The Japanese would feel the impact of this single mission throughout the remainder of the war.
C2W Disciplines
The two disciplines that comprise C2W are C2-attack and C2-protect.
C2-ATTACK
- C2-attack is defined as--
- The synchronized execution of actions taken to accomplish established objectives that prevent effective C2 of adversarial forces by denying information to, by influencing, by degrading, or by destroying the adversary C2 system.
C2-Attack Principles
- The three principles of C2-attack are to-
- Plan based on the unit's mission, commander's intent, and concept of operations.
- Synchronize with and support the commander's plan.
- Take and hold the initiative by degrading the adversary's INFOSYS and forcing the adversary to be reactive. Reactive means that C2-attack slows the adversary's tempo, disrupts the adversary's planning and decision cycles, disrupts the adversary commander's ability to generate combat power, and degrades the adversary commander's means for executing mission orders and controlling subordinate unit operations.
Figures 3-2 and 3-3 illustrate some of the potential relationships between the elements of C2W.
C2-Attack Effects
In general terms, C2-attack has four effects that focus on the adversary's C2 infrastructure and information flow to produce a lower quality and slower decision-making process.
- First, the adversary is denied information by disrupting his observation, degrading his orientation and decision formulation, and degrading information collection. Information collection can be degraded by destroying collection means, by influencing the information the adversary gets, or by causing the adversary not to collect at all.
- Second, the adversary commander is influenced by manipulating perception and causing disorientation of his decision cycle.
- Third, adversary IO are degraded by selectively disrupting C4I systems.
- Fourth, adversary information capabilities can be neutralized or destroyed by physical destruction of nodes and links. Destruction operations are most effective when timed to occur just before the adversary needs a certain C2 function or when focused on a target that is resource-intensive and hard to reconstitute.
Historical Perspective
Heraclitus of Ephesus in sixth century BC noted that "if you do not expect the unexpected, you will not find it." During the German invasion of the Soviet Union in June 1941, the Germans recognized, but the Russians did not, exploitable deficiencies in the existing Soviet C2 system. Employing the tools of C2W in an interrelated fashion, the Germans were able to effectively disrupt, exploit, and destroy the Soviet C2 system. Using weapons specifically built for C2W, the Germans attacked elements of the Soviet system by air, artillery, and sabotage. The results of these attacks were startling. Due to cross-border German sabotage efforts, many of the Soviet units "did not receive the war alert order when it was issued [from Moscow] on the night of 20-21 June 1941." By 24 June, large gaps had already been torn in the Soviet communications network, thus forcing commanders to rely on easily exploitable, unprotected, radio networks. This, in turn, led to the successful targeting of exposed command posts and associated units throughout the theater. These attacks, because of their effectiveness, led Soviet commanders to prohibit the use of radios because they might give positions away. Using C2W, the Germans had effectively shut down the Soviet C2 system, creating an operational environment that quickly led to a general collapse of the entire eastern front.
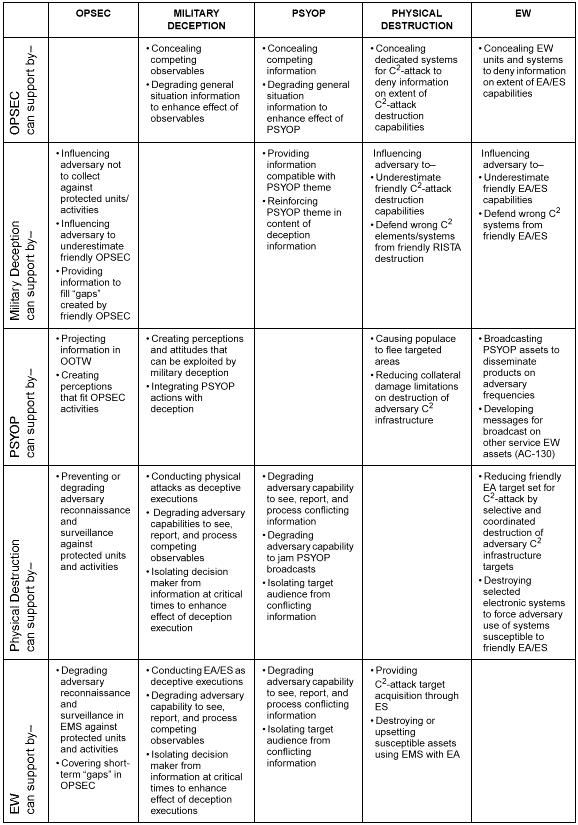
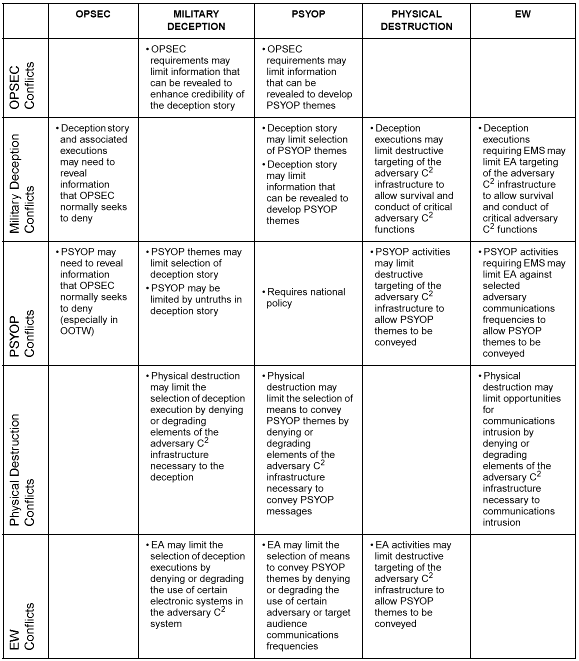
C2-PROTECT
- C2-protect is defined as--
- The maintenance of effective C2 of ones own forces by turning to friendly advantage or negating adversary efforts to deny information to, to influence, to degrade, or to destroy the friendly C2 system.
C2-protect can be offensive or defensive. Offensive C2-protect uses the five elements of C2W to reduce the adversary's ability to conduct C2-attack. Defensive C2-protect reduces friendly C2 vulnerabilities to adversary C2-attack by employing adequate physical, electronic, and intelligence protection.
C2-Protect Principles
The C2-protect process can best be understood by reverse engineering our C2-attack process. Commanders ask how the adversary can employ destruction, EW, military deception, OPSEC, and PSYOP to disrupt our C2 systems and decision-making process. Having wargamed the adversary's C2-attack courses of action, the commander can develop a comprehensive protect operation, synchronized with the main effort and C2-attack. The commander is guided by the five principles of C2-protect.
- To gain C2 superiority. This principle includes functions such as the unimpeded friendly processing of information, accurate development of courses of action, valid decision making, and efficient communications to and from subordinates.
- To stay inside the adversary's decision cycle. This is done by denying, influencing, degrading, and/or destroying the adversary's C2 personnel, equipment, and systems.
- To reduce the adversary's ability to conduct C2-attack.
- To reduce friendly C2 vulnerabilities using C2-protect measures. As an example, countering the effects of adversary propaganda or misinformation through PSYOP and PA.
- To reduce friendly interference in our C2 systems throughout the EMS (deconfliction and coordination).
Historical Perspective
The history of the Information Age is being made now. In 1988 we saw the first well-publicized case of a computer virus. This insidious, self-replicating virus known as the Internet Worm penetrated the computer system at the University of California at Berkeley, corrupting thousands of computers on the internet. A computer emergency response team (CERT) had been created at Carnegie Mellon University. In 1993 they had their first large event as they put out a warning to network administrators that a band of intruders had stolen tens of thousands of internet passwords.
When CERT began in the late 1980s, they processed less than 50 events per year. Now they are in the thousands per year. The military is a target of this attack. Recent stories have told of a 16-year-old who compromised the security of more than 30 military systems and more than 100 other systems before he was caught after a 26-day international electronic manhunt. This experience hints at the impact a professional, well-financed effort could have against computer nets. The lesson this evolving history is showing us vividly today is that the information highway is creating a great vulnerability to US forces. We are all familiar with the security of transmitting information over a radio or telephone. But there is an even greater weak spot now in computers, data bases, software (such as decision-making aids and tools), servers, routers, and switches. This vulnerability exists today and is growing in geometric proportions.
C2-Protect Effects
The effects of C2-protect mirror those of C2-attack. We can deny information the adversary needs to take effective action. We can influence the adversary not to take action, to take the wrong action, or to take action at the wrong time. We can degrade and destroy his capabilities to perform C2-attack against friendly forces. PSYOP and PA supports C2-protect. PSYOP can drive a wedge between the adversary leadership and its populace to undermine the adversary leadership's confidence and effectiveness. The Commander's Internal Information Program (formerly the Command Information Program), publicized by the PAO, can be extremely beneficial in countering adversary propaganda in the US and among the deployed forces. PA specialists, working with PSYOP and intelligence personnel, can also develop information products that commanders can use to help protect soldiers against the effects of adversary disinformation or misinformation.
CIVIL AFFAIRS OPERATIONS
CA activities encompass the relationship between military forces, civil authorities, and people in a friendly or foreign country or area. CA activities support national policy and implement US national objectives by coordinating with, influencing, developing, or controlling indigenous infrastructures in operational areas. CA secures local acceptance of and support for US forces. CA is important to gain information dominance because of its ability to interface with key organizations and individuals in the GIE; for example, CA's traditional relationship with NGOs and PVOs such as the International Committee of the Red Cross.
Commanders fully integrate civil-military operations (CMO) into all operations and use CMO to influence, coordinate, control, or develop civilian activities and civil organizations. CA activities play a command support role in all operational environments and across the operational continuum. However, CA operations are most common when supporting the lower end of the operational spectrum.
Functional Specialties
Many CA activities require specific civilian skills. CA activities most relevant to the GIE and supporting IO are categorized into four major sections:
GOVERNMENT SECTION
Public administration provides liaison to the civilian government.
ECONOMIC SECTION
Economics and commerce monitors government economic and commercial agencies,
normally only in a civil administration mission.
PUBLIC FACILITIES SECTION
Public communications allocates civilian communications resources for
civilian and military use and directs civil communications agencies as required,
normally only in a civil administration mission.
SPECIAL FUNCTIONS SECTION
Civil information advises, assists, supervises, controls, or operates
civil information agencies and provides TV, radio, or newspaper services.
Collection Activities
The nature of CA activities and the need for CA personnel to develop and maintain a close relationship with the civilian populace puts them in a favorable position to collect information. CA information collection activities encompass the complete spectrum of cultural, social, political, and economic issues within the present or potential area of operations. In their daily operations, CA personnel deal with people, equipment, and documents that are prime sources of information. Information collected is often important to other units' staff sections or agencies and supports the CCIR.
Information Sources
CA units are included in the information collection plan of the supported unit. CA units report information that meets the criteria of the supported unit's collection plan. Prime sources of information available to CA units include, but are not limited to-
- Civilians who were housed with, catered to, or associated with enemy personnel.
- Dislocated civilians and other personnel participating in movement control, relief, or other assistance (normally referred to appropriate intelligence personnel).
- Government documents, libraries, or archives.
- Files of newspapers or periodicals.
- Industrial and commercial records.
- Technical equipment, blueprints, plans, or information of interest related to transportation, signal, engineer, and medical fields.
Relationships
The information collected can supplement the intelligence effort. US forces need timely and accurate information and intelligence to plan missions, secure the element of surprise, identify and develop targets, and protect US interests across the operational continuum. CA activities are closely tied to the intelligence functions and operations associated with the overall tactical mission.
CA personnel are not, and must not have the appearance of being, intelligence agents. The mission of the unit drives the intelligence cycle. As operational planning begins, so does intelligence planning. Requirements for operational planning are normally for finished intelligence studies, estimates, or briefings. CA planners prepare their estimates from basic intelligence documents that are not primarily written for CA use, such as an area study. Intelligence is the product resulting from the collection, evaluation, and processing of information.
Overall, CA elements collect information that the G2/J2 turns into intelligence. CA forces, if used correctly, can complement theintelligence collection process, especially HUMINT. In some cases, CA elements can also enhance the capabilities of technical intelligence (TECHINT) or intelligence concerning foreign technological development that may have eventual application for military use.
Coordination and Support
All CA activities require close coordination with military forces, US and foreign government agencies, and nonmilitary agencies with a vested interest in military operations. CA planners must consider all available support to ensure successful completion of the CA mission. In most cases, CA planners directly or indirectly support the agencies assigned by law to carry out national policy. CA planning is a command responsibility. It must be coordinated, at a minimum, with all other staff planners. To ensure success, coordination and cooperation with the following are vital to the conduct of all operations: other US staffs and units, host nation military, coalition military, US Government, foreign governments, international agencies, PVOs, and NGOs.
GOVERNMENT AGENCIES
Effective CA activities require close contact between the US military, the Department of State (DOS), and other US Government agencies. Because DOS formulates and implements foreign policy, it has a vested interest in CA activities. In the area of CA, DOS has primary or joint responsibility with DOD for policy. Some examples are matters involving PSYOP, PA, CA, civil information, or other measures to influence the attitude of the populace and plans for turning CA activities over to civilian control at the end of hostilities.
PVOs AND NGOs
The list of PVOs and NGOs that may be found in an AO could be very large. Approximately 350 agencies capable of conducting some form of humanitarian relief operation are registered with the USAID. Commanders must consider the presence and capabilities of PVOs and NGOs and, when appropriate, coordinate and cooperate with their efforts. Because many of these organizations may have been established in the AO in advance of the Army's presence, they may be a good source of information and knowledge.
CA, PSYOP, AND PA ELEMENTS
CA, PSYOP, and PA elements are able to use the same communications media with essentially the same messages but to different audiences. CA and PSYOP personnel address local populations and enemy forces, respectively, while PA personnel address US forces and national and international news media. Popular American public support contributes to the success of CA. CA and PSYOP personnel provide news and information to the local populace on the effects of combat operations.
CIVIL-MILITARY OPERATIONS CENTER
Commanders can establish a CMOC to perform liaison and coordination between the military PVOs and NGOs, as well as other agencies and local authorities. Figure 3-4 illustrates additional GIE players that may interact with the CMOC. Relationships with nonmilitary agencies are based on mutual respect, communication, and standardization of support. NGOs and PVOs have valid missions and concerns, which at times may complicate the mission of US forces. As an example, liaison with an organization that is caring for the sick and injured of the local populace may reveal that human rights abuses are occurring. This information could provoke a response by DOS officials to warn local authorities to stop such abuse from happening, as well as increasing the level of protection for the local population by US forces.
STAFF
CA operations must be integrated into the battle plan, to include providing for timely and accurate reporting of the operation and combating distorted or disinformation disseminated by the adversary. The CA representative to the IOBS-
- Represents CA concerns in IO.
- Coordinates with PA and PSYOP representatives to ensure consistency of messages and OPSEC without compromising CA credibility.
- Prepares CA estimates, assessments, and the annex to the OPLAN/OPORD to identify and integrate CA support.
- Coordinates the use of local resources, facilities, and support. Examples include civilian labor, transportation, communications, maintenance, or medical facilities, and miscellaneous services and supplies.
- Provides liaison to local agencies and civilian authorities.
- Advises on cultural and moral considerations.
In concert with the G2/J2 and chief of staff, the CA staff officer (G5/J5) controls, coordinates, and integrates the CA effort at each echelon. One essential function is to prepare and issue a CA annex as part of the unit's OPORDs or OPLANs. See Appendix A, Annex A.
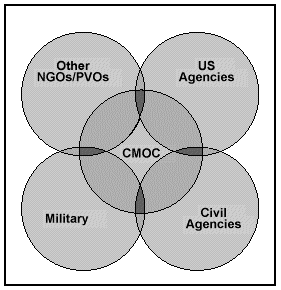
Historical Perspective
In the early spring of 1991, in the aftermath of its humiliating defeat at the hands of US-led coalition forces, the Iraqi Army launched a violent attack against the Kurdish minority in northern Iraq. More than half a million refugees fled across the border into southeastern Turkey. Huddling on exposed mountainsides, they promptly began to become ill and die from starvation, exposure to the bitter cold, and various diseases. The world press reported that over a thousand Kurds, especially children and the elderly, were dying each day.
On April 5, President Bush directed US military forces to "stop the dying." Lieutenant General John M. Shalikashvili, then deputy commander of US Army Europe, was placed in command of the coalition task force Provide Comfort. Elements of several CA units, active and reserve, were redeployed from the Persian Gulf or deployed from Fort Bragg to Turkey under the 353d Civil Affairs Command (USAR), Bronx, New York.
In Turkey, the CA soldiers joined with 10th Special Forces Group to aid overwhelmed relief workers already on the scene. The latter included personnel from the United Nations High Commissioner for Refugees, the US Department of State Office of Foreign Disaster Relief, the Turkish Red Crescent, and more than 40 different civilian humanitarian relief organizations, all of which were attempting to care for the Kurds in 40 or more scattered locations. Shalikashvili's greatest problem became coordinating all the organizations' efforts with the US Air Force-the primary means for transporting emergency supplies into the region.
At US European Command Headquarters in Stuttgart, Germany, an Army Reserve CA captain with the 353d saw a possible solution. The captain, a software engineer in civilian life, joined with three other CA reservists in an intensive three-week effort, first in Stuttgart and later at Incirlik Air Base, Turkey, to design and implement a unique relief supply data base. Their program, later named the Disaster Assistance Logistics Information System (DALIS), combined key data from agencies on the type of aid arriving, storage locations, and intended destinations. DALIS allowed planners to coordinate efforts and deliver the right supplies to the right locations at the right time. These innovative soldiers used the power of the microprocessor to unscramble what threatened to be a logistical, diplomatic, and humanitarian nightmare. By combining data from multiple sources, they provided vital information that reduced redundancy and avoided maldistribution of resources at a critical moment, saving thousands of lives. Using IO, CA soldiers became masters of the situation and made a decisive contribution to the success of Provide Comfort.
PUBLIC AFFAIRS OPERATIONS
Public affairs must be integrated with other battlefield functions to achieve the desired effect of an accurate, balanced, credible presentation of information that leads to confidence in force and the operationFM 46-1
PA fulfills the commander's obligation to keep the American people and the soldiers informed. PA operations help establish the conditions that lead to confidence in America's Army and its readiness to conduct operations. Army operations are of interest to the public and subject to being covered by the media. PA is therefore a function that supports both combat and noncombat operations and contributes to success in war and other military operations.
Missions
The inherent challenge is for commanders to understand the dynamics of media coverage. The media can potentially have a quick and pervasive impact on their plans and operations. Its coverage of the development of plans and the conduct of operations may impact and influence strategic decisions in a more profound and immediate way than in the past. PA operations enable commanders to effectively operate with the media. Commanders must also have a better appreciation for the immediacy of media coverage such as personal interviews, live versus taped reports, film versus written dispatches, methods of transmission, and so on.
The commander's information needs are not answered by a single source, but by a combination of many systems and functions, including the news media. The advances in information technology provide potential adversaries with the capability to exploit (deny, distort, degrade, or destroy) information. The PAO must have the capability to monitor the national and international media and identify and assess information relevant to the operation.
The missions of PA, PSYOP, and CA involve communicating information to critical audiences to influence their understanding and perception of the operation. Information communication must be fully coordinated to eliminate unnecessary duplication of effort and ensure unity of purpose. Planning for these operations must be synchronized, and the messages they communicate must be truthful and mutually supportive to ensure that credibility is not undermined and mission success is achieved.
The PAO's support to the commander is multidimensional. The PAO advises the commander on media relations and the PA implications of current and future operations and events. He serves as the official command spokesperson and implements the Commander's Internal Information Program. PA focuses on achieving an accurate, balanced, and credible presentation of timely information that communicates the commanders perspective to enhance confidence in the force and the operation. It provides the critical battlefield function of media facilitation by serving as the interface between the media and the force.
With the broad scope and initiative given to soldiers and units today at every level, one of the primary tools the commander uses is the internal information program. Well-informed soldiers are likely to have higher morale and perform better. Soldiers need and want information from both external and internal sources and are interested in the public perception of an operation. Therefore, PA operations use various communication methods and channels to make this information available to soldiers, other Army audiences, and external audiences. The broad range of missions the Army executes today are done in an environment of global visibility. Media coverage can be pivotal to the success of the operation and achieving national strategic goals.
Impact of Change
Every aspect of every operation may be an issue of interest to the media and consequently to the public. Existing and emerging technology puts military operations onto the global stage, often in real time. Soldier actions can induce public reactions, which in turn causes NCA reactions that impact operations without ever engaging US forces. For example, real-time or near real-time reports of the actions of a soldier manning a roadblock, the results of a minor skirmish, or the effects of a major combat action become the subject of discussion. Media personalities, politicians, pundits, critics, academics, and the general public rapidly form positions and opinions, often in pursuit of agendas well beyond the scope and purpose of the operation being reported. They become active participants in the international public debate of events and issues.
Adversaries can also attack the public opinion center of gravity and affect operations without ever engaging US forces. All Army operations can be influenced through planned or inadvertent messages communicated via the GIE. PA and the associated GIE addresses simultaneous effects that are integral to all levels of war (Figure 3-5). In the Information Age, the old separation of public information and internal information activities are compressed.
Providing accurate, timely news, information, and entertainment reduces distractions, rumors, fear, and confusion that could cause stress and undermine efficient operations. Such activities contribute to team building, morale, and unit cohesion. They enhance soldier confidence and understanding. They contribute to ethical behavior, respect for the law of war, private property, the rights of civilians and noncombatants, and human dignity.
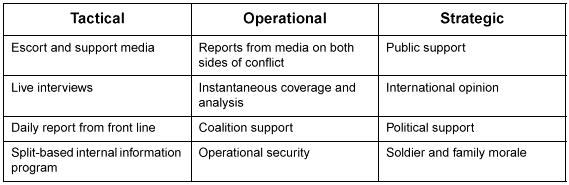
Coordination and Support
PA is a battlefield function and has a direct impact on the conduct of operations. It must be fully integrated into the planning process at all levels and across the full continuum of operations. A member of the PA staff serves on the IOBS (see Appendix D). The PA representative assesses media presence, capabilities, information needs and interests, and content analysis of both traditional media and electronic forums such as those on the internet and electronic bulletin board.
Finally, PA operations must be integrated into the battle plan, to include providing for the timely and accurate reporting of the operation, combating distorted or disinformation disseminated by the adversary. The PA representative to the IOBS-
- Represents PA concerns in IO.
- Identifies, assesses, and advises the commander on information and issues with PA implications.
- Reviews strategic and operational information with PA implications such as events, missions, and propaganda.
- Coordinates with CA and PSYOP representatives to ensure consistency of messages and OPSEC without compromising PA credibility.
- Facilitates availability of battlefield information for PA purposes, for example, releasable visual imagery used to inform the public of Army capabilities and accomplishments.
PA is integrated into the OPLAN/OPORD through the PA Annex.
Appendix A, Annex A provides
the information to implement PA media facilitation, news, information provisions,
and force training operations. This annex is coordinated with all staff agencies,
especially those that significantly impact the information environment, that
is, PSYOP, CA, signal, military intelligence, to ensure that PA activities
are synchronized with other activities.
Historical Perspective
At 1800 hours local (Riyadh) on 27 February 1991, the Gulf War CINCCENT and ARCENT commanders agreed that in all likelihood no more than 24 hours of battle remained. At 2100 hours during a briefing for the press corps telecast live around the world, the CINCCENT reflected that opinion and indicated that coalition forces would be pleased to stop fighting when so ordered. The time of the briefing in CONUS (1300 hours EST) ensured a wide audience, including the President of the United States, for at least a portion. Reacting to the briefing, the President and the Chairman of the Joint Chiefs of Staff (CJCS) conferred, and the CJCS called Riyadh from the Oval Office, indicating the President's wish to stop the offensive as soon as practicable. The CINC called his component commanders, stating that the NCA was considering a cease-fire at 0500 (local) on 28 February.
Meanwhile, VII Corps had prepared a double envelopment movement, passing 1st Cavalry Division around to the north of 1st Armored Division, to crush what remained of the Iraqi Republican Guard. The corps intended to execute the double envelopment beginning at 0500 on the 28th. In accordance with an ARCENT warning order concerning the cease-fire, however, VII Corps units assumed a local security posture, focusing on force protection. An ARCENT frag order, published at 0200 and titled "Potential Temporary Cease-Fire," reiterated the 0500 implementation time.
At 0300, CENTCOM notified ARCENT that the President had set 1200 am eastern standard time on 28 February (0800 hours local) as the beginning of the cease-fire time and urged the Army component to inflict the greatest possible damage on the enemy before that hour. Accordingly, ARCENT published a new FRAG order at 0330, calling for the resumption of offensive operations. At 0406, the VII Corps commander ordered his division commanders to execute the double envelopment with a new departure time of 0600, being mindful of the 0800 cease-fire. Difficulties inherent in reordering battle and executing the mission for maximum gain over the next four hours led to confused communications, misunderstood commander's intent, and postwar questions over operational and tactical execution.
In the space of 11 hours, a press conference that included unguarded opinions
about the past and future course of a war profoundly affected the strategic,
operational, and tactical levels of that war. Commanders on the front lines
were neither informed nor consulted on the intent of the public briefing,
either before or after it had taken place. The ubiquitousness and immediacy
of press reportage effectively erased boundaries between national and theater
command authorities and dramatically compressed the time between strategic
decision and operational consequences.
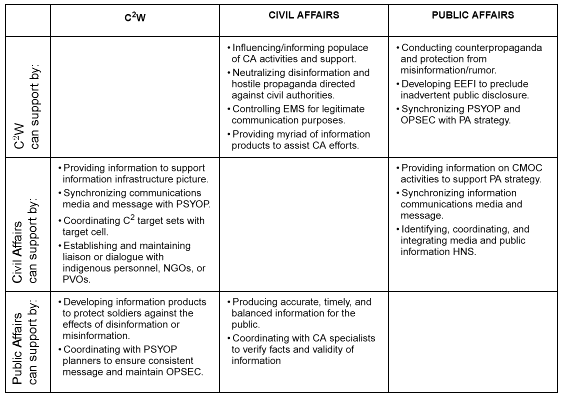
Relevant Information and Intelligence
In modern battle, the magnitude of available information challenges leaders at all levels. Ultimately, they must assimilate thousands of bits of information to visualize the battlefield, assess the situation, and direct the military action required to achieve victory.FM 100-5This chapter sets the doctrinal foundation for the role of relevant information and intelligence in IO. The chapter discusses the need for relevant information, the criteria to carefully assess such information, and the commander's decision and execution cycle. It also includes information on the role of intelligence in framing relevant information about the adversary.
RELEVANT INFORMATION
Relevant information is defined as--Information drawn from the military information environment that significantly impacts, contributes to, or is related to the execution of the operational mission at hand.
Relevant information has a direct relationship with the MIE in two important ways:
- One, the act of collecting, processing, or disseminating relevant information serves as the principal criteria a commander applies, to include an individual, organization, or system as part of the MIE.
- Two, it is the product or medium drawn from or used by those same players that serves as the basis or currency of IO. See Figure 4-1.
In the past the Army has tended to approach the collection and use of operational information from a specialized perspective. For example, different BOS elements have collected and used information necessary to support their particular functions, such as--
- Intelligence focused upon information about the adversary and foreign nations.
- Operators focused on situational information concerning friendly forces.
- Logisticians focused on friendly force sustainment conditions and requirements.
- PA and CA focused on the interface between military and nonmilitary sectors.
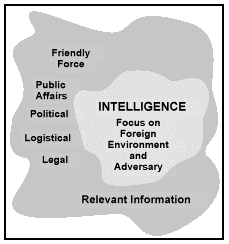
Only a limited amount of such information was shared and that at relatively high levels within the military organizational hierarchy. Information flowed up and down stovepipes with routines that tended to slow the sharing of information across organizational boundaries. Relatively little effort was focused upon the systematic integration or synchronization of information. Normally, numerous specialized, noninteractive data bases were developed and maintained to meet the needs of particular elements on the battlefield.
Because of changes in the information and operational environments, we can now achieve new levels of efficiency and effectiveness in use of information by integrating and synchronizing the collection, processing, and dissemination efforts. Efforts must focus on leveraging the potential operational contribution of information by efficiently collecting and sharing information across all BOS elements.
Assessment Criteria
Because sources of information are imperfect and susceptible to distortion and deception, commanders and planners must carefully assess the quality of the information prior to its use. They can do so using the following six criteria:
- Accuracy. Information that conveys the true situation.
- Relevance. Information that applies to the mission, task, or situation at hand.
- Timeliness. Information that is available in time to make decisions.
- Usability. Information that is in common, easily understood formats and displays.
- Completeness. All necessary information required by the decision maker.
- Precision. Information that has the required level of detail.
As a first priority, information should be accurate and relevant. As a second priority, it should be both timely and in usable form. Finally, information should be as complete and precise as possible. The following rule of thumb supports these relationships: incomplete or imprecise information is better than none at all; untimely or unusable information is the same as none at all; inaccurate or irrelevant information is worse than none at all.
Decision and Execution Cycle
Commanders must have information to command. Information is the medium that allows the commander's decision and execution cycle to function. Information gives direction to actions by the force, provides courses of action for protecting the force, and helps the force accomplish its operational mission. Relevant information drawn from the MIE supports the creation of situational awareness that contributes directly to effective C2 during all stages of the decision and execution cycle. C2 in an environment of situational awareness helps the commander ensure unity of effort toward mission accomplishment. Ultimately, C2 depends on the right person having the right information at the right time.
C2 is a continuous, cyclical process by which a commander makes decisions and exercises authority over his forces to accomplish an assigned mission. A commander's decision and execution cycle has four sequential steps (see Figure 4-2).
-
Step 1. First, the commander is the central element in the entire
process of C2. Accordingly, he strives to understand his current situation
and environment by acquiring information about his battlespace and the status
of relevant forces, both friendly and adversary, using all available sources,
including personal observation, sensors, INFOSYS, and spot reports from
subordinates.
-
Step 2. Upon mission receipt, the commander combines his understanding
of his current environment, visualizes the desired future end state, and
develops an initial concept of how to execute the mission.
-
Step 3. Based on his understanding of the situation and his intent,
the commander issues guidance and directs a planning process to develop and
refine a viable course of action for mission accomplishment. Upon deciding
on a course of action, he disseminates his orders to put the operation into
motion. During this execution phase, the commander monitors the operation
and gauges its results. This brings him full circle to acquire new or additional
information from which he begins the cycle again. Throughout the entire cycle,
the fog and friction of war continually affect the commander's ability to
acquire information, visualize, plan, decide, and execute.
- Step 4. Since the decision and execution cycle is a continuous process, all parts of the cycle are active at each echelon of command. Commanders collect information, develop situational awareness, and plan for future operations at the same time they conduct current operations. Meanwhile, senior and subordinate commanders gather information and work through decision and execution cycles at their respective levels. Maintaining rapid decision and execution cycles--and thus a rapid tempo of operations--requires that seniors and subordinates alike have an accurate, common picture of the battlespace. From this common picture, a unit gains greater situational awareness with which to exercise initiative during combat or other situations.
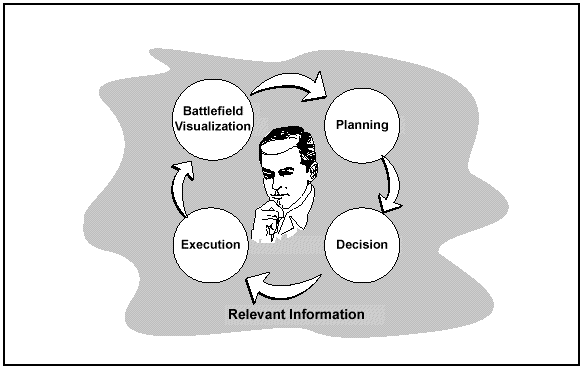
The commander operates within the GIE, adjusting his MIE to enhance his situational awareness as necessary. Moreover, the commander uses his various means in the MIE to ensure that all elements of his force have a common, complete, and relevant situational awareness. This requires a sophisticated INFOSYS that enhances the commander's ability to share, manage, and move information among organizations. The commander also uses his information capabilities to support OOTW. The emphasis during such missions shifts away from the combat focus of C2W operations and starts to take in broader considerations contributing to efficient and effective operations. These operations often involve a variety of GIE players. For example, the G3/J3 works closely with PA and CA officers, among others, to determine critical information requirements pertaining to his AO.
INTELLIGENCE
Intelligence is--The product resulting from the collection, processing, integration, analysis, evaluation, and interpretation of available information concerning foreign countries or areas. Also, information and knowledge about an adversary obtained through observation, investigation, analysis, or understanding.
Joint Pub 1-02
Intelligence is also the critical subelement of relevant information that focuses primarily upon foreign environments and the adversary. In support of friendly operations, intelligence helps produce a common, current, and relevant picture of the battlespace that reduces uncertainty and shortens the commander's decision-making process. Against an adversary, intelligence is vital for developing and executing effective C2W operations that degrade and distort the enemy's decision-making process while protecting friendly C2. Intelligence support to IW executed at the strategic and national levels must be leveraged to support C2W and IO conducted at the operational and tactical levels. This effort requires a seamless intelligence-collection process and supporting architecture, providing real-time intelligence products focused on CCIR.
Role of Intelligence
Intelligence provides the commander with an accurate understanding of the threat situation as it relates to current and future operations. Intelligence personnel acquire, use, manage, and exploit information to produce such an understanding. For common situational awareness to be accurate and current, the intelligence effort is continuous. Intelligence collection includes all possible sources, from national-level covert operations through local open sources such as news media, commercial world contacts, academia, and local nationals.
In noncombat operations, HUMINT, open sources, and other government agencies provide timely information to augment the unit's more traditional battle-focused intelligence-collection effort. The intelligence effort provides current, accurate threat and targeting data to weapon systems and intelligence sensors. Their effectiveness is dependent upon the rapid movement of data between collector, processor, decision maker, and shooter. Intelligence supports C2W, focusing on C2-attack and C2-protect.
Intelligence-Enabling Functions
The primary purpose of intelligence is to enable well-informed operational decisions based on an accurate understanding of the situation. The essence of intelligence is to collect, analyze, screen, and present information requested by the commander. Intelligence helps reduce uncertainty for the commander by screening out information that is not relevant to his decision-making process. Intelligence-enabling functions focus on assessing friendly vulnerabilities, understanding the adversary, employing IPB, and assessing battle damages.
ASSESSING FRIENDLY VULNERABILITIES
The first critical step in protecting IO capabilities is to identify specific and potential threats. Potential threats range from the adversary's direct overt and covert actions, to individuals and organizations seeking to exploit military INFOSYS, to natural phenomena. They include a new family of global commercial imaging, cellular telephone, and positioning systems that jointly or separately provide a potential adversary with near real-time information on forces and movements.
The fluid, porous nature of the MIE makes it difficult to protect INFOSYS from possible attacks. Therefore, intelligence provides the commander the necessary information to conduct risk assessments and develop risk management options to protect vital C2 components and capabilities. The risk assessment is based on identification of such factors as specific threat capabilities, technical capabilities, doctrine, and past performance of the threat force. The risk assessment is not a finished document, but a continuous process that is constantly updated to reflect changes in the operating environment, technology, and threat acquisitions. Because C2W offers potential adversaries the chance to strike at the supporting infrastructure of the US force--wherever it is located--the commander and his staff must be aware of threats to their INFOSYS at the home station.
UNDERSTANDING THE ADVERSARY
The effectiveness of C2-attack is predicated on a thorough understanding of an adversary, his C2 system, and his decision-making process. The deeper the understanding, coupled with the tools and techniques to take advantage of such knowledge, the more effective the exploitation of the potential adversary. At all levels of war, intelligence is an operational tool that identifies, assesses, and exploits the enemy's information and C2 systems. Data is required on what information the adversary collects, by what means, what reliability he places on various sources, and how that data is evaluated.
Intelligence personnel must be able to describe the enemy's decision-making process and how direction is sent to subordinates. Detailed intelligence is required on the social and cultural environments and the psychological makeup of the adversary's key leaders and decision makers. How they interact and perceive one another are important aspects of the information necessary to develop effective PSYOP and deception operations. How subordinates execute decisions completes the picture. Having a detailed understanding of the adversary's use of information is necessary in order to determine where and how to effectively influence his actions (see Figure 4-3).
"Know the enemy and know yourself, and you will be victorious."Sun Tzu (500 BC)
EMPLOYING INTELLIGENCE-PREPARATION-OF-THE-BATTLEFIELD
In this context, IPB is the continuous process used to develop a detailed knowledge of the adversary's INFOSYS. IPB is a continuous process of overlapping and simultaneous actions that produces situation updates on a continuous basis and providing options to the commander. This form of information IPB, as shown in Figure 4-4, is the basis for planning operations, developing C2W courses of action, and targeting. The process builds upon the standard IPB but also requires--
- An understanding of the adversary's decision-making process and leadership style.
- Knowledge of the technical requirements on a wide array of INFOSYS.
- Knowledge of the political, social, and cultural influences at work in the MIE.
- The ability to conduct highly technical processes to produce C2W course-of-action templates.
- Identification of and an in-depth understanding of the biographical background of the adversary's key leaders, decision makers, communicators, and advisors.
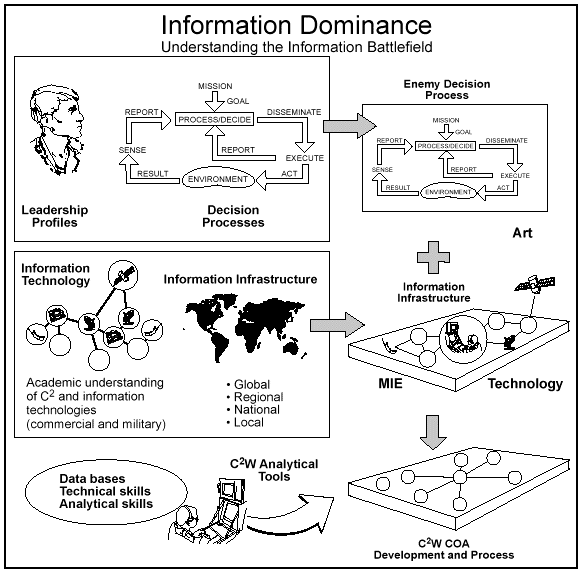
Much of this information should be routinely collected and maintained in national-level data bases and be readily available at the start of a mission.
The IPB actions the intelligence officer accomplishes to support IO include constructing a template of the adversary decision-making process, understanding the information infrastructure of the adversary, and analyzing the adversary's vulnerabilities.
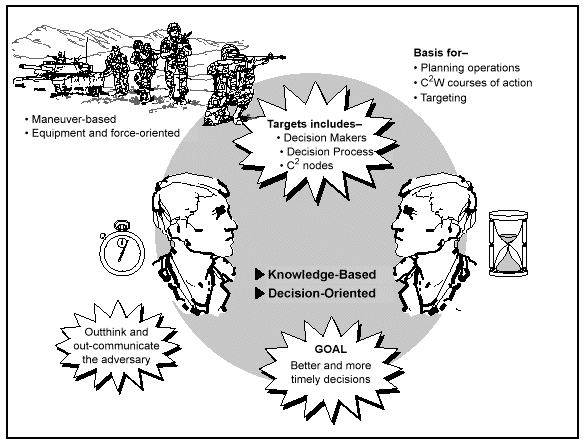
Constructing a Decision-Making Template
The first step in the IPB process is to construct a template of the adversary's decision-making process. This aspect of information IPB focuses on developing an understanding of the leadership/personality profiles of the critical adversary decision makers. It address how they use information to make decisions, how they interact as organizations to make decisions, and how they execute those decisions. This step is linked directly to the ultimate goal of IO, which is to find ways to create a desired response in the adversary decision-making process, to create a relative military advantage, or to achieve the desired end state of the military operation.
Understanding the Adversary's Information Infrastructure.
The second element of IPB is to understand the information infrastructure of the adversary. See Figure 4-3, which depicts how information flows within the unit, organization, and structure. This analysis includes the human interface as a valid form of information distribution and is not limited to only technology assessments. An understanding of how information from outside the adversary's unit, organization, or structure flows must also be developed for the commander's use. This includes understanding the local, regional, and global information environments. CA teams operating in-country can greatly assist in this process.
Analyzing the Adversary's Vulnerabilities.
Next, the intelligence officer analyzes the decision-making template and the infrastructure template to determine adversary vulnerabilities. Vulnerability analysis occurs on two levels.
- First, system vulnerabilities are identified which can be exploited to cause the desired effects on the decision process.
- Second, the appropriate attack mechanism and specific entry point (building, floor, air shaft) is determined.
Vulnerability analysis is then extended to include the collateral damage a C2W action may cause on the operating environment. As an example, an option in attacking an adversary's C2 might be to destroy his electrical power infrastructure. However, the strategic cost (political or logistical) of destroying this capability might outweigh the tactical gains. One implication of the GIE is that actions and their consequences are examined across the MIE, as opposed to the battlefield alone.
Developing Options
The decision-making template and the infrastructure template are combined to form a C2-attack course-of-action template. Various courses of action can then be developed and analyzed to determine the best way to use IO to influence, support, or accomplish the overall mission.
ASSESSING BATTLE DAMAGES
BDA serves to confirm or deny previous intelligence estimates and update the IPB. The intelligence system continuously assesses the effectiveness of IO. This BDA allows commanders to adjust IO efforts to maximize effects. An important aspect of this information BDA is timely analysis to determine when exploitable vulnerability is created in the adversary C2 structure. Compared to the way we look at conventional BDA reporting procedures, BDA in IO is not so apparent.
Information BDA is not always reported in terms of physical destruction of a target. The challenge of information BDA is to be able to assess the effects of our efforts without the benefit of physical confirmation. The effects may well be trends, activities, and patterns in future adversary actions. They could be as simple as an absence of activity on a C2 net, combined with an increase of traffic elsewhere, that is, reduced very high frequency/ultrahigh frequency (VHF/UHF) transmissions coupled with observations of increased courier traffic or heavy land line activity. BDA also examines the collateral damage C2W actions may cause to nonmilitary systems and capabilities within a commander's MIE.
Information Systems
Microprocessing, miniaturization, communications, and space technologies have combined to permit almost real-time intelligence and information sharing, distributed decision making, and rapid execution of orders from a wide variety of forces and systems for concentrated effect.FM 100-5INFOSYS allow the commander to view and understand his battlespace, communicate his intent, lead his forces, and disseminate pertinent information throughout his chain of command and his AO. Effective military and nonmilitary INFOSYS help the staff get the right information to the right location in time to allow commanders to make quality decisions and take appropriate actions. This chapter describes how INFOSYS operate as part of IO. Specifically, the focus is on the functions, role, security, and management of INFOSYS. These INFOSYS consist of--
The entire infrastructure, organization, personnel, and components that collect, process, store, transmit, display, disseminate, and act on information.Joint Pub 6-0
FUNCTIONS
INFOSYS include personnel, machines, manual or automated procedures, and systems that allow collection, processing, dissemination, and display of information. These functions cover all aspects of the organization, providing commanders with an accurate, relevant, common picture and a common situational awareness. Accordingly, a commander should consider his staff as part of the INFOSYS because its chief function is to plan and integrate IO. INFOSYS collect, transport, process, disseminate, and protect information in support of the CCIR. In addition, INFOSYS enable the commander to use information effectively to maintain an accurate view of his battlespace, coordinate the activities of his tactical forces, and help shape his MIE.
INFOSYS directly support battle command; however, all aspects of land warfare--operations, logistics, planning, and intelligence--depend on a responsive information system infrastructure. INFOSYS are able to simultaneously support current operational deployments and future contingencies. Interoperability and flexibility are critical characteristics of any INFOSYS, especially given the requirement for Army forces to conduct force projection and split-based operations using strategic systems.
- And to control many is the same as to control few. This is a matter of formations and signals.
-
Sun Tzu, The Art of War
ROLE
The role of INFOSYS is to provide the infrastructure that allows the Army to interface with the GII. INFOSYS enable the integration of all IO activities. INFOSYS form the architecture that--
- Supports the staff process.
- Supports the decision-making process.
- Provides the relevant common picture that helps synchronize force application.
- Links sensors, shooters, and commanders.
- Supports C2-attack and C2-protect capabilities.
The accelerated development of information technologies has created new techniques for managing, transporting, processing, and presenting data. These include imagery, video, color graphics and digital overlays, mapping, and data base technology.
With the revolution of information technology, developments in satellite communications, network and computer technology, and the infrastructure of military and nonmilitary INFOSYS combine to provide the commander with a global reach capability. See Figure 5-1. Communications and automation architecture allow for modular C2 support for force tailoring during any phase of an operation. Operations take place in a global environment and demand information from a host of information sources. Military and nonmilitary INFOSYS provide that global capability to support commanders and units across the range of operations. Discussion includes the INFOSYS, the principles that form the foundation for their support, and the direction of future INFOSYS technology.
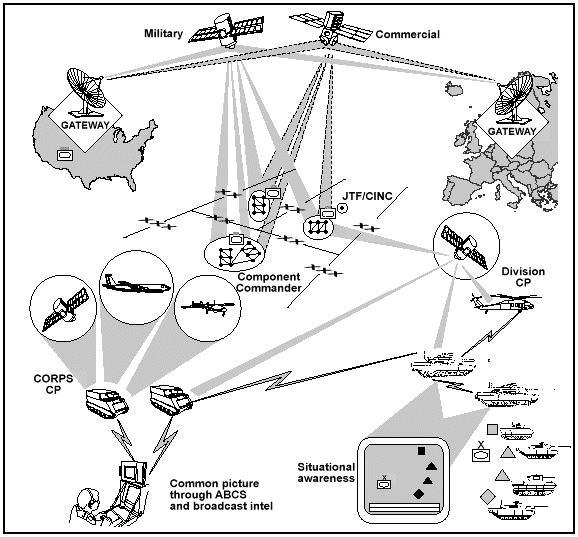
Military Information Systems
Military INFOSYS integrate fielded and developmental battlefield automation systems and communications to functionally link strategic, operational, and tactical headquarters. INFOSYS maximize available information networks through seamless connectivity as well as C4 interoperability. Figure 5-2 depicts the relationships of strategic, operational, and tactical architectures that tie the many distributed elements into an integrated, interoperable, and cohesive network.
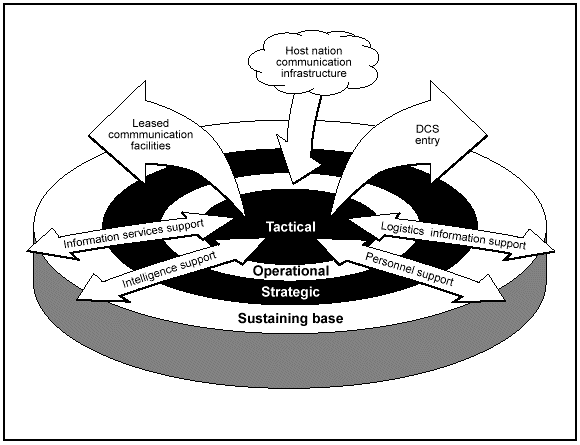
JOINT GLOBAL COMMAND AND CONTROL SYSTEM
The primary national warfighting C2 information system is the joint Global Command and Control System (GCCS), which interfaces with the Army Global Command and Control System (AGCCS).
ARMY GLOBAL COMMAND AND CONTROL SYSTEM
AGCCS is a seamless C2 system operating at the upper echelons of the ABCS and supports C2 for echelon-above-corps units.
ARMY BATTLE COMMAND SYSTEM
ABCS is the primary Army warfighting C2 INFOSYS and employs a mix of fixed/semifixed installations and mobile networks, depending on the subsystem. ABCS is interoperable with theater, joint, and combined C2 systems across the full range of BOS functions. It is vertically and horizontally integrated at the tactical and operational levels. ABCS provides connectivity to combat information data bases and processes information pertaining to each BOS. In addition to the theater-level AGCCS, the other components of the ABCS include the Army Tactical Command and Control System (ATCCS) and the Force XXI Battle Command Brigade and Below System (FBCB2).
Army Tactical Command and Control System
ATCCS is linked directly to AGCCS, providing the framework of seamless connectivity from brigade to corps. Moreover, it integrates the traditional disparate stovepipe functions into a coherent, seamless infrastructure that binds the BOS together. Figure 5-3 depicts this INFOSYS architecture. Tactical internet capabilities to establish the use and allocation of new IO capabilities offered by digitization of tactical forces are in development. The tactical internet has both operational and systems information architectures. The operational architecture is for required connectivity of force elements and the type and volume of digital information-sharing by elements within the force. The system architecture is for specific hardware and software to provide connectivity and dissemination of battle command information.The two evolving architectures account for predetermined user information exchange requirements throughout the tactical force.
Each node of the tactical internet can provide information services while on the move. Network management is an important feature of the tactical internet and is highly critical to the successful delivery of information across the battlefield. It enables the tactical information manager to track tactical users on the battlefield. It provides a tool to assist in the dynamic configuration of battle command information networks needed to conduct tactical IO.
Force XXI Battle Command Brigade and Below System.
In the near term, the FBCB2 system employs the GPS (POS/NAV) and communicates over the single-channel ground and airborne radio system/enhanced position location reporting system (SINCGARS/EPLRS) and the mobile subscriber equipment/tactical packet network (MSE/TPN). These systems form an integrated network to move information (data) between higher and lower echelons (vertically) and between adjacent organizations (horizontally) without routing through the brigade headquarters. Moreover, FBCB2 provides digital connectivity from brigade to weapons systems or platform level. It transitions from a network of three separate systems to a homogeneous network and system of systems comprised of--
- Appliqué--a family of laptop-sized computers connected to navigation devices and radios to provide processing and display capabilities to platforms without an embedded processor.
- Tactical Internet--a battlefield communication systems networked together using commercially based internet protocols.
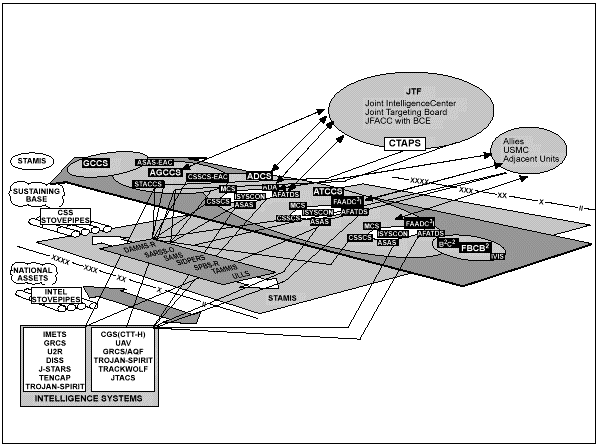
Nonmilitary Information Systems
Information technology is growing exponentially and transforming how the world conducts business, diplomacy, and war, requiring that commanders have a broader and externally oriented view of all sources of INFOSYS when executing IO. Moreover, DOD has limited authority for securing this civilian infrastructure or influencing the content of its products. Technological improvements in mobility, directed-energy weapons, digitization, and sensors continue to reduce factors of time and space and demand faster tempos of operation across vast areas.
Increasing global population, rapidly expanding world economic markets, and unprecedented advances in INFOSYS technology continue to perpetuate a global explosion of information networks of a nonmilitary or commercial nature. These ever-increasing networks are rapidly creating a global web or infosphere of information. Important changes are occurring in broadcast communications technology, computing, and space-based technology. The global nature and speed of news broadcasts can elevate apparently obscure events into international spectacles and has created a market for news known as infotainment. The number of players in the GIE are growing rapidly and sharing new information over computer networks at a steadily increasing rate.
Cellular communications and data compression advances increasingly provide greater communications freedom to individuals in ever wider regions of the globe. These advances enable individual soldiers as well as independent media or other actors to independently reach home using the internet or broadcast and publication sources. Potential sources of immediate information and the number and variety of MIE influences (both intentional and inadvertent) are rapidly multiplying. The cumulative effects of these changes permanently alter the shape of organizations and C4I architectures in ways that are just becoming evident.
- Networks are, in many fields, supplanting traditional hierarchies as the major organizing concept.
- In the business world, greater connectivity and access to information at all levels is eliminating much of the status-monitoring functions performed by middle management.
- New ways of thinking and operating are necessary because elements that are relatively low in an organization now have the information to make and execute decisions.
Like the rest of the nation, the Army relies on elements of an information environment it does not control. These nonmilitary INFOSYS include--
- US and host nation PSNs and postal and telegraph systems.
- Commercial communications satellite systems such as intelligence satellites (INTELSAT) and international maritime satellites (INMARSAT).
- Commercial receivers that use precision, space-based navigation systems such as GPS.
- Electric power systems that support information networks.
- Commercially developed software applications.
- Commercial, international news media.
- Public-accessed data bases and bulletin boards.
Historical Perspective
In 1944, at the Battle of Arnhem, the British First Airborne Division landed with the wrong radio crystals. They couldn't communicate with the outside, not even to their relief column at Nijmegen, a few miles away. They were isolated, under attack by superior numbers, and surprised at being dropped where they weren't supposed to be. During the entire multiday battle, members of the Dutch resistance in Arnhem were routinely talking to the counterparts in Nijmegen by telephone, because the national telephone system had not been taken down. It never occurred to a single paratrooper to knock on the door of a house and call Nijmegen, because the battlefield had been defined outside the civilian infrastructure. The Dutch underground assumed the paratroopers were talking by radio, and the paratroopers had never thought about using the civilian infrastructure.
The availability of nonmilitary INFOSYS often offer the command an alternative means to satisfy its informational C2 needs, but only after a careful assessment of security risks. As an additional benefit, use of available nonmilitary INFOSYS may reduce the requirement for deployed military information system packages. Operational use of a nonmilitary system allows planners to compensate for system shortages and to meet the surge of information requirements in the early stages of deployment.
The J6/G6 is responsible for standardization of nonmilitary equipment and software used throughout the AO. However, planners have to ensure the deployed modular INFOSYS packages implement open, nonproprietary, commonly accepted standards and protocols to interface with nonmilitary systems. Proper use of INFOSYS creates new challenges at individual user, organization, and system levels. Planners should consider these challenges in IO planning because they will affect the end user and the information management structure.
The user will be challenged by the digitization of the battlefield, by interface requirements between the operator and the system, and by the need to develop effective training strategies. The optimal use of INFOSYS ultimately depends on the availability of quality soldiers and leaders who are trained to employ advanced INFOSYS technology. Organizations will be challenged to develop flexible task-organization strategies that use the INFOSYS to adapt to the wide range of different conditions existing in the GIE. In addition, organizations will improve their battlefield functional capability in a digital environment by using advanced computer applications and tools. System challenges will emerge as a result of--
- Constantly advancing technology.
- Uneven distribution of early generation equipment mixed with new, improved digital INFOSYS.
- Limited EMS availability.
- The search for commercial-off-the-shelf products available for use within the INFOSYS architecture.
Meeting these challenges will enable and enhance the conduct of future operations.
Signal planning increases the commander's options by providing the requisite signal planning support systems to pass critical information at decisive times, thus leveraging and exploiting tactical success and facilitating future operations.FM 100-5
SIGNAL SUPPORT
Throughout all force-projection stages, a paramount need exists for a signal support means to transport information from the sustaining base power-projection platform at CONUS installations, through strategic gateways, to the forward-most warfighters. Signal support requirements to fulfill this task are enormous and vary greatly, depending on the type of military operation.
Mission-Essential Tasks
Information battlespace requires an end-to-end, protected, seamless, multigigabyte information-transfer and processing capability for the warfighter to conduct IO virtually anywhere at any time. This capability must be a multimedia system of systems that transports video, imagery, data, and voice information to create an infosphere that the battle commander can plug-in and pull what he needs to visualize the battle from the current state to a successful end state. The signal support mission-essential tasks to project and construct the infosphere are to--
- Link the force to the infosphere to achieve seamless global connectivity.
- Transport information with broadband, high-capacity systems optimizing satellites and terrestrial signal support to connect CONUS, installation sustaining bases (ISBs), and joint operational areas (JOAs).
- Reach back through strategic entry points to power-projection platforms and information fusion centers.
- Extend the communication range of battle command operations centers and fighting platforms by providing C4 for mobile operations (C4FMO).
Support Enablers
The enabling objective of signal support to IO is to provide the warfighter the capabilities he needs to obtain and share in near real-time. Signal support requires the total integration of all information management functions into a system of systems or ABCS. ABCS provides knowledge-based information that is adaptable and responsive to the commander's IO requirements. The ABCS has a suite of C4 hardware and software capable of collecting, processing, fusing, managing, transporting, disseminating, displaying, and protecting force-level information (status) and force-level control information (intent, plans, orders). The signal support mission-essential tasks to enable IO are to--
Digitize, compress, and broadcast multimedia battle command information in five categories, using increased bandwidth, high-efficiency transport systems. The multimedia categories control, monitor, alert, inquire, and explore critical information.Encrypt and provide multilevel information security.
Manage information networks with smart software that dynamically allocates throughput capacity on demand and then routes and disseminates information.
Display via ABCS, a three-dimensional interactive knowledge-based relevant common picture (RCP).
While the core of the twentieth century land warfare has been the tank, the core of the twenty-first century will be the computer.
General Gordon Sullivan, CSA (1993)
FUTURE TECHNOLOGY
As technology advances, the conduct of operations will continue to change. Each advance in information technology will--
- Help leaders form a more complete picture of the battlespace.
- Generate the potential for faster, higher quality decisions.
- Support more rapid maneuver in terms of both time and space.
- Increase a unit's flexibility and agility.
Nevertheless, technology is only an enabling tool. Quality soldiers and well-trained leaders remain the true centerpiece to successfully planning and operating this increasingly digitized and automated information system of systems. The following examples illustrate where information technology could enable military operations by the turn of this century.
-
Today, tactical radio communications networks exist separately with no automatic
routing or interconnection between nets. On the future digitized battlefield,
a tactical internet capability will enable direct communications among and
between virtually all users. This could enable a whole new level of horizontal
integration, coordination, and synchronization that will coexist with the
current vertical system (Figure 5-4).
-
Direct broadcast satellites enable wide access to information at various
echelons in real time or near-real time. This in turn enables a new level
of empowerment and self initiative for lower echelons.
-
Image compression and transmission technologies will allow transfer of images
and video from numerous sensors and platforms, enabling better understanding
of battlespace for planning, rehearsal, and mission execution.
- Finally, multimedia technology will enable three-dimensional presentation of imagery and graphics to help commanders visualize their battlespace for more effective training, planning, rehearsal, and execution.
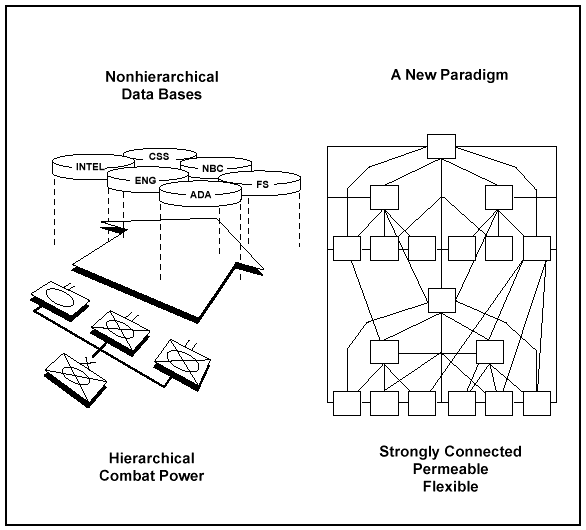
SECURITY
Due to the present and ever-increasing dependence upon automated INFOSYS within the Army, INFOSEC and information systems security (ISS) has become critical. In both war and peace, computer systems and networks on which units rely for logistics, personnel, administration, maintenance, and financial data processing and transfer are vulnerable to attack. Often, the internet is a favorite communication platform for intruders. Gaining access to a unit's computer and communications network can be accomplished by a wide range of methods and techniques. Some of the more common methods include--
- Inserting malicious software through contractors.
- Tracking software maintenance changes and system operations activities.
- Alternating access paths or sniffer devices that trap information about traffic and passwords.
These intrusions may be initiated during peacetime or at any point in an operation. It is even possible that a military system could come from the factory with an embedded logic bomb or virus. In the past, new commercial floppy disks used by government agencies have been found to contain a virus upon delivery from the factory.
Accordingly, security measures and procedures must actively as well as passively preserve the confidentiality, integrity, and functionality of INFOSYS. Protection requirements include near-real-time measures that detect intrusions and alterations, then react and counteract by restoring the INFOSYS needed by commanders to support the military operation. A series of security measures that are facets of an overall C2-protect effort ensure ISS. The three primary security measures are--
- Procedures for quality assurance.
- Denial of unauthorized intrusion.
- Hardening of programs.
Historical Perspective
In 1994 a computer hacker operating from the United Kingdom attacked the Rome Air Development Center at Griffiss Air Force Base, NY, where he compromised the security of 30 systems and penetrated more than 100 other systems before being caught in a 26-day international electronic manhunt. The victims included the South Korean Atomic Research Institute, NASA, the Goddard Space Flight Center in Greenbelt, and the Jet Propulsion Laboratory in California.
The Defense Information Systems Agency estimates that DOD experienced 231,000 incidents, or security intrusions, in 1994. These incidents included destruction of data, modification of data or software, stolen data or software, and shut-down of hosts or networks. Affected DOD functions include--
- Ballistic weapons research.
- Inventory and property accounting.
- Knowledge-based simulation.
- Payroll and business support.
- Mail hub for postwide electronic mail.
Subcommittee on Investigations, June 1996
Procedures for Quality Assurance
Quality assurance procedures include configuration control and reduction of inadvertent corruption of both data and processes. In order to protect automated INFOSYS, the first step is to understand the threat against them. Security threats to INFOSYS fall into two categories:
- Compromise of data and information.
- Denial, corruption, or loss of service.
Protection Against Intrusion
Protection against intrusion into friendly computer networks is accomplished through denying unauthorized entry into these systems. The vast percentage of intrusion results from human error. Training and OPSEC compliance by system managers, operators, and users are the best measures to combat system compromises. In addition, systems administrators must be able to track down intruders.
Hardening of Programs
In addition to tracking down intruders, system programs should be hardened against intruders' attempts to gain vital information or damage information flow. No protection plan is perfect, and protection/restoration resources are finite. OPLANs and OPORDs specify the priorities of protection efforts.
MANAGEMENT
INFOSYS management consists of prioritizing information in a limited communications environment. The primary purpose of automated and manual INFOSYS is to achieve an information advantage by using and managing information for timely and accurate decision making in any type of operation. The focus of battle staffs is to leverage available technology by employing INFOSYS that give the commander the desired information at the right time and the right place. See Appendix C.
General consensus is that the desire for information by higher headquarters is quickly exceeding the subordinate commander's ability to provide it in a timely manner. Commanders at all levels must carefully define their critical requirements.CALL Newsletter, July 1994
Management Process
All information that the staff provides is predicated upon the commander's intent, concept of operations, and supporting commander's CCIRs. The CCIRs govern the C4I architecture and its use. The CCIRs define the commander's information needs, thus focusing the staff and INFOSYS support on the rapid acquisition, fusion, and analysis of information that yields knowledge-based operations. The INFOSYS augment routine or periodic reports (established by unit SOPs) with specific requests for information from BOSs or other data bases.
Technical Systems Management
The ABCS spans several systems and requires technical management with similar spans. INFOSYS provide an efficient and rapid means of retrieving information, enabling the battle staff to develop and maintain a single, virtual (or logical) data base that satisfies both current and anticipated CCIRs. This allows battle staffs to continue coordinating, integrating, and synchronizing current and future IO. The ABCS, which works primarily at the SECRET classification level, poses both a technical and tactical INFOSYS challenge.
Technically, the network of ABCS devices function as a seamless whole with redundant paths. Data flow among computers does not require intensive operator action. However, understanding and interacting with the information received is generally a user requirement. The INFOSYS architecture covers the entire battlefield, enabling the command and control of forces. This architecture consists of integrated local area networks (LANs), wide area networks (WANs), and battlefield automated systems integrated into a single, seamless system subject only to the requirements of multilevel security (MLS) as depicted in Figure 5-5.
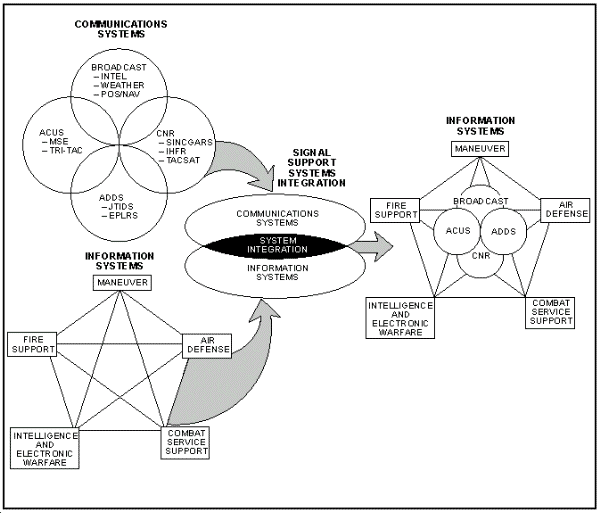
INFOSYS allow the commander and his staff to distribute critical information between higher, lower, adjacent, joint, and multinational forces. Voice traffic and data distribution are the primary methods of passing this information. Voice traffic includes user-to-user, conference, and broadcast type of transmission. Data distribution includes formal record traffic (joint message text), informal record traffic (facsimile and electronic mail), system-to-system data, and POS/NAV data.
Technical systems management connects all INFOSYS devices into a multilevel secure network that supports the commander's concept of operation and maintains the correct security levels at each network node throughout the battle. Technical systems management requirements include--
- Planning the INFOSYS network.
- Planning communications connectivity.
- Planning network security.
- Allocating frequencies.
- Controlling and monitoring the connection of systems devices to one another and to supporting communications systems.
- Reconfiguring the network as required by the tactical situation or equipment failures.
- Maintaining the network.
- Maximizing network performance.
Tactically, the information flow must support the needs of commanders. Commanders and staffs must have the information they need to plan, direct, control, and coordinate an operation. The information must be secure and readily available. Tactical systems management ensures that information is exchanged inside and outside the unit and made available according to the needs of commanders and staffs to support the tactical plan.
Within each BOS, the information flow, processing, and storage are managed according to the needs of the BOS. Flow, processing, and storage of information among BOSs are collectively managed according to the needs of the overall force-level commander. Tactical systems management includes--
- Planning information exchanges.
- Planning data base locations and replications.
- Planning continuity of operations (including security).
- Controlling and monitoring information exchanges and data base transactions.
- Implementing continuity of operations plans as required.
- Planning for degradation of the network.
Appendix C contains detailed information on INFOSYS planning.
Electromagnetic Spectrum Management
In a dynamic battlespace, each echelon of command must effectively contribute to achieving a state of information dominance. To do so, it uses the EMS for its own purposes, while effectively preventing similar use by an adversary. The EMS is a valuable and finite resource. Controlling it is the linchpin for digitization. Commanders must have a battle staff with knowledge of the EMS.
The J6/G6 or signal officer has staff responsibility for battlefield spectrum management. The spectrum manager under his supervision manages all spectrum use. Major considerations in IO planning include deconfliction of frequencies, development of joint signal operating instructions (JSOI), and development of the joint restricted frequency list (JRFL), as well as all other bandwidth requirements levied by intelligence, C2W, CA, PA, and signal elements. These elements must be balanced to ensure that users maximize the EMS effectively.
Uncontested ownership of the EMS is not guaranteed. However, to gain control of the flow and content of information, units must effectively manage the EMS to reduce the likelihood of electromagnetic interference (EMI). For unopposed entry operations, the status of forces agreement made with a host nation defines frequency provisions and procedures to be followed in all frequency and radio regularity matters. Parts of the spectrum are reserved by nations and other international agencies and therefore are not available for use by the US military.
Where agreements do not exist, coordination of frequency use is made through DOS. The United Nations (UN) recognizes the International Telecommunications Union (ITU) as the specialized agency in the telecommunications field. The ITU allocates the international radio frequency spectrum, registers frequency assignments, and coordinates resolving interference. Forced entry operations create the greatest demands for flexible and adaptive spectrum management. An adversary will use the spectrum as he sees fit, creating potential interference with friendly usage. For example, a television station may interfere with combat net radios, yet the OPLAN may call for capturing the station intact for future friendly use, thereby hindering efforts to eliminate the interference. During initial spectrum planning, planners must consider adversary spectrum usage and management and adapt to events as they unfold.
Communications dominate war; they are the most important single element in strategy.Mann (1907)
Planning and Execution
JFCs employ air, land, sea, space, and special operations forces in a wide variety of operations...to not only attack the enemy's physical capabilities but also the enemy's morale and will.Joint Pub 3-0The challenge for commanders in the twenty-first century is to operate effectively in a dynamic joint and multinational environment against a wide array of threats. Maintaining the information high ground helps commanders meet that challenge. As full-dimensional operations evolve, information and IO become increasingly important to Army operations as the Army executes missions to deter conflict, to compel opponents, to reassure allies and friends, and to provide domestic support. This chapter discusses considerations for planning and executing IO.
PLANNING
IO planners must consider the conditions that affect the Army as it deploys. They must focus on the principal objective of achieving information dominance, and, in doing so, follow a planning process that applies the components of IO correctly in support of military operations.
Employment Considerations
The IO discussed herein depend on a series of considerations and conditions that affect the force-projection army as it deploys and operates to support joint, multinational, and interagency power-projection operations. Figure 6-1 depicts how IO apply across the spectrum of operations and how the use of the IO components, especially C2W operations, increases in times of conflict and war
LEVELS OF WAR
The levels of war--strategic, operational, and tactical--provide a useful framework for ordering IO activities within a commander's battlespace. This framework helps clarify IO activities by echelons within the theater across the full range of military operations. In the theater, all land operations are conducted as part of a larger, integrated, joint, multinational, and/or interagency campaign. Under the direction of the NCA, a unified CINC sets the campaign in motion. The campaign is supported by all elements of national power: social, economic, political, and military. The interconnectivity and interoperability of INFOSYS are the critical elements that tie these disparate sources of power together. As described in Chapter 5, INFOSYS connectivity is a prerequisite to success in this multidimensional environment.
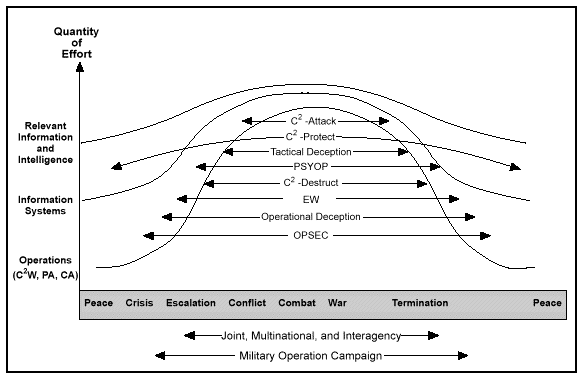
Strategic Level
At the national and theater levels, the employment of IO techniques offers a series of strategic options for consideration. The potential for nuclear exchange and major power conflicts in the post-Cold War world is diminishing. Therefore, military options to effectively attack a strategic target--while minimizing the potentially devastating social, economic, and political effects of conventional military use--increase in importance. Army IO offer both a potential deterrent capability and coercive capability at all levels of war.
As with nuclear warfare, nations can engage in IO at strategic, operational, and tactical levels. Similar to nuclear warfare, the effects can be widespread or targeted against a narrow range of hostile capabilities. As with nuclear warfare, nations may eventually develop IO capabilities that are perceived to be principally offensive or defensive. National strategies can be supported by building an IO capability based upon varying combinations of C2-protect and C2-attack and other capabilities. From purely a technical viewpoint, the spectrum of candidate information targets and the range of operational alternatives are virtually unlimited.
US Army force component commanders, in support of national and theater strategic objectives, are responsible for employing the full range of their information capabilities during war or OOTW. As part of a national IO strategy, the Army can be called upon to employ its capabilities to support both direct and indirect actions. Occasions have arisen and will continue to arise that dictate the use of Army capabilities outside a purely battlefield context. The Army component commander has capabilities ranging from PSYOP support to deep battle strikes to contribute to joint warfighting operations.
Information and INFOSYS capabilities inextricably link the traditional levels of war. These phenomena require commanders and staffs at each level to understand the information gathered, where the information is required, and the means or connectivity necessary to deliver and/or receive that information. National-level systems (DOD and commercial) are increasingly capable of supporting and enhancing tactical operations (weather, communications, imagery, navigation). The challenge for leaders is to--
- First know the information is available.
- Include the requirements for the information in plans and exercises.
- Understand how to get the information into a system, unit, or headquarters that provides an enhanced operational capability.
In many cases the connectivity is found through other services or through civilian agencies. For example, the long-haul connectivity during Operation Desert Shield/Storm was augmented by commercial satellite terminals. Systems such as the Army High Frequency Electronic Warfare System (AHFEWS), employed at the strategic or operational level with other joint C2W assets, could diminish an opponent's confidence and will to fight before operations begin. Army UAVs could contribute to the domination of OOTW situations as an initial show of strength before the possibility of hostilities occur. If necessary, they could provide the selected intelligence needed to dismantle an adversary's C2 structure. Combined with deception and PSYOP, these contributors to C2W could erode a potential opponent's confidence in his own forces and conceal the OB and intentions of the friendly forces.
Army component commanders strive to support the joint force attack strategy at all levels in order to commit and employ Army capabilities--including C2W, CA, and PA--to the best possible advantage. As with other military activities, IO need to be coordinated and integrated with the OPLAN and JTF campaign plan and synchronized to achieve decisive results. IO offer the prospect of maintaining friendly C2 and situational awareness at a highly dependable level, while simultaneously degrading an adversary's ability to effectively command and control his forces. Such a combination should create a state of information dominance.
Operational Level
At the operational level, IO occur across the full range of operations and are critical to the success of each stage of force projection. In peacetime, IO support--
- Deterrence and reassurance.
- General situational awareness.
- Operational assessments and estimates.
- Contingency planning.
- Training in support of the CINC's planning and preparation activities.
During conflict or hostilities, IO implement C2W activities at each level of war. Continuous engagement in IO helps the commander seize and sustain the initiative and synchronize operational capabilities. This allows the commander to control the tempo of operations so that friendly forces can effectively transition from peacetime to wartime operational environments and situations. During Operation Desert Storm, for example, the coalition experienced information dominance in near real time because the enemy's INFOSYS were almost totally disabled.
The linchpin permitting the operational maneuver of coalition forces in Iraq was the enemy's inability to visualize the battlespace. This enabled an entire US corps to move in relatively open desert terrain for distances beyond 200 kilometers and still achieve total operational surprise. The enemy's information flow had been so disrupted and his surveillance capabilities so suppressed that he could not see the battlefield. The success of that operational campaign depended critically on information dominance. Space sensors, aircraft-borne sensors, ground sensors, helicopter-transported Special Forces teams, and Marine drones combined to give the operational commander an accurate and timely picture of the battlespace.
Historical Perspective
If the Iraqi forces moved in daylight, they were subject to immediate attack by coalition air and surface-to-surface missiles. At night, their movements were detected by superior night- capable sensors. They were then attacked by the coalition's all-weather attack aircraft. Further, their use of broadcast media, coupled with a lack of understanding of the coalition's intent, caused them to base their decision cycle on externally filtered information.
Tactical Level
At the tactical level, commanders usually accomplish their missions through combined arms operations. At this level, IO are often limited in scope. While a tactical-level commander uses all aspects of IO, the focus is often on disruption or destruction of enemy INFOSYS or nodes, primarily through EW and physical destruction. The commander maintains access to his INFOSYS through OPSEC, ISS, and EP. Other applications include--
- Planning and executing C2W.
- Projecting and constructing the infosphere.
- Protecting friendly information.
- Establishing and maintaining user access to battle command information via ABCS.
- Enabling IO and battlefield visualization.
- Collecting and producing RII.
- Attacking the enemy's C2 system.
Information dominance is a temporary tactical condition achievable through a deliberate process. It entails the construction and protection of the information environment, collection of intelligence and relevant information, processing and dissemination of such information, and focused attack against both the enemy's C2 and his eyes and ears. Information dominance facilitates superiority in battlefield visualization at a specific time and place, creating a window of opportunity that is fleeting at best. The commander must seize the opportunity to gain the advantage through effective battle command. Two features are essential to this process: CCIR and tempo.
-
Commander's Critical Information Requirement. The commander must control
information, or he runs the risk of being overwhelmed or disoriented by it.
CCIR can control the glut of information and separate the true signals from
the noise. CCIR cannot be a fixed concept. Like IPB, it must be precise to
ensure responsiveness and dynamic to survive.
- Tempo. The tempo is the time devoted to the tactical decision-making process. Execution must be dramatically compressed. But, because the information dominance advantage is achievable through deliberate action within a specific battlespace, battle command can be better synchronized, resulting in the creation of opportunities that lead to success.
Tactical units, both maneuver and CSS, participate in IO directed by higher headquarters. In some operations, tactical units perform targeting--striking C2 nodes, deception, reconnaissance and surveillance, and PSYOP activities focused on supporting an overall theater-level IO. They are also linked to the layered information environment via a CMOC or the PAO. For example, CMOC connectivity to local governmental, cultural, social, and economic institutions can provide a wealth of information supporting military operations. The PAO facilitates media relations and contact to support friendly forces.
Historical Perspective
One of the earlier applications of C2W was demonstrated during the American Civil War. From the beginning, telegraph lines became an important target of cavalry raiding parties from both sides. Since the Union forces were more extensively equipped with telegraphic systems, they were more vulnerable. This vulnerability was exploited by Confederate troops.
Among the more innovative soldiers were the telegraphers attached to Confederate cavalry commands. Their specialists, who were also qualified as flagmen, rode in the lead as Confederate cavalry units raided Union territory. They switched military traffic to the wrong destinations, transmitted false orders to the headquarters of Union commanders, and cast suspicion upon all orders that came by wire. When they had finished the job, they cut all the wire in sight and took home with them as much as they could roll up in a hurry.
With an expanded vision, tactical field commanders anticipate potential threats of disinformation, enemy PSYOP, and rumors within their command, as well as the potential backwash of public information into their battlespace. Establishing an effective internal information program enhances the morale of soldiers, reinforces the stated unit mission, and supports accurate media reports for both soldiers and their families.
RESTRAINTS AND CONSTRAINTS
An increased awareness of how operations shape and are shaped by the MIE is necessary as commanders and staffs plan, prepare, and execute IO. Because information can and will be interpreted differently by any number of individuals or groups, military operations can affect the economic, political, and social fabric of individual lives, organizations, and nations far beyond the scope and intent of the military operation. This reality creates a dynamic set of restraints and constraints that impact military operations.
Asymmetrical or hybrid operations are the norm as tailored forces are assembled to meet a wide variety of needs. Accordingly, different levels of modernization are found within the army, among joint or interagency task force members, and between US and coalition forces. Disparities in information and communications technology threaten continuity and interoperability. Information capabilities can offset these variances, providing the force and the connectivity needed to operate effectively.
Statutory constraints, international law, federal regulations, and rules of engagement (ROE) may limit a commander's options regarding IO. Laws and regulations, such as those governing the use of the frequency spectrum, public information, PSYOP, and espionage, provide examples of free access to information and INFOSYS and are intended to prevent misuse or abuse of these activities. IO may be further constrained or further enabled as new laws, rules, agreements, and protocols are established and as the international community adjusts to the impact of the information explosion.
Simple interference, willful manipulation, and corruption or destruction of data bases or INFOSYS, to include space-based systems, have become increasingly active and sensitive activities. The information web and its continuity or disruption has implications far beyond the military environment, into economic, political, and social dimensions. Competition for the EMS, space-based data systems, communications networks, and webbed computer networks all set the stage for potential interference, both intentional and unintentional. Collateral damage gains new meaning in this environment. The potential for the civilian population to be directly or indirectly affected is present and growing.
The laws governing the information environment and the law of land warfare are the guidepost, and every soldier is responsible for preventing violations. Close coordination with the supporting judge advocate is critical to assuring compliance with applicable restraints and constraints. As the Army moves into the Information Age, the features of the battlespace continue to change, and the means and methods of conducting all types of operations also change. Success in any operational environment depends on leadership, discipline, morale, and professional training.
Today's operations increasingly depend on intelligence and INFOSYS from tactical through strategic levels to provide critical information on all aspects of the friendly and enemy situation. The seamless and horizontal flow and integration of information provides valuable operational data to support planning and battle command. While the fog of war has thinned, it will never completely disappear. The commander will always face some uncertainty on exact enemy force dispositions, OB, and operations in general, not to mention some degree of uncertainty about the enemy's intentions. That uncertainty will be compounded by artful opponents (military or otherwise) and exacerbated by the consequences of unintentional actions or influences from other sources within the commander's MIE.
Information Dominance
The principal objective of IO is to gain information dominance--a relative advantage between the friendly commander's decision process and that of the adversary--and to use that advantage to enhance and enable the elements of combat power. IO are an essential foundation of knowledge-based, combined arms warfare. Likewise, full-dimensional operations require integrated IO.
BATTLE COMMAND
Army operations are profoundly affected by information and IO in the critical function of battle command. Although battle command remains principally an art, it relies increasingly on the ability to process information and move it rapidly to critical points in the operational area. To achieve the required level of information dominance, the Information Age commander treats IO as he would any other critical element of combat power, by providing guidance and direction to his staff and his subordinate commanders.
The commander's personal involvement in the development of the CCIR makes it the principal vehicle for ensuring that his battle command information needs are met. Advances in information technology have made decision making and control of units more technical and quantifiable; yet much of those functions remain well within the realm of art, not science. The commander understands that he will never have all the critical information he wants, when he wants it, and that leading soldiers and units to success will remain largely in the realm of art. Accordingly, he employs IO to retain an information advantage over his opponent.
Digital technology enhances C2. It allows the Army to have previously unimaginable amounts of accurate and reliable information. It allows higher commanders to have detailed knowledge about events several echelons below. At the same time, it gives subordinates more information about the bigger picture and about what is happening in other areas of the picture. Based on the RCP, commanders are better able to continuously, and in near-real time, integrate combat power.
Technology and time do not change some aspects of battle command. Commanders and staffs will continue to make judgments based on less than perfect information. Likewise, they will have to inspire soldiers to perform their duties in the face of fear and fatigue. Commanders will continue to mold units to levels of high performance through training, chain-of-command development, personnel management, morale, and a positive command climate.
Elements
The three basic elements of battle command--leadership, decision making, and controlling--are characterized by both continuity and change.
Leadership. The commander's leadership continues to provide purpose, direction, and motivation to soldiers and units. Leaders will be better equipped to make informed decisions but will operate within a philosophy that will not change.
Decision Making. Decision making is facilitated through much-improved information technologies, maintenance of a relevant, common picture upon which to base decisions, and improved decision-making skills of leaders.
Control. Control is facilitated by better communications, to include video broadcasting and private links, new position locating and reporting technologies, greater situational awareness, remotely shared electronic maps, automated decision support aids, and other information technologies and procedures.
Challenges
The challenges for leaders are to provide purpose, direction, and motivation to forces operating over greater spaces, under greater time pressures, and amid more complex situations. Specific implications of IO as they apply to the commander's art include the following:
-
Identifying, conceiving, and communicating the unit's purpose remains a complex
art. This is largely the commander's domain. Understanding the mission, the
intent of the next two higher commanders, and the concept of operation of
the parent organization may be easier with improved communications, but the
restatement of the mission, the formulation of the intent statement, and
the issuance of planning guidance are still functions the commander must
perform himself.
-
The current doctrinal approach of mission orders, or decentralized
decision-making, is not anticipated to change. The ability to communicate
with remote commanders and staffs by video conference and by other electronic
means does not eliminate the commander's need to provide implicit direction
to subordinates. Information technology enhances the effort by providing
a RCP across the BOSs and functions in near real time. During critical actions
the commander focuses most of his attention and decision making on the main
effort. Therefore, relying on his subordinates to act within his intent and
concept is vitally important.
-
Commanders need to motivate their soldiers, as well as their staffs and others,
to accomplish difficult tasks under dangerous, trying circumstances. Commanders
will continue to inspire and mentor subordinates through face-to-face
communications and physical presence. Although it may be difficult, commanders
still need to position themselves where they can see the battlefield
and where soldiers can see them. Commanders establish interpersonal relationships
with their staffs and subordinate commanders. Commanders also contribute
to unity of effort by establishing personal relationships among and between
commands to foster mutual trust, cooperation, open communications, and teamwork
in both national and multinational operations. Commanders remain the leaders
that all members of the organization look to for timely decisions and informal
feedback.
-
Uncertainty will always exist. The commander may know what the enemy is doing
at the moment, but will rarely know why. Sound command judgment is required
to determine what the enemy may be doing tomorrow. In addition, no matter
how well the commander knows the status of his forces today, he needs to
make judgments about what their condition may be tomorrow. Unquantifiable
information and information gaps will remain. No matter how much information
the commander gathers before making a decision, uncertainty will remain.
- The ability to process information through risk management enables commanders to avoid unnecessary risks. Identifying, analyzing, and selecting control measures to manage risks gives commanders maximum force protection.
STAFF RESPONSIBILITIES
To facilitate IO, the commander establishes staff responsibilities for planning and execution. OOTW present unique challenges due to the heavy involvement of the media and other players in the GIE. The staff must consider the actions and reactions of US and foreign governmental and nongovernmental agencies, PVOs, and the media when planning operations. Depending on the situation, IO planning can be a complex undertaking or a relatively routine staff function. The commander's IO cell, however organized, draws upon selected expertise throughout the primary and special staff, with liaison and possibly augmentation from subordinate commands. A number of techniques and a variety of arrangements are available to accomplish these responsibilities.
Staff Members
Current staff members can integrate IO actions into the operation. This approach uses current staff procedures, processes, and techniques to plan, coordinate, and synchronize IO with the operation. The likely choice for the nonmodernized or partially modernized force is to designate a staff representative to supervise these actions.
Process-Oriented Group
A process-oriented or ad hoc task group, led by the J3/G3, can integrate and synchronize IO actions. This approach is similar to that used for targeting and deep attack. This too is a viable approach for the partially modernized force or nonmodernized force entering a complex combat or noncombat environment where a number of IO capabilities and or threats exist. Appendix D provides a notional IO structure at Figure D-1.
Information Operations Battle Staff
A dedicated IOBS can be formed to integrate IO actions. This approach would apply to partially and fully modernized forces. The battle staff would consist of all staff members with a functional responsibility within IO, such as signal, fire support, PA, CA, OPSEC, EW, PSYOP, and battlefield deception. Figure D-2 of Appendix D illustrates a notional IOBS.
J3/G3 Staff
Since IO are only one facet of the larger operation, albeit an important one, the J3/G3 is the primary manager of information. He outlines and monitors the performance and responsibilities of the staff in processing information to support IO and the knowledge flow. The J3/G3 ensures that the staff collects, analyzes, and presents information that fulfills the CCIR. Specific requests for information from BOSs or other information source data bases are generated to fill specific needs. Routine or standard reports to the staff (established by unit SOPs) are used when information requirements remain stable through operations.
The J3/G3, within his overall staff responsibility for integrating IO into the OPLAN, usually designates one individual accountable for all IO actions. Key staff members participating in IO coordination and integration include intelligence, signal, fire support, PA, CA, EW, deception, OPSEC, PSYOP, and logistics personnel. In peacetime operations, the G5, PAO, and specialized staff, such as the SJA or chaplain, participate in IO planning and operations. Even as the role of PA expands, a separation between PA and PSYOP functions must be preserved to maintain the credibility of PA spokespersons and products. While essential coordination between these staff functions may be accomplished through the IO cell, the IO cell PA representative should not also serve as the primary command spokesperson.
Army Land Information Warfare Activity
C2W requires the commander to develop and sustain staff members who are technically and operationally proficient in C2W. Maintaining C2W staff proficiency is a complex undertaking, demanding extensive training, education, and experience with other services, agencies, and joint commands. To enhance the capability of the Army component to conduct IO, Department of the Army established the Land Information Warfare Activity (LIWA). LIWA acts as the operational focal point for land IW/C2W by providing operational staff support to active and reserve component land component commanders (LCCs) and separate Army commands.
LIWA field support teams (FSTs) are tailored to fill the specific needs of a component commander and are specifically earmarked to that land component command. Team members consist of a need-driven mix of PSYOP, deception, OPSEC, EW, and intelligence specialties, along with members of other service components, if required. LIWA FST members support the LCC's staff as it plans, coordinates, and executes IW/C2W in joint and multinational environments.
LIWA FST supports commands ranging in size and capability from a numbered Army headquarters to a corps or division when these tactical commands are designated the land component of a joint task force. Appendix B provides information on LIWA support and services.
What separates good units from not so good units is the way the unit processes information.General Donn Starry, US Army (1978)
Planning Process
The IO planning process consists of five basic steps that apply across the three components of IO (operations, RII, and INFOSYS).
MISSION ANALYSIS
The first step of the process begins as the commander analyzes the mission, formulates his overall concept of operations, and considers how IO can contribute to achieving his mission. Under the direction of the J3/G3, the staff analyzes the command's mission and concept of operations to derive a concept of IO. Simply put, "How can IO support the mission?" The staff must consider both C2-attack and C2-protect. Flexibility is essential, as IO support may shift over the course of the overall operation.
During analysis, the staff examines enemy and friendly INFOSYS within the context of the commander's MIE. The staff determines the capabilities both sides require to operate effectively. It also sets out the requirements and conditions needed to establish information dominance. The staff considers nonmilitary INFOSYS influences or capabilities beyond traditional military control--such as local or regional communications networks, radio, television, computer networks (internet or worldwide web), and the news media--that may influence the operation. The examination produces a list of critical nodes and vulnerability analyses.
- The C2-attack analysis identifies adversary C2 systems of C2W interest and determines the critical C2 and C2-attack nodes in those systems. The C2-attack focus increases payoff by identifying key target vulnerabilities for offensive action.
- The C2-protect analysis focuses on the adversary's capability to detect, locate, and attack critical friendly C2 nodes to disrupt the friendly decision-making process. As with C2-attack, intelligence plays a major role by providing information on adversary sensor capabilities, target selection, and attack means. The staff considers the physical destruction, jamming, and intrusion, as well as deception and PSYOP means available to the adversary. The product is a list of critical, vulnerable nodes and processes that must be addressed by C2-protect.
PRIORITIZATION
The second step is to prioritize both friendly and enemy critical nodes and vulnerabilities. This part of the process develops potential targets for C2-attack and C2-protect and ensures deconfliction of their integrated effects.
For C2-attack purposes, nodes critical to more than one adversary system may have a higher priority. Vulnerability may override criticality, with more critical nodes that are less vulnerable receiving a lower priority. Priorities should be balanced and shifted between C2-attack and C2-protect as required to support the unit mission. The C2-attack product is a prioritization of the list of critical, vulnerable adversary targets from earlier work. Similarly, C2-protect targets should be identified in terms of criticality and vulnerability, then prioritized.
CONCEPT OF OPERATIONS
The third step of the process is the formulation of an IO concept of operations to influence the adversary's C2 while protecting friendly C2. The G3/J3 reviews his sets of potential C2-attack and C2-protect targets. He assesses available IO capabilities to develop an IO concept of operation that best supports the overall operational mission and is synchronized with the overall concept of operation. Synchronization of IO, both internally (among the five C2W elements and CA and PA) and externally (across the BOSs), is absolutely critical for achieving decisive C2-attack and C2-protect results. The impact of proper synchronization is to focus the effect of the entire range of friendly capabilities to achieve maximum effect at the decisive point in time and space.
Although the situation dictates the critical areas for the operation, the commander and staff consider these specific areas in planning:
- Operations--both C2-attack and C2-protect objectives from a friendly and enemy perspective. The basic OPLAN/OPORD and the C2W annex synchronize physical destruction, EW, OPSEC, deception, and PSYOP to maximize C2-attack and C2-protect. Many C2W activities can have the effect of maximizing protection while degrading adversary C2 capabilities. Other influences in the commander's information battlespace can directly impact mission success, for example, the media, governmental and nongovernmental organizations, local or regional social/cultural influences, perceptions, attitudes, and opinions.
- RII requirements.
- INFOSYS support requirements.
The battle staff considers all these factors to arrive at an IO concept of operations. The concept is oriented on establishing information dominance in order to give the force dominant battlespace awareness and control of the MIE. A critical tool in developing an effective concept of operation is the synchronization matrix. The synchronization matrix is designed to array time-phased objectives along a horizontal axis against performing units usually organized by BOS along a vertical axis. Within the framework of the matrix, critical tasks that must be performed to achieve the IO objectives are identified, aiding the planner in recognizing the interrelationship between specific tasks and actions and the need to orchestrate them in a manner that maximizes the impact of their execution. See Figure 6-2 for an example of an IO synchronization matrix.
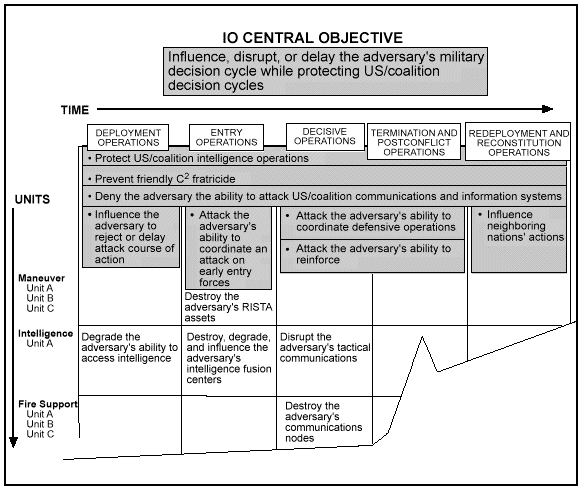
EXECUTION
Execution begins with tasking those elements that conduct IO missions. The G3/J3 controls and directs both the IO planning and execution phases of the process, with support from the G2 and IO element specialists on the staff. The keys here are--
- Selecting the best C2-attack capability for the best effect (deny, influence, degrade, destroy).
- Synchronizing the application of effects to reinforce the five elements of C2W, CA, and PA capabilities (not allow them to conflict). Similarly, protection of C2 nodes needs to be tasked to available means and/or additional protective tactics, techniques, and procedures (TTP) adopted by the force.
IO taskings normally become part of the basic order paragraph 3 concept of operations and coordinating instructions. Additional IO details are covered in a separate annex that consolidates applicable IO/C2W into one coherent operational discussion. When a separate IO/C2W annex is written, it should include an IO/C2W synchronization matrix that establishes time lines, responsibilities, sequence of actions, and desired effects.
As planning and execution take place, planners should consider a number of factors beyond strict combat capabilities. These include--
-
The opportunity cost of an action--that is, what is the trade-off
between attacking or destroying an adversary's capability now or exploiting
that capability for future gain? As an example, destroying key C2 facilities
may give the operational commander freedom of action by denying the enemy
effective C2 of his forces. However, the opportunity cost of this action
would be to deny national signal intelligence (SIGINT) systems a valuable
link to the opponent's NCA. Therefore, the national command level would lose
information about the adversary's national-level intent and resolve. Similarly,
destroying an air defense network may give the tactical commander local air
superiority, but it may also eliminate the only means the operational-level
commander has to track or identify enemy formations.
- Legal and policy restrictions and ROE--in order to understand their impact on the linkage between the levels of war. Target planners are required to know the ROE as well as the laws and policy governing the attack of certain persons, places, or things. How does the commander deal with the commercial computer network, the local/regional phone network, or the cellular data net that not only supports the military effort but also the civilian population, commerce, and industry? Other considerations include when and what information to release to the media, NGOs, and PVOs.
Planners must be aware that the counter-IO the adversary launches will likely target US civilian infrastructures. The mere threat of such actions may also generate significant effects, both real and psychological. For example, an adversary's announcement claiming the insertion of a virus into a particular banking institution's computer operation could trigger a panic with major economic repercussions, regardless of the adversary's actual execution of such an attack.
FEEDBACK
The fifth step is to set up a monitoring and feedback mechanism. A continuous damage or effects assessment process is critical in order for the commander to revise his continuing estimate of the situation and adjust operations. See Appendix A to develop C2W and IO-related planning products. The five-step planning process is illustrated in Figure 6-3.
EXECUTION
The force-projection cycle is an excellent framework to discuss how to execute IO. The packaging, timing, and employment of key IO activities is essential to attaining and maintaining information dominance in conducting operations across the full spectrum, to include OOTW.
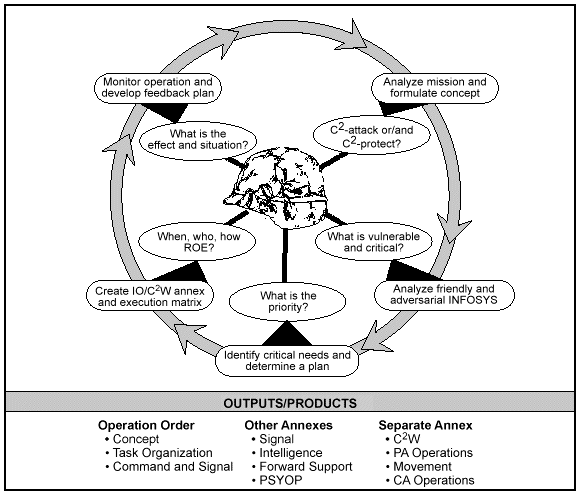
Force-Projection Operations
Our post-Cold War National Military Strategy calls for a primarily CONUS-based Army--one that is capable of rapid power projection on short notice to any region of the globe to decisively defeat a regional adversary. These force-projection operations follow a general sequence of stages that often overlap in space and time. IO considerations and actions apply to all force-projection stages. They focus on ensuring information support to battle command during all joint, multinational, and interagency operations and effective intervention against the adversary's C2.
In many situations, GIE organizations will be present in the AOR before Army forces arrive. They will often be well-entrenched, with an established logistical framework and long-standing coordination and liaison arrangements. For example, initially the media may know the AOR better than the military. As it covers the buildup, the media gains a thorough understanding of and forms its own perspective about the situation, particularly in OOTW. The projection of Army forces into the situation is of national interest, with national and international media watching from the moment forces arrive. CA and PA personnel need to deploy early to support the commander and the force in their interactions with these organizations. CA and PA operations not only reduce the potential distractions to a commander but also educate these organizations and facilitate their efforts to provide accurate, balanced, credible, and timely information to local officials and agencies, as well as external audiences. Some unique considerations apply for force-projection operations and OOTW.
The friendly communications infrastructure provides the means to integrate C4I capabilities starting from the installation power-projection platform with reach-back capabilities while en route, during initial entry, during buildup, throughout the operation, and during redeployment. The variety of conditions under which the Army is employed in the Information Age requires close IO coordination, integration, and synchronization from the strategic to the tactical level. Figure 6-4 outlines this concept. Force projection, supported by IO, is continuous and seamless and compresses time and space.
MOBILIZATION OPERATIONS
Mobilization is an information-intensive operation. Once mobilization is declared, the unit's activities include assembling personnel, checking readiness factors, and time-phasing operations to meet force deployment schedules. IO assist in synchronizing arrival, processing, certifying, and moving to final points of departure. The Army depends on information management resources in its sustaining base to accomplish the mobilization process. These resources include--
- The Standard Army Management Information System (STAMIS).
- FORSCOM's Mobilization Level Application Software (MOBLAS).
- TRADOC's Reception Battalion Automated Support System (RECBASS).
- DOD INFOSYS such as the Defense Joint Military Pay System (DJMS) and the Defense Enrollment Eligibility Reporting System (DEERS).
Most of these systems depend upon the NII for their operation. Many run on standard commercial platforms such as personal computers (PCs), reduced instruction set computing (RISCs), or mainframes. The systems could be expanded or enhanced during a crisis. Their dependence also underscores the importance of engaging the interagency process to help secure the NII from possible attack or compromise.
Intelligence activities during the mobilization phase focus on collecting intelligence on probable operational environments and potential adversaries. The staff performs the initial information-based IPB during peacetime.
C2W activities during mobilization are predominantly concerned with protecting information. Upon mobilization, protection of information is included in the commander's recall and assembly plans. C2-protect measures protect the availability, integrity, and confidentiality of unclassified and classified information necessary to support mobilization operations. During this stage of force projection, bits of information conveyed in nonsecure public and military radio transmissions, news releases, friendly conversations, telephone calls, trash, and so forth, permit news media personnel or hostile intelligence analysts to piece together US intentions and capabilities. OPSEC and INFOSEC aid the commander in preventing adversaries from collecting information of intelligence value.
PREDEPLOYMENT OPERATIONS
Commanders establish objectives and unit requirements to set the stage for predeployment activities and seek to preserve friendly assessments and decision-making capabilities. IO integrate the elements of C2W to mask deployment and enhance deception operations. Plans include--
- Engagement of the adversary's INFOSYS.
- Identification of tasks, C2W target sets, specific procedures, and coordinating instructions--all displayed within a detailed IO synchronization matrix.
These steps ensure the implementation of IO and set the stage for ongoing military actions.
PA operations during predeployment contribute to establishing conditions that lead to confidence in the Army and its readiness to conduct operations while remaining attentive to OPSEC and INFOSEC. As units are identified for possible or actual mobilization, public and media attention increases dramatically. PA operations contribute to a reduction in rumors, misinformation, and uncertainty on the part of soldiers, family members, and the public.
During the predeployment phase, tactical INFOSYS continue to be used less than fixed military and civilian systems for routine actions during predeployment. Military systems that link operational and strategic echelons, such as the DISN and the Defense Switch Network (DSN), are the primary dedicated military systems used. Intelligence, logistics, and operational planning require extensive coordination with outside agencies, other services, and so forth, to provide the data required.
Intelligence activities continue to revolve around establishing an adversarial data base and an information-based IPB. Component commands require national intelligence and weather data to support detailed planning. Before deployment, the commander's staff should develop CCIR, PIR, CMO, and RISTA plans.
C2W actions continue to focus on protecting information through exercising OPSEC procedures. With the support of the higher joint headquarters, as augmented by LIWA, C2W planners consider offensive actions to establish information dominance once the force begins to deploy. Close coordination with PA personnel is required during deception and PSYOP planning to maintain OPSEC and ensure such efforts are not targeted against friendly audiences and, most importantly, US, allied, or coalition media.
PA develops assessments for current and future operations. Planning continues for appropriate media inclusion (journalists accompanying units). PA implications of all aspects of the operation are considered to include media attention and public response. Synchronized PA programs contribute to increased soldier understanding, confidence, dedication, discipline, will to win, and public confidence in the Army. PA efforts focus on protecting and enhancing the public support of gravity.
DEPLOYMENT OPERATIONS
IO are necessary to establish the conditions for deploying forces into an AO. Deploying forces require near-real-time joint and/or interagency communications tailored for rapid deployment, en route operations, and links from strategic through tactical levels.
During the deployment stage, staff planning functions intensify. Contingency plans (CONPLANs) and PIR are updated, completed, or adjusted. Commanders and staff planners tap into joint and interagency planning systems and data bases, such as the Joint Operations Planning and Execution System (JOPES) and the Army Mobilization and Operations Planning and Execution System (AMOPES), to determine lift asset availability and sequencing. Intelligence requirements and assessments are continually monitored and adjusted. As forces begin deploying, commanders plan for the impact of force separation and reduced information support through low-capacity systems. They adjust their CCIR to those most critical to maintain situational awareness, training readiness, and mission accomplishment.
INFOSYS requirements for deploying forces demand home station, en route, and intertheater/intratheater communications that are secure, flexible, and deployable. These INFOSYS must be capable of interoperating with joint forces, civilian agencies, and multinational or coalition forces. INFOSYS support mission planning with multiple continuous intelligence and logistics links to the deploying/deployed force, home station, major commands, logistics agencies, and national and joint intelligence sources.
Deploying forces are highly dependent on CONUS-based intelligence, such as imagery and weather, derived from national or theater-based sensors. The forces require assured and survivable communications to numerous agencies. During deployment, echelons above division execute most of the C2W actions such as deception, PSYOP, and continued OPSEC.
ENTRY OPERATIONS
IO are necessary to establish the conditions for successful early entry. IO capabilities are deployed into a contingency area with a focus on their ability to gather the information required by the commander while denying the enemy use of his information and IO capabilities. Early entry operations vary by region and mission. In both unopposed and opposed entry, counter-RISTA operations are essential. Air and missile defense is key to successful counter-RISTA operations during the early entry period when forces are most vulnerable. Air and missile defense systems negate enemy airborne RISTA, EW, and C2 platforms while simultaneously protecting key geopolitical assets and the force's critical nodes from air and missile attack.
Unopposed Entry
Unopposed entry allows for greater use of IO capabilities. Early deploying assets focus IO on the adversary to support forward presence or host nation (HN) forces. Early entry forces rely on split-based communications with CONUS-based elements for most of their intelligence and communications support. Although HN or commercial systems may be available, planner awareness of statutory requirements regarding their use is essential.
Opposed Entry
When entry is opposed, commanders may have to rely on a limited number of INFOSYS to get the information they need to accomplish the mission. Because information requirements may well overwhelm the capability of available assets, commanders must clearly prioritize their information needs to best focus the use of these limited capabilities.
Working within the joint IW/C2W plan, army commands employ their C2W capabilities to satisfy assigned tasks. Successful opposed entry operations can be significantly enhanced by denying the adversary use of his INFOSYS through employment of C2-attack assets. C2-attack could include deceiving or overloading the adversary's INFOSYS and disrupting his use of the EMS.
DECISIVE OPERATIONS
Commanders visualize the battlespace and develop operational concepts that use common situational awareness and the ability to rapidly and accurately move information about the battlefield. The IO capabilities available to the unit permit surprise and the decisive defeat of the adversary from dispersed positions. Defeat of the enemy is usually accomplished most effectively by countering enemy strengths with dissimilar (asymmetrical) systems and methods. Units begin to conduct offensive C2W operations. This requires friendly commanders to exercise increased control over the tempo of battlefield activities. Tactical commanders leverage their information superiority to employ weapon systems, including joint assets, and to regulate the nature and tempo of enemy actions.
To optimize the flow of essential information, commanders prioritize their information requirements through CCIR and SOPs. The IOBS, however constituted, ensures that C2W, PA, and CA are integrated into the commander's concept of operation. This is accomplished as the G3 integrates his IO assets into the operational scheme to get the best possible picture based on the commander's intent. Moreover, the G3 leverages organizations and assets from the GIE, that is, joint and national intelligence assets, to complete the IPB mosaic. Often, the assets available are less than those needed to perform the desired IO. The commander provides the focus to prioritize these IO assets. Constant monitoring of enemy and friendly IO status ensures this information is included in situation updates, IPB, and the commander's RCP of his battlespace.
Media and public attention is usually more intense during this phase. PA operations include media facilitation, advising the commander on PA implications of the operation, as well as providing for internal and external audience information needs. PA personnel review strategic and operational information with PA implications, coordinate with CA and PSYOP, and facilitate releasable information.
Unity of effort and massing of combat power effects are enabled by enhanced information flow, both vertically and horizontally, among commanders and staff members and supported by military INFOSYS. Tactical units employ military information to fully integrate the systems, capabilities, and functions of the combined arms team into the conduct of decisive operations. Control of decentralized maneuver and engagement is achieved by optimizing the enhanced situational awareness and communication provided by digital connectivity. This ability allows tactical units the opportunity to avoid adversary strengths and detection means while moving into the most advantageous positions to permit the destruction of the enemy force in both offensive and defensive operations. Units exercise the capability to focus and mass the effects of indirect fires against the adversary and to synchronize their effects with maneuver. By employing highly maneuverable artillery, aviation platforms, suites of digital sensors, and intelligent minefield systems, maneuver units establish quick-fire sensor-to-shooter links that acquire, strike, assess, and restrike enemy targets at a high rate and level of lethality.
Enhanced situational awareness and communications capabilities allow the maneuver commander to conduct decisive strikes within the enemy depth by employing both organic and supporting fire systems. Commanders use C2-attack to destroy, disrupt, and exploit enemy INFOSYS. By providing the RCP at all echelons, IO facilitate the synchronization of all combat power across the BOSs. In conjunction with air and ground battle plans, commanders must select the proper vulnerable nodes and know whether to destroy or merely disrupt them and when to exploit through C2W.
Available IO assets may dictate the arrangement of forces on the ground. Coalitions may be formed with armies that have varying IO technical capabilities. Intelligence can be used to ensure the validity of target nominations, while the C2W planning process can ensure that the appropriate response is directed against that target.
Our present theory is to destroy personnel, our new theory should be to destroy commands. Not after the enemy's personnel has been disorganized, but before it has been attacked, so that it may be found in a state of disorganization when attacked.Extracted from J.F.C. Fuller's memorandum
"Strategic Paralysis as the Object of the Decisive Attack," May 1918
TERMINATION AND POSTCONFLICT OPERATIONS
IO enter a new phase upon termination of hostilities. The aftermath of war could leave a significant dislocation of the infrastructure and population in the area of conflict. The potential for renewed conflict should not be discounted. In these circumstances the protection of information by OPSEC, the hand-off of military information to other nonmilitary organizations, and even the continued collection of new information may become necessary. Certain military information is protected, while other military information is required to be released publicly to prevent further bloodshed and permit resumption of normal life. Conscious decisions in the orchestration of these competing demands exist as IO continue. For example, the presence of minefields and their location should be released to all parties to prevent civilian causalities.
Dislocations and damage following combat generate requirements for new information. Monitoring, relocating, and providing humanitarian assistance for displaced persons is as much an information problem as it is a logistical one. Destruction of physical infrastructures may dictate that for humanitarian reasons the US leave particular items of equipment in place that would otherwise be redeployed. Such equipment may include temporary bridges that replace destroyed ones, radio broadcast band transmission equipment, and electrical generation or water purification equipment. Information is critical in making these decisions. Further uses of such information are required to adjust Army data bases and unit readiness affected by these actions.
When combat operations bring an end to the conflict, deployed forces transition to a period of postconflict operations. The transition to postconflict operations can occur even if residual combat operations are still underway in parts of the AO. Therefore, adjustments to IO must be anticipated and planned to ensure a smooth transition during the critical period after the fighting stops. IO adjustments during postconflict operations focus on providing support for restoring order, reestablishing the HN infrastructure, preparing forces for redeployment, and continuing a presence to allow other elements of national power to achieve strategic aims.
The transition plan for postconflict operations prioritizes and plans for information requirements and required connectivity to support civil administration mission activities; CMO such as civil defense, humanitarian assistance, and populace and resources control (PRC); and unified planning with DOS, NGOs, PVOs, and HN officials and agencies. CA personnel are uniquely qualified to advise the commander on these activities that reduce postconflict turmoil and stabilize the situation until international relief organizations or HN agencies assume control.
Postconflict operations require close coordination between PA elements and those conducting CMO to ensure consistent, accurate dissemination of information. Internal information programs aid the transition to redeployment and reconstitution by reducing rumors and uncertainty. IO transition planning addresses the smooth retrograde of assets from the theater of operations, while considering the possibility of renewed hostilities. Tactical and mobile information assets should be replaced as soon as possible by the fixed communications and information infrastructure of the HN. Part of this stage may include transition of INFOSYS and operations to DOS, PVOs, NGOs, the HN, or other agencies that represent nonmilitary options to support HN rebuilding. Planning begins at this point for support of the redeployment of friendly forces and continued reconstitution of assets destroyed in the conflict or retained by the HN.
REDEPLOYMENT AND RECONSTITUTION
Normally, reconstitution and redeployment actions occur in a benign regional environment; however this is not always the case. Sensitivity to the effect information has on the population remains a concern. PSYOP and CA may be used to gain and continue support of the population. Information about Army operations and CMO can be disseminated through local, national, and international media. PA operations do not focus on directing or manipulating public opinion, but on providing accurate, timely information about operations. PA personnel take action when necessary to counter misinformation communicated via the GIE.
Intelligence collection may focus on nonbattlefield aspects of the current environment and the potential for new threats or adversaries to emerge. Commanders must remain sensitive to the potential vulnerability of critical nodes or systems to renewed adversary operations and be prepared to shift to alternative means if necessary.
In this stage, IO support the redeployment of assets no longer needed or needed for another mission elsewhere. Commanders plan and prioritize their IO to allow a smooth transition for redeployment. Postconflict requirements have a direct impact on the redeployment flow. INFOSYS must integrate contractor and HN asset capabilities into the redeployment flow.
Units must be rapidly reconstituted to premobilization levels of readiness. To ensure rapid replacement and refitting for new missions, units must identify lost or incomplete equipment because of the high probability of some information assets being left in theater or not yet replaced by the logistics system. Commanders must continue to emphasize INFOSEC during redeployment operations, especially in the event of ongoing hostilities.
Operations Other Than War
Military operations other than war usually involve a combination of air, land, sea, space, and special operations forces as well as the efforts of governmental agencies and nongovernmental organizations in a complementary fashion.Joint Pub 3-0
Army forces face complex and sensitive situations in a variety of OOTW. These range from supporting near hostilities in peace enforcement and peacekeeping operations; through drug interdiction, nation assistance, and humanitarian assistance; to support for US state and local authorities responding to natural disasters or civil unrest.
The primary tool for mission accomplishment in conventional military operations is the use of force directed against an adversary. In OOTW, however, such a threat may not be present or may not be clearly defined. The threat in these environments may be rogue elements, thugs, or even the adverse effects of the environment or a natural disaster. Hence, commanders employ a wider range of methods in less conventional ways that involve many more players to accomplish the mission. As such, IO capabilities to support the assigned missions may become essential for success. IO may be one of the most critical and acceptable means of achieving the assigned objectives because ROE may severely restrict the use of conventional military weapons.
In OOTW, as in other operations, military IO capabilities are not the only assets the commander may have available. Non-DOD, state, and local agencies; international organizations; military or paramilitary forces; and private organizations may also be available to contribute to IO. These players may offer a variety of services and resources, both military and nonmilitary, from within the GIE. This expanded field of individual and organizational senders and receivers of information, with varying methods of operation and focus, add a variety of INFOSYS needs. Interoperability, cooperation, coordination, and liaison may significantly increase resource requirements.
Historical Perspective
Projection of information is essential to successful military operations. During Operation Restore Hope in Somalia in 1992-1993, a peace operation, the 10th Mountain Division (LI) adjusted its mission analysis and tracking by establishing information dissemination as a BOS. This BOS included PA, PSYOP, and information for soldiers. The division considered full integration of these activities into all aspects of the operation as critical to success.
COORDINATION AND LIAISON
IO can be extremely complex and demanding. The Army is often faced with formidable infrastructure and interoperability challenges, both at home for domestic support operations and abroad for multinational operations, often in austere environments.
To provide coherence to information efforts, IO planning must be in sufficient detail and coordinated with all participating agencies. This requires extensive coordination and liaison. As an example, CA, PSYOP, and PA elements are able to use the same communications media with essentially the same messages but to different audiences. CA and PSYOP personnel address local populations and enemy forces, respectively, while PA personnel address US forces and national and international news media. Employment of C2W, intelligence, and INFOSYS capabilities requires coordination to ensure the synchronization of operations among participating organizations. Since military and civilian systems are often incompatible, military and supported agency communication planners must coordinate as early as possible in the operation. The Army may be required to coordinate IO with the following organizations:
United States Agencies
The Army may coordinate with non-DOD agencies in the broad spectrum of
OOTW, especially when the Army is placed in a supporting role to US agencies
during domestic support operations. FMs 100-19 and 100-23 and Joint
Pub 3-08 list and describe various agencies requiring consideration.
Among these is the United States Information Agency (USIA), which is especially
pertinent for the conduct of public diplomacy information efforts conducted
in foreign countries.
United Nations
The nations involved in specific UN operations rely on shared, relevant,
and pertinent data concerning the situation and parties involved in the
operation. IO help synthesize this data for a common understanding of threatened
interests, to determine relevant and attainable objectives, and to achieve
unified efforts. The methodology for exchanging intelligence information
should be conceived and exercised well before operations begin. US intelligence
personnel know and understand foreign disclosure policy and procedures. They
generally obtain necessary foreign disclosure authorization from the Defense
Intelligence Agency.
NGOs and PVOs
The number of NGOs and PVOs that may be found in a commander's AO could
be extensive. NGOs and PVOs can be valuable sources of information that
commanders involved in IO should consider. Commanders may also need to create
centralized control and liaison structures, such as CMOCs or emergency operations
centers (EOCs), to facilitate coordinated efforts with NGOs. See
FM 100-23-1.
Local Assets
Local assets may provide the capability to support and secure the temporary
setup of IO--telephone towers, satellites, ground cables, or other utilities
that would allow commanders to achieve assigned objectives or tasks. Also,
some localities may have the equivalent of non-DOD agencies. The US embassy
or consulate can be contacted for assistance in establishing liaison with
these agencies. These agencies may provide invaluable assistance in these
environments.
SPECIAL CONSIDERATIONS
All operations require gathering and dissemination information, as well as some form of intelligence. Since intelligence is a restrictive term, the preferred terminology in UN operations is information-gathering and dissemination. Accurate information is essential for planning PSYOP, OPSEC, EW, destruction, and deception operations.
By gathering information from soldiers, NGOs, PVOs, and civilians personally involved in the day-to-day operation, a commander can gauge the mission's effectiveness and better plan current and future IO. Maximum use should be made of open-source information. When practical, tactical information-gathering systems should be used so that information may be disseminated to UN/coalition forces, NGOs and PVOs, and other government agencies. However, parties to a conflict in peacekeeping operations or civilians in other operations may perceive information-gathering as intrusive or hostile. Therefore, intelligence activities must always be sensitive to legal constraints and/or maintaining the trust of the parties involved. The perception of impartiality is important for the protection of the peacekeeping force. Important intelligence considerations include the following:
- Every item of operational information becomes potentially important during OOTW.
- Personnel have to be information-conscious at all times.
- Participants must remain constantly alert to what takes place around them and to any change or inconsistency in the behavior, attitude, and activities of the military and civilian populace.
Information-gathering assets, sources, and agencies include those used in conventional operations as well as some that are not normally considered. Intelligence personnel will make traditional use of all organic or attached collection assets. However, they may also use other sources and agencies such as the local news media, NGOs, PVOs, international organizations, and exchanges with local police, governments, and militaries. Dissemination of intelligence is conducted using standard intelligence report formats. Intelligence personnel pass information to liaison officers (LOs) who pass intelligence products to parties requiring them in joint or multinational operations.
Although not peacetime operations, CA and PSYOP are critical operations that aid commanders in accomplishing their peacetime objectives. Commanders must understand CA and PSYOP abilities to support US and allied armed forces. PSYOP is a vital force employed to optimize the influence of US national policy on foreign target audiences, whether neutral, hostile, or friendly. In other operations, PSYOP provide the commander with the capability to project the purpose and mission of US forces and to influence target audience behavior to support the commander's mission. For PSYOP to achieve maximum effectiveness, planners must include them early in the planning process. In crisis situations, rapid production and dissemination of accurate information to the population are critical. PSYOP personnel can provide the commander with real-time analysis of the perceptions and attitudes of the civilian population and the effectiveness of the information being disseminated.
Signal support to OOTW missions requires the same detailed planning as any other operation. However, the scope and scale of planning may actually increase when the commander is considering or is confronted with--
- Nonmilitary INFOSYS such as commercial and local communications services. The operational principles of signal support apply.
- Interfaces among military and commercial communications, INFOSYS, and networks. Most civil and military communications systems are incompatible because of different equipment, frequency allocations, and usage parameters. For these reasons, military and civilian communications planners must exchange knowledgeable communications support personnel and compatible equipment to ensure connectivity is maintained between military and civilian operations centers. This exchange of personnel and equipment can occur at any level and should be implemented and modified as the situation dictates.