13 February 1997
Source: IEEE Spectrum,
February 1997, Special Issue, pp. 18-80
By TEKLA S. PERRY, Senior Editor
Hard currency is disappearing from many everyday transactions along the road to electronic money. (Text 8K)
By EDWARD W. KELLEY JR., Board of Governors, U.S. Federal Reserve System
The way electronics will fit into the evolution of money -- from acting as a niche player to wreaking major changes in payment systems -- has yet to be determined. (Text 13K)
By MARVIN A. SIRBU, Carengie Mellon University
CyberCash, First Virtual, GC Tech, NetBill -- these and other systems have been developed to enable electronic transfers of payments across the Internet. (Text 37K; 7 images 95K)
BY DAVID CHAUM & STEFAN BRANDS, DigiCash Inc.
Electronic cash can offer transaction privacy to honest users, affords convenient storage and transportation, and protects against loss. (Text 29K; 3 images 55K)
By PETER S. GEMMELL, Sandia National Laboratories
One method of making electronic cash transactions private for honest users but traceable by law enforcement agencies involves the use of trustees. (Text 13K; image 17K)
By STANLEY E. MORRIS, Director, Financial Crimes Enforcement Network
The speed and anonymity of electronic payment systems make them attractive to those pursuing illicit activities. (Text 7K)
BY ROBERT W. BALDWIN & C. VICTOR CHANG, RSA Data Security Inc.
Existing encryption-based security mechanisms can be combined to minimize a wide range of threats to electronic commerce. (Text 42K; 4 images 44K)
By CAROL HOVENGA FANCHER, Motorola, Inc.
A wallet full of cash, credit, and identification cards may, in the future, be replaced with two or three smartcards, each containing an IC, as a recent flurry of market tests and smartcard rollouts demonstrates. (Text 46K; 3 images 40K)
By MICHAEL C. McCHESNEY, Security First Technologies
While home banking has been around for some time Internet banking is a new concept, and has a number of advantages. (Text 36K; 4 images 89K)
By STEVEN M. H. WALLMAN, U.S. Securities and Exchange Commission
From stock offerings conducted entirely over the Internet, to the automation of traditional exchanges, technology is changing the way stock markets work. (Text 32K; 3 images 98K)
By ALFRED R. BERKELEY III, The Nasdaq Stock Market Inc.
This screen-based stock market has been particularly sensitive to the effects of new computer and communications capabilities. (Text 12K; image 33K)
By MIKE ter MAAT, American Bankers Association
Electronic cash can create profits for its issuers, and launch competition for todays government-controlled currency systems. (Text 31K; 3 images 34K)
By HOWARD ANDERSON, The Yankee Group
This visionary sees the e-money revolution as inevitable, with "e-mail for money" becoming as ubiquitous in the future as e-mail messages are already today. (Text 14K)
Paper version of this special issue available from IEEE Spectrum for $10.00.
Thanks to the authors and IEEE.
Hypertext by JYA/Urban Deadline.
By Tekla S. Perry
Senior Editor
I'm not an early adopter of electronic money. I don't use Quicken to balance my checkbook or pay my bills, I don't shop over the Internet ...yet. But on a day-to-day basis, hard currency has already been eliminated from most of my transactions. Many are billed directly to my credit card -- my monthly e-mail fees, my newspaper subscription, catalog purchases, the preschool bill. I also use a credit card for most transactions over US $10. I buy gas at automated pumps: it's faster to swipe a card myself than to walk into the gas station to pay. I pay for groceries in "scrip," a currency issued by my son's school for fund-raising purposes. Just about the only uses I have left for U.S. government currency are buying the occasional cup of coffee and splitting a lunch check with a friend
The authors in this special issue on electronic money paint a world from which even those uses of paper currency can be eliminated. A smart card, loaded with electronic money at an automatic teller machine or, eventually, on a home computer could be used for that coffee and bagel. Technology also exists for "electronic wallets" that can exchange money with each other, making it possible to split a restaurant check electronically or hit up a friend for a few dollars.
The boom of the World Wide Web has intensified interest in electronic money that can be transferred over the Internet. Site operators envision catalog shoppers browsing the Web and doing all their transactions on line; at the rate graphics download on my computer, I can't see that happening any time soon. But they also envision Internet money creating a new type of commerce -- that in information, paid for in fractions of a cent -- that would sustain hordes of Web sites that are currently bleeding red ink. Given a standard currency and an easy way of obtaining that currency on my computer, I wouldn't mind zapping off a few pennies every time I wanted the text of an article -- its cheaper than photocopying charges at my local library.
How will this be implemented? A host of technologies have been developed. Some are still theoretical, some in testing, and some in commercial use. Some involve electronic forms of "cash," others use debit accounts, others are credit-card based. The workings of these systems are explained by Marvin A. Sirbu, a professor at Carnegie Mellon University in Pittsburgh, David Chaum and Stefan Brands, chief technology officer and distinguished scientist, respectively, of Digicash BV in Amsterdam, and Peter S. Gemmell, a senior member of the technical staff at Sandia National Laboratories, Albuquerque, N.M.
The biggest CAUTION/SLOW sign on the road to electronic money is security. There's a significant chance that unauthorized persons will access financial information over the Internet and use it for fraud, and undetectable counterfeiting is also a real concern. So before electronic money becomes pervasive, security must be tight, yet the stuff be simple to use, with transaction details mostly transparent to the user. SET, a security standard for Internet transactions, was created by Visa and MasterCard. Robert W. Baldwin, the senior engineer at RSA Data Security, Redwood City, Calif., responsible for its SET effort, and C. Victor Chang, RSA vice president of engineering, detail today's technology in the rapidly advancing field of electronic transaction security.
Security concerns are also slowing down implementation of electronic banking over the Internet. Citibank chairman John Reed said at a recent conference on electronic money that it will take 50 to 70 years before most of the people who use banks do their business electronically. He indicated that Citicorp considers banking on the Internet off-limits until security issues are solved. But banking on the Internet has begun, with, some feel, strong enough security in place. Michael C. McChesney, chief executive officer of Security First Technologies, Atlanta, Ga., holds that point of view, and explains his firm's electronic banking technology.
As banking moves to the Internet, stock trading is not far behind. The first-ever Web-based initial public offering was conducted a year ago, by Spring Street Brewing Co. of New York City, and since then 30 companies have followed its lead. Traditional stock markets are moving to the Internet as well. Steven M.H. Wallman, a commissioner on the U S Securities and Exchange Commission, discusses that activity and Alfred R. Berkeley III, president of the Nasdaq Stock Market Inc., chimes in with Nasdaq's view of this evolution. (Both organizations are based in Washington, D.C.)
Perhaps the most active segment of the electronic money category in the past year has been smartcards, reviewed by Carol Hovenga Fancher, North American smart card strategic marketing engineer for Motorola Inc., headquartered in Schaumburg, Ill. Though one of the oldest forms of electronic money, in use in Europe for decades, todays generation of smartcards has generated new interest worldwide. Large tests were conducted this past year in the United States at the Atlanta Olympic Games, throughout much of Europe, in Iceland, and elsewhere, even as the technology of the cards themselves was questioned by researchers announcing a theoretical method of breaking algorithms related to smartcard security systems.
Most recently, as this issue went to press, attention was focused on the British-developed Mondex smartcard, with MasterCard International buying 51 percent of the international arm of Mondex International Ltd., London and seven U.S. companies -- Wells Fargo, Chase Manhattan, Dean Witter, AT&T, First Chicago NBD, Michigan National Bank, and MasterCard -- jointly forming Mondex USA and planning a U.S. rollout. Meanwhile American Express Co. has licensed the Proton card, designed by a group of Belgian banks.
All the same, while electronic transactions may simplify commerce for the user, they raise regulatory law enforcement, and economic issues. Today in the United States, where U.S. Comptroller Eugene Ludwig cautions against premature regulation, the government has not begun to regulate electronic money, but is certainly keeping a close eye on the evolving industry. The concerns of the government and economists are discussed by Edward W Kelley, Jr., a member of the Board of Governors of the Federal Reserve System, Stanley Morris director of the U.S. Treasury Department's Financial Crimes Enforcement Network, and Mike ter Maat, a senior economist with the American Bankers Association, Washington, D.C.
So is this world of electronic money coming soon? Howard Anderson, managing director of The Yankee Group, Boston, thinks so, and tells why. Is he right? Do you see electronic money taking over your computer and your wallet? Let IEEE Spectrum know, at http://www.spectrum.ieee.org.
An extensive tutorial on electronic money and Internet commerce appears in Digital Money: The New Era of Internet Commerce, by Daniel C. Lynch and Leslie Lundquist (John Wiley & Sons, New York, 1996).
A conference on the security of digital financial transactions will convene Feb. 24-28 on the island of Anguilla, British West Indies. To obtain program and registration information, see www.cwi.nl/conferences/FC97.
Edward W. Kelley Jr.
Board of Governors of the U.S. Federal Reserve System
Will electronic money become the new medium of exchange, or will it be confined to just a few special niches?
In the long history of how things get paid for, is electronic money the next step?If the issue is how money is transferred, that question is settled -- it is happening now But if it is the creation and acceptability of new forms of money, the jury is out.
Like so many other tools of civilization, money has evolved tremendously over the centuries. While change was glacially slow at first, the pace of evolution has recently been accelerating, and there is no reason at all to think that will stop. But what new forms might money assume? Will electronics take over, and if so, how soon will it do so?
Money has three functions in society, and how well electronics serves these functions will determine its future. First, money is a unit of account, or a way to measure and record value: a pig is worth X dollars. Second, it is a way to store value conveniently for future use; possession of a pig is replaced by possession of a bank account recorded in, and retrievable in, money. Finally, it is a medium of exchange; instead of having first to find a pig to trade for cloth, money buys cloth or a pig.
For money to fulfill these three functions, it must satisfy certain requirements. It should be easily and broadly recognizable and hard to fake (counterfeit), its value should be reasonably stable (a major matter indeed!) and it should be durable and not deteriorate (electronic pulses are potentially wonderful). Finally and crucially, it should be convenient and inexpensive to use (vital for its acceptance in daily commerce).
The history of money illustrates these points. It began, of course, with barter. In a primitive society a pig might be traded for a bolt of cloth. The obvious limitations of this kind of exchange led to the use of proxies for value. In societies near oceans, sea shells served in other places special stones; and later on, pieces of metal, often gold or silver, did duty and came to be shaped into coins. The development of printing spurred the use of paper notes. From this came checks, with which payments could easily be made over a distance, a major breakthrough. When the telegraph was invented, the technology for making remote payments developed further, as transfers became virtually instantaneous. Then a natural extension was the use of modern electronics and computers.
Today, money is transferred in a wide variety of ways. Most of the value moves nearly invisibly to consumers and businesses through what may be termed wholesale payment systems, such as the Federal Reserves Fedwire, and these systems are almost entirely electronic already. But most of the products under development are designed to serve the vast "retail" channels, which encompass the infinity of smaller transactions occurring daily throughout the economy.
How will electronics fit into this matrix of functions and requirements? The products being developed today fall into two groups, and it is important to distinguish between them because only one of them is a new form of money. Those referred to as electronic banking do not represent a new kind of money, but rather offer a new way to access a number of traditional bank services with traditional money. Such activities as bill paying and shifting funds among accounts over a telephone or computer connection belong here, and development is well along in this field. The many emerging types of stored-value cards and other media, however, do create a new money, as they represent an alternative to government-issued or -guaranteed instruments.
In stored-value systems, the liability of the issuer is recorded directly on the card, and a corresponding deposit account is not necessarily maintained for the individual card holder. Innovations of this type are coming along a bit more slowly. To be sure, some systems may involve both stored value and a deposit balance transfer capability, thus integrating the two types of products.
Predictions of an electronics-based cashless society have been around since the 1960s and, at least to date, it has not emerged. Consumers and businesses have proven quite conservative in their money management, relying heavily on tried and true methods even after more advanced techniques have become available. To one degree or another, this conservatism will likely be the case in the future as well. That said, why should the course of events be different now?
The characteristics of e-money and the speed of its advent will depend in large measure upon whether it serves the historic functions of money better than do its existing forms -- whether electronic cash does better as a unit of account, a store of value and a medium of exchange. How acceptable the new products are will be determined by the market and the classic economic factors of basic supply and demand characteristics. Suppliers will have to deliver a product that consumers want to use at a price that they are willing to pay, and that merchants see as a desirable additional way to conduct business.
In determining product prices, the cost factor is always crucial, and engineers designing the product's technical characteristics will have an important influence on these costs. Components will include the costs of cards themselves of terminals, of creating and maintaining software, of obtaining funds and of settlement, and (lest we forget) a profit margin. It is likely that the advance of technology will lower all of these costs continuously.
A long list of features, some essential and others only desirable, will determine the demand for the product. The degree to which these features are incorporated in new products will determine whether e-money does, in point of fact, represent an improvement.
Convenience will be key for everyone. For consumers, this will consist, among other things, of ease in obtaining cards and replenishing them, as well as plenty of opportunity to use them. Merchants will want to see fast and easy service requirements on the part of their staff and fast settlement of the amounts due to them. Privacy may be a tricky issue as consumers will want to keep the details of their transactions private, whereas merchants and issuers will want to ensure they capture an appropriate record of their transactions.
Then there is the all-important issue of safety for the store-of-value devices. Both consumers and merchants will want their stored-value systems to be simple in operation and error free, because neither will favor a device at all likely to somehow eliminate its own value through electronic malfunctioning.
Both consumers and merchants will also demand a high degree of financial stability on the part of the issuer. Otherwise an insolvency may leave the holder with a worthless asset.
All the items on that laundry list have significant technical dimensions, and these technical problems are well on the way to being solved. For instance, engineers have made solid progress in solving the hardware and software issues posed by stored-value cards. Chip cards can now be mass produced, and advanced cryptography techniques are incorporated into the operating systems stored in the chips.
Meanwhile, issuers are confronting the managerial, financial, and legal issues, which could prove far more difficult in many cases. For example, potential issuers are looking into the financial and legal structures that will provide their product with the greatest financial stability while at the same time avoiding the need for regulation, or at least minimizing their costs of complying with regulation.
Governments are keeping a watchful eye on all of this activity, chiefly through their finance ministers and central banks. The Federal Reserve, the central bank of the United States, is closely following several issues. First of all, the safety and soundness of the financial system, especially the banking system, are major concerns as instabilities there can disrupt the economy at large. On this point, the Federal Reserve is unalarmed by developments to date, because market forces should help ensure sound financial practices. After all, consumers and merchants will be most inclined to purchase stored-value products from those issuers who have implemented prudent financial structures and have taken steps to minimize the possibility of fraud.
Furthermore, the stored-value industry appears unlikely to be large enough to threaten the financial system
Then there is the need to protect against crimes such as fraud and money laundering, as well as to ensure the privacy and security of the financial activity of society. The Federal law-enforcement community is looking closely at those issues.
Over the longer term, there could be implications for the control of monetary policy, but I am confident that central banks will be able to adapt their monetary policy procedures to the growth of stored-value products, if the necessity arises. Perhaps most controversial in this context is who should be permitted to issue stored value and under what conditions. While all these issues require resolution, none seems to present insoluble concerns, and the Fed sees no present reason to jump in with preemptive regulations before any clear public policy requirements have been demonstrated. To do that could disrupt the socially beneficial entrepreneurial processes of the private sector and would imply that market forces could not do the job. We believe that they can.
How all this will evolve as time goes along is hard to predict. The large-value wholesale systems are fully electronic already, and while they will no doubt evolve over time, they are not the focus of creative energies in the private sector today. The electronic banking products designed to improve access to existing retail banking functions will almost certainly soon find a place in our financial activities. The stored-value or e-money products could at the least evolve to serve a special niche in small transactions .For larger purchases, the financial incentives may continue to lead consumers to use other means of payment, such as checks and credit cards. It seems unlikely that e-money will make major inroads in the existing order of the financial system for the foreseeable future, but innovation in this area may well lead to noteworthy new efficiencies for the payment system.
One thing I will predict with confidence :the forms of money will continue to evolve, as scientists and engineers continue to advance the applicable technologies.
____________________
About the author
Edward w Kelley Jr. took office as a member of the Board of Governors of the U.S. Federal Reserve System on April 20, 1990, to a full term ending Jan. 31, 2004, after completing an unexpired term from May of 1987. Before becoming a member of the Board, Kelley had been chairman of the board of Investment Advisors Inc., Houston. From 1959 to 1981 he was president and chief executive officer of Kelley Industries Inc., a holding company with subsidiaries in manufacturing, distribution, and business services. Kelley has also been a founding director of three banks in the Houston area.
Brian Madigan, associate director of monetary affairs at the Federal Reserve System, assisted in the preparation of this article.
Governor Edward W. Kelley Jr. of the U.S. Federal Reserve Board has delivered a number of speeches on electronic money. His remarks at the Digital Commerce Conference (May 6, 1996) are available from the Office of Publications, Board of Governors, U.S. Federal Reserve System, Washington, D.C. 20551, 202-452-3245. His speech at the CyberPayments '96 Conference, Dallas (June 18, 1996) can be downloaded from the Internet at www.bog.frb.fed.us/BOARDDOCS/SPEECHES/.
Alan S. Bliner, vice chairman of the U.S. Federal Reserve Board, addressed the topic of electronic money before the Subcommittee on Domestic and International Monetary Policy of the Committee on Banking and Financial Services, U.S. House of Representatives (Oct. 11, 1995). His remarks may be obtained from the Office of Publications, Board of Governors, U.S. Federal Reserve System, Washington, D.C. 20551; 202-452-3245.
MARVIN A. SIRBU
Carnegie Mellon University
A plethora of technologies and business models are in development to enable electronic payments
Since the advent of banking in the Middle Ages, bank customers have used paper-based instruments to move money between accounts. In the past 25 years, electronic messages moving through private networks have replaced paper for most of the value exchanged among banks each day. With the arrival of the Internet as a mass market data network, new technologies and business models are being developed to facilitate electronic credit and debit transfers by ordinary consumers.
These new systems include CyberCash (which is a gateway between the Internet and the authorization networks of the major credit cards) and the Secure Electronic Transactions protocol (a standard for presenting credit card transactions on the Internet), as well as First Virtual (a way of using e-mail to secure approval for credit card purchases of information), GC Tech (a payment system that can use credit or debit via an intermediation server), and NetBill (a public-private-key encryption system for purchasing information).
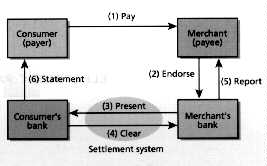
In today's banking world, money consists of ledger entries on the books of banks or other financial institutions. A checking account, also known as a demand deposit account (DDA), records deposits by the consumer and can be used, via the consumers instructions in the form of a check, to make payments to third parties. Typically, a check is written by a consumer authenticated by signature, and presented to a merchant, who may endorse it with a signature before presenting it to a bank for payment. If the merchant's bank and the consumer's bank are the same, it can simply transfer the funds on its ledgers from the consumers account to the merchants. If the payer and the payee keep accounts at different banks, the payee bank presents the check for settlement to the payers bank and receives the funds in return through a settlement system. Several private check clearinghouse systems, as well as the Federal Reserve system, provide settlement services in the United States [Fig 1].

[1] This simplified model shows the steps involved in processing standard paper checks used by a consumer to pay a merchant.
When checks are sent to banks for deposit, merchants do not yet know if consumers have adequate funds and therefore need to find out whether the checks cleared. Similarly, consumers receive statements from their banks showing which checks have been paid. Any discrepancy between bank records and those of the payers may indicate that forged checks were presented against consumers accounts.
This model works equally well when there is a negative balance in consumers' accounts, at least if the consumers' banks are willing to extend credit -- that is, to lend the consumers funds needed to pay off the checks.
Many banks in the United States and Europe provide such credit facilities, sometimes referred to as "overdraft protection." A credit card is another example of an account that lends money to the consumer.
The simple model below illustrates the major issues that must be addressed in designing an electronic credit or debit system.
Such a system does exist for paper checks. In the United States and Canada a bank identification code and account numbers are encoded in magnetic ink on the check. But the naming of accounts is not standardized internationally. Payees provide their account numbers when endorsing checks. The payers' banks match the signatures on checks with customers' signatures on file at banks. Integrity is ensured by the use of special paper and the practice of writing checks in ink with no alterations. The U.S. Federal Reserve system provides a vehicle for settlement and confirmation takes the form of periodic statements or special notices for bounced checks. If checks are presented in person or mailed in sealed envelopes they are generally protected from observation by third parties.
From a business perspective, payment systems differ in the warranties the different parties make and in the liabilities they assume. For example, the payers' banks are responsible for verifying signatures on checks. If this fails to happen, the payers are not liable for forged checks drawn on their accounts It is possible to cut the cost of the entire process if payment messages can be readily tied to the parties' accounting systems -- for instance, by including purchase order numbers or a consumers account number with a merchant on all checks. It may also be desirable to link payment to some proof that merchandise has been delivered. These links to other processes are among the principal benefits of electronic payments.
In a payment processing system, the cost of normal operations is frequently outweighed by the costs associated with exception handling. If a typical transaction costs US 5 cents to process, and the manual labor associated with handling errors and exceptions comes to an average of $25, even with an error rate of only two per thousand, exception costs will equal normal processing costs. As electronic processing drives down the cost of normal transactions, exception handling becomes relatively more significant. Payment systems must therefore be implemented to the highest standards of reliability, with automated procedures for recovering from errors whenever possible.
The credit card system was designed to provide immediate gratification of the wants of consumers by allowing them to purchase goods or services on credit. A credit card is a token of trust that transfers the risk of granting credit from a merchant to the card-issuing bank. Once a merchant has had a purchase authorized by the card issuer over the private authorization network, the merchant is assured of payment and the card issuer assumes responsibility for billing the consumer and collecting the money. Settlement takes place later, when the merchant periodically submits a batch of authorized transactions to the merchant's (acquiring) bank for settlement with the card issuer. But the issuers assumption of risk is limited, however, to "card-present" transactions, such as those taking place in retail stores. When a merchant accepts a credit card by mail or phone ("card not present"), the card issuer accepts only the risk of nonpayment; the merchant bears the risk of fraudulent card usage. Merchants pay the costs of credit card use because selling on credit expands their business. Under U.S. law, a consumers liability if someone else fraudulently uses the consumers card is limited to $50 [Fig. 2].
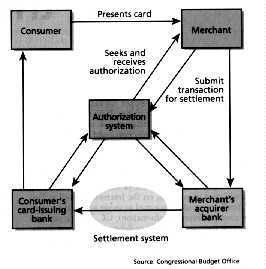
[2] In this model of credit card transactions, consumers present their cards to the merchants who submit the card numbers and transaction details to the authorization system, which either approves transactions directly or routes the requests to the card issuing bank for approval. Periodically -- for example, at the end of the day -- merchants submit details on approved transactions to their banks. This information is submitted to the card association for settlement after a bank nets out transactions for which it serves as both card issuer and acquirer.
In a card-present transaction, the merchant validates the payers signature by matching the one on the back of the card against the one on the charge slip. Integrity is protected by the device of giving the consumer a carbon copy of the slip. The consumer's account number is verified by the embossed number on the credit card. Settlement is handled by card associations (such as Visa and MasterCard). The merchant receives immediate confirmation of a transaction while submitting it for authorization by way of the card associations private data network.
When a catalog sale takes place by mail or phone, the merchant has no way of verifying the consumer's right to use the card number proffered At best, the merchant can request the consumer's billing address and receive an address verification. In effect, a credit card purchase requires only that the card number be conveyed from buyer to seller. For this reason, consumers are asked to protect their credit card numbers.
While conventional checking and credit card systems may seem quite similar the legal meaning of credit card and check payment differ significantly Credit card companies warrant their merchants; a person can challenge a credit card charge if dissatisfied with the goods. Checks provide no such recourse. If a person buys a plane ticket on an airline with a check, and the airline goes bankrupt before the ticket can be used, the unlucky purchaser becomes an unsecured creditor, behind many other claimants. By contrast, someone who pays for a ticket with a credit card may claim restitution from the card-issuing bank, and the card issuer in turn is entitled to redress from the airline's bank, which must stand behind the airline.
Payment systems vary significantly in their allocation of liability and in the warranties made by the different parties. Technical mechanisms have a strong influence on the willingness of parties to assume liability. If only the payers bank can verify a signature on a check, the merchant or payee bank will not assume any liability for fraudulent signatures. But if public-key-based "signatures" make it possible for a merchant to verify them on an electronic check, merchants can be expected to undertake verification as they now do in card-present transactions.
Translating checks or credit card transactions to the Internet requires finding electronic and business model equivalents for the functions described above.
Signatures and confidentiality are the two biggest problems in creating digital payment instruments. These issues are typically handled with some form of cryptography. The use of public-private-key pairs allows a message to be "signed" digitally and verified by anyone who has the public key. Some form of public-key infrastructure, such as certificates, must be employed to associate a named user or an account unambiguously with a particular public key. Message digests provide integrity.
Most payment systems require special consumer and merchant software to prepare and process electronic payment messages. Although the consumer software is often described as an "electronic wallet," that term is misleading; funds are never kept in the wallet, which acts rather as an electronic checkbook for signing payment orders -- managing keys, performing cryptographic operations, and formatting messages, as well as acting as a check register for keeping track of transactions.
The use of credit cards over the phone for catalog shopping is well established. Some of the first Internet systems propose to extend that model to shopping from Web-based catalogs.
CyberCash Inc., Reston, Va., implemented a system for protecting credit card presentation on the Internet in April 1995. The system was one of the first of its kind. The company, which provides software to both consumers and merchants, operates a gateway between the Internet and the authorization networks of the major credit card brands. As Nathaniel Borenstein, chief technical officer for First Virtual Holdings Inc., San Diego, Calif., noted, "Debugging obscure problems with incompatible implementations of Internet protocols is not a core competence of most financial institutions" -- hence the role for a gateway service.
The consumer begins by downloading the wallet software, which supports encryption and transaction record keeping. Like a physical wallet that may hold a number of credit cards, the software wallet can be used by the consumer to register several credit cards. Another software package provides similar services to the merchant. Messages are encrypted using a random symmetric key, which in turn is included in the message encrypted under the recipient's public key The CyberCash public key is built into the wallet and merchant software. Consumers generate a public-private-key pair when they register credit cards with the wallet software, and the public key is sent to CyberCash, where it is maintained in a database. While consumers, merchants and CyberCash all have public-private-key pairs, only CyberCash knows for certain everyone's public key. As a result, the company can exchange information securely with consumers or merchants, but they communicate with one another in the clear, relying on CyberCash to authenticate all signatures [Fig. 3].
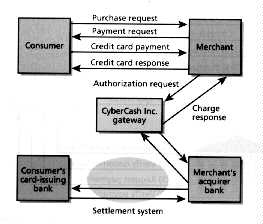
[3] CyberCash Inc., Reston, Va., provides consumer software, merchant software, and a gateway to support the secure communication of credit card transactions over the Internet.
When the time comes to make a purchase, the consumer requests the item desired by selecting it with a Web browser. The merchant's server sends the wallet software a cleartext, signed payment-request message that describes the purchase and indicates which credit cards the merchant accepts. The wallet software thereupon displays a window that lets the consumer select which credit card to use, and approve the purchase and the amount.
A credit card payment message, including a signed and encrypted description of the transaction, along with the consumer's credit card number, is sent back to the merchant, which forwards the payment message, along with the merchant's own signed and encrypted description of the transaction, to the CyberCash gateway. There, CyberCash decrypts and compares the two messages and their signatures. If they match, it submits a conventional authorization request and returns the charge response to the merchant, whose software confirms the purchase to the consumer's wallet software (credit card response). Additional messages cover refunds, voiding transactions, capture, and status inquiries.
CyberCash operates its gateway as an agent of the merchant's (acquiring) bank. Thus it must be trusted to decrypt the information for resending over conventional authorization networks.
Since the information is encrypted under CyberCash's public key, the merchant does not actually see the consumers credit card number -- a procedure that in theory cuts the risk that customer credit card numbers will be abused. In practice, so many catalog companies organize their customer marketing records by credit card numbers that an acquirer usually authorizes CyberCash to provide them to merchants on request.
In February 1996, Visa and MasterCard announced their joint support of a standard protocol, dubbed Secure Electronic Transactions (SET), for presenting credit card transactions on the Internet. SET is designed to operate both in real time, as on the World Wide Web, and in a store-and-forward environment, such as e-mail. As an open standard, it is also designed to permit consumer, merchant, and banking software companies to develop software for their respective clienteles independently and to have them interoperate successfully.
In the CyberCash protocol, only CyberCash knows everyone's public key. SET, however, assumes the existence of a hierarchy of certificate authorities that vouch for the binding between a user and a public key. Consumers, merchants, and acquirers must exchange certificates before a party can know what public key to employ to encrypt a message for a particular correspondent [Fig. 4].
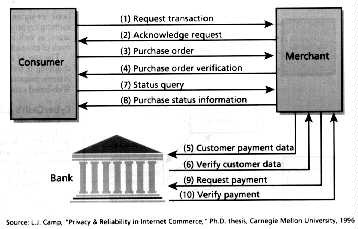
[4] The operation of the Secure Electronic Transaction (SET) protocol relies on a sequence of messages. In the first two, the consumer and merchant signal their intention to do business and then exchange certificates and establish a transaction ID number. In the third step, the consumer purchase request contains a signed hash of the goods and services order, which is negotiated outside the protocol. This request is accompanied by the consumer's credit card information, encrypted so that only the merchant's acquiring bank can read it. At this point, the merchant can acknowledge the order to the customer, seeking authorization later (steps five and six) or perform steps five and six first and confirm authorization in step four. Steps seven and eight give the consumer a query capability, while the merchant uses steps nine and ten to submit authorizations for capture and settlement.
Although the software industry is moving rapidly to implement SET, the protocol poses significant problems for banks. Card issuers must invest considerable sums to have public key pairs and certificates issued to their card holders. Yet the benefits to the SET card issuers are not clear. A standard protocol may reduce software costs to merchants and consumers, as well as inhibit merchant fraud, but the cost of such dishonesty is borne by the acquirers, not the card issuers. What is more, it is not clear that SET will generate significant new credit card volume, as opposed to merely displacing mail and telephone orders. The card associations suggest that SET transactions, like card present ones, should involve lower payments to card issuers Thus a shift from telephone orders to SET could actually reduce the revenues of card issuers, while increasing costs by requiring them to issue certificates. Aligning benefits with costs will require a reallocation of the merchant discount between issuers and acquirers, a politically difficult task for card associations.
First Virtual provides a mechanism that lets information providers accept credit cards for Internet purchases without resorting to cryptography. Consumers establish account IDs with First Virtual and fax or telephone their credit card numbers to it. To buy information, consumers present those account IDs to merchants, who then connect to the First Virtual server to verify that IDs are valid if so the information is sent directly to the consumers. The server then sends them an e-mail message asking if they are willing to pay for the information. Consumers e-mail a reply indicating "yes," "no," or "fraud" If the answer is yes, First Virtual submits the user's credit card number through its acquirer, and the consumer's card is charged. After holding the funds for 90 days, the company transfers them to the merchant by means of an automated clearing house.
The First Virtual model has several key premises. First, consumers do not really know if they want a piece of information until they have looked at it. Second, the cost of sending information electronically "on approval" is negligible, so a merchant has lost very little if a consumers answer is "no." Third, most consumers are honest: they will not systematically order goods and then answer "no" even when they are satisfied. (As an added deterrent to dishonest behavior, First Virtual will cancel a consumer's account if the pattern of usage suggests abuse.) By not charging consumers until they are satisfied, the system eliminates the cost of reversing charges for information that was not delivered as a result of network or computer problems.
Since the request for payment approval comes by e-mail, while goods are typically delivered over the Web, First Virtual believes that its model is so hard for an attacker to abuse that the risks are justified. Moreover, because the company delays payment to merchants for 90 days, consumers have plenty of time to discover fraudulent charges on their credit card statements, in which case First Virtual can easily reimburse the credit card with the funds it is holding.
In the First Virtual model, naming is provided by the account ID. In lieu of signatures, the company relies on the integrity of the Internet's e-mail infrastructure to ensure that a real consumer is answering yes or no. There is no message confidentiality, except that the account IDs may be viewed as pseudonyms. Confirmation is provided by e-mail and credit card statements. Settlement is handled first by the credit-card provider transferring payment to First Virtual and then First Virtual transferring payment to the merchants.
The company has been in operation since October 1994. It claims more than 180,000 consumer accounts.
Beginning in the early 1970s, banks began searching for ways to reduce the costs of check processing (6.5 cents -13 cents per item) by handling payments electronically. In direct payroll deposit, an employer sends a list of payroll payments to its bank, which then transfers funds to the employees' accounts at their banks through one of several automated clearinghouses (ACH). Consumers use direct payment to deal with recurring bills, such as utility, mortgage, and auto loan payments. In 1995, four ACH operators -- the Federal Reserve, the New York Clearinghouse, the Arizona Clearinghouse, and VisaNet ACH Services -- handled 2.9 billion transactions worth $13 trillion on their private electronic networks. The cost to banks was only half of what they would have spent processing checks manually. Payers and payees saved even more.
For both direct payroll deposit (used today by more than 45 percent of the U S. workforce) and for direct payments, transactions begin when a large organization sends a batch file or tape to its bank with a list of payments or requests for payment. Because this is a batch system it can take as many as three days for a payee to receive confirmation that a payment has cleared. The existence of these ACH systems for settlement between banks provides a strong base on which to build consumer-oriented electronic payment systems that can accept individual electronic requests for payment originating with consumers.
On the Internet, a paper check can readily be replaced by a digitally signed message -- that is, an electronic check. A consortium of banks working through the Financial Services Technology Consortium (FSTC) Inc. has demonstrated a prototype electronic check system that maps directly into the model described above for conventional checks. The payer uses a secure processor, in the form of a PC card, to generate a digitally signed payment instruction, or "check," that is transmitted to the premises of the merchant where it is "endorsed" digitally before it is sent on to the merchants bank. There, the check can be settled through an existing ACH [Fig. 5]. Other scenarios are also supported, for example, payers can send electronic checks to their own banks which would then transfer funds directly to the payees' banks.
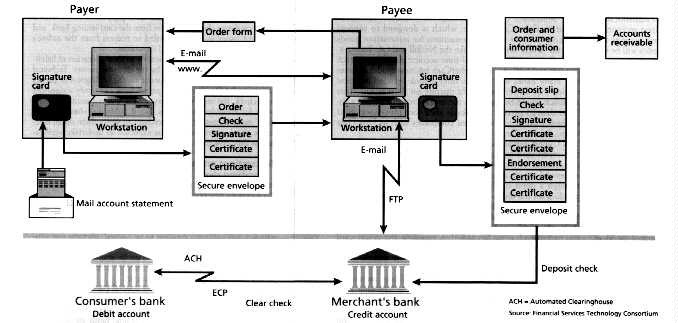
[5] In the electronic check concept developed by Financial Services Technology Consortium Inc., consumers uses smartcards or secure processors to compose and sign electronic checks. A check is sent, together with the consumers' public-key certificates and transaction details, to the payee for endorsement. The payee then adds its own signature and certificates and sends the check to its bank for deposit. The results of transactions are reported to both merchants and consumers.
Standards for conveying invoice and remittance information so that payments can be readily linked into accounts payable and accounts receivable processing systems are an important component of the electronic check concept.
The FSTC model assumes that public keys and certificates are widely available, with banks vouching for their customers and associations of banks, such as an ACH, vouching for one another. The insistence on a hardware token for protecting a private key is designed to provide a high level of protection against such threats as Trojan horse software.
To the extent that FSTCs electronic checks rely on the conventional ACH system for clearing, they cannot give the merchant immediate payment confirmation of the sort provided by credit card authorization. CyberCash, Carnegie Mellon University, and GC Tech have introduced, or are developing, low-cost debit payment systems that give a merchant an immediate assurance that the payment will go through
These systems provide a service model based on the concept of an on-line bank account, with immediate posting of transactions so that payees can get real-time confirmation that funds are available. In addition, they offer an interface to existing electronic funds-transfer mechanisms, including both ACHs and credit cards, so that consumers can easily transfer funds between their primary banks or credit accounts and their Internet payment accounts. Furthermore, these systems aggregate many on-line transactions for batch settlement over traditional settlement networks. They differ in the order of steps required for a transaction, in the consumer protection they provide in the event that goods are not delivered, and in the balance they strike between computationally expensive public-key cryptography and the use of shared-key cryptography.
GC Tech SA, headquartered in Paris, France, bases its business model on turnkey payment systems software for banks and other financial institutions [Fig. 6] The intermediation server in the GC Tech model maintains a "ledger" of consumer funds on account in the payment system. These funds may actually be on deposit at the consumers bank, but their disposition is accounted for on the intermediation servers books. Account funding may take the form of a charge against the consumer's credit card or a transfer from the consumers checking account to the payment system account. A consumer opens an account by downloading the wallet software and specifying a credit card used to fund the account.
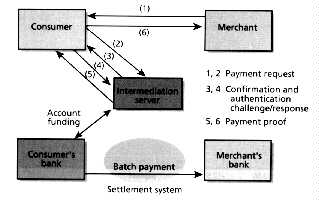
[6] The payment system protocol from GC Tech SA, headquartered in Paris, France, revolves around an intermediation server that maintains account information for consumers and merchants. Merchant requests for payment are relayed by way of consumers' wallets to the intermediation server, which authenticates the consumers and returns through them a confirmation to the merchant that he will be paid.
When the consumer has selected a product for purchase, the merchant responds with a digitally signed payment-request message that is sent to the consumer's electronic wallet, which verifies the terms of the transaction and forwards the message to the intermediation server. The server then issues an authentication challenge to the consumers wallet software. Upon receiving a correct response, the server debits the consumers account and credits the merchant. Accumulated merchant credits will be settled in a single periodic batch transaction. If the consumer has sufficient funds, the server returns a digitally signed proof of payment (PPT) to the consumer's wallet software, which forwards it to the merchant. Assured of payment, the merchant can now deliver the goods.
The GC Tech cryptographic model assumes that the intermediation server and the merchant have public-private-key pairs, while consumers have only a PIN number When the consumer forwards the proof of payment to the server, it proposes a session key encrypted under the server's public one. This session key is used to encrypt the authentication challenge and response, as well as to protect the PIN from disclosure. The proof of payment, signed by the servers private key, can be independently verified by both consumers and merchants. This model eliminates the need to issue and manage certificates for consumers.
Various entities are expected to use the GC Tech system, marketed under the brand name GlobeID. The GlobeID operator in France is Kleline SA, a joint venture operated by Moet Hennessey Luis Vuitton SA and Compagnie Bancaire SA, all three of which are in Paris. U.S. operations are expected to start in early 1997.
NetBill, a system under development at Carnegie Mellon University (CMU) Pittsburgh, in cooperation with Mellon Bank Corp., also in Pittsburgh, is optimized for delivering such information goods as text, images, and software over the Internet. Its developers, who include the author, have stressed the importance of guaranteeing that consumers receive the information they pay for. To that end, consumers are not charged until the information has actually been delivered to them. Similarly, merchants are guaranteed payment for goods delivered. The basic NetBill protocol has eight steps, beginning with the authentication of identity (using public-key cryptography) and ending with the transmission of a decryption key to the consumer so that the information being purchased can be decrypted and presented [Fig. 7].
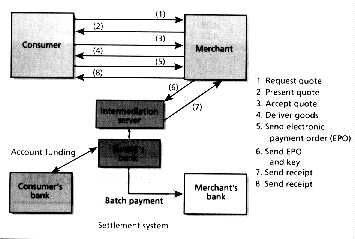
[7] The NetBill payment protocol has eight steps. In the first, the consumer and merchant authenticate each other using their public-key certificates and establish a symmetric session key to protect the privacy of subsequent messages. The first message requests a quote based on the consumer's identity, to allow for customized per-user pricing, such as volume discounts or support for subscriptions. If the quote (step two) is accepted (step three), the merchant sends the digital information to the consumer (step four) but encrypts it and withholds the key. The consumer software constructs an electronic payment order (EPO) describing the transaction and including a cryptographic checksum of the goods received. The order is signed with the consumer's private key and sent to the merchant, who verifies all its contents, appends the key for decrypting the goods, endorses the EPO with a digital signature, and sends it on to the NetBill server. The NetBill server verifies funds in the consumer's NetBill account, debiting the consumer and crediting the merchant, and a digitally signed receipt, including the key to decrypt the goods, is sent first to the merchant and then on to the consumer. The consumer software can now decrypt the purchased information and present it to the consumer.
In this system, consumers are not charged until the (encrypted) goods reach them. At the same time, if there is not enough money in the consumers account, the transaction will he rejected and the key never delivered, preventing the consumer from using information that has not been paid for. The merchant's endorsement of the electronic payment order also serves as a warranty that what was received by the consumer is what the merchant intended to deliver. In the unlikely event that the merchant or client machine goes down after the consumer has been charged but before the key is delivered, the consumer can request a copy of the receipt -- which contains the key -- from the NetBill server.
Note the contrast in message flows between the GC Tech and NetBill systems. GC Tech requires merchants to communicate with the intermediary by way of the consumer's software. In a NetBill microtransaction, only the merchant talks directly to the accounting server.
NetBill will fund its accounts by charging the credit cards of consumers to put spending money in their NetBill accounts. These funds will be held at NetBill's bank. As merchants accumulate credit balances, funds will be transferred via VisaNet to the merchants' banks.
CMU and Mellon Bank expect to launch a commercial trial of the NetBill system in the first half of 1997. Transaction fees, paid by the merchant, are expected to range from 2.5 cents on a 10 cent transaction to 7 cents on a $1 transaction.
In September 1996, CyberCash Inc., Reston, Va., introduced its CyberCoin service, which is designed to support low-cost (25 cent to $10) transactions for information goods over the World Wide Web. Like the NetBill and GC Tech systems this one relies on a real-time account database to track Internet transactions. The CyberCash business model assumes that many banks will want to offer a bank-branded payment service that CyberCash would operate on their behalf. This approach would be similar to the recent trend in credit cards: fewer than 25 percent of banks do their own processing; most of them leave it to specialized companies such as First Data Corp., Atlanta. Ga.
A CyberCoin account can be "loaded" either by a charge to a credit card or by a transfer from the consumer's checking account. In the latter case, the transfer is handled in one of several ways as an ACH transaction, by direct access through a debit or ATM network, or by other means. Depending on the mode of access and the user's level of authorization, funds may become available immediately or held for as many as three days until the transaction clears While it is less costly to the intermediary to obtain the funds through the clearing house -- thus avoiding the credit card discount fee -- consumers are likely to prefer credit cards that give them instant access to the funds and 30 days before they have to pay the bill.
In the CyberCoin system, like the NetBill one, merchants deliver the goods encrypted and provide the key only after payment is confirmed. But rather than using RSA digital signatures on every small transaction, the CyberCoin system uses asymmetric cryptography only to load accounts and establish a session key. Individual transactions are then signed with this symmetric key, thus reducing the data processing burden.
CyberCash has established partnerships with a number of important players. Netscape, for one, has agreed to bundle the CyberCash wallet software with its browser software products.
Payment systems can be expected to go on proliferating for the next several years, until the market determines the most desirable combinations of functions, price, and performance The paper world, after all, has many different instruments, which embody different tradeoffs among risk, cost, complexity, responsiveness, and the time until the transaction is final. The same variety should be expected in electronic credit and debit systems.
Yet new technologies uncover new ways to distribute risk, liability, and cost among the parties to a transaction, so that new financial instruments with no comparable paper analog, are also to be expected They will take somewhat longer to develop, however, as they require changes in regulatory assumptions, case law, and participant behavior, all of which evolve much more slowly than technology does.
____________________
About the author
Marvin Sirbu holds a joint appointment as professor in the departments of Engineering and Public Policy, the Graduate School of Industrial Administration, and Electrical and Computer Engineering, at Carnegie Mellon University, Pittsburgh. In 1989 he founded the university's Information Networking Institute, which is concerned with interdisciplinary research and education at the intersection of telecommunications, computing, business, and policy studies. Before joining Carnegie Mellon in 1985, he taught in the Sloan School of Management at the Massachusetts Institute of Technology, where he also directed a research program on communications policy.
Providers of Internet payment systems maintain extensive Internet Web sites replete with information about their systems: CyberCash (www.cybercash.com/), FSTC (www.fstc.org/), NetBill (www.ini.cmu.edu:80/netbill/), First Virtual (www.fv.com:80/), GC Tech (www.gctec.com/), and SET (www.mastercard.com/).
B. Clifford Neuman and Gennady Medvinsky discuss on-line payments in "Requirements for Network Payment: The NetCheque Perspective," in Proceedings of the IEEE Compcon '95 (March 5-9,1995), pp. 32-37.
The U.S. Congressional Budget Office has published a report on cyberpayments: Emerging Electronic Methods for Making Retail Payments (Government Printing Office, Washington, D.C., June 1996).
"Privacy & Reliability in Internet Commerce" is the subject of L. J. Camp's doctoral dissertation (Department of Engineering and Public Policy, Carnegie Mellon University, Pittsburgh, Pa., August, 1996).
David Chaum and Stefan Brands
DigiCash Inc.
Electronic equivalents of traditional cash payment systems are being launched worldwide
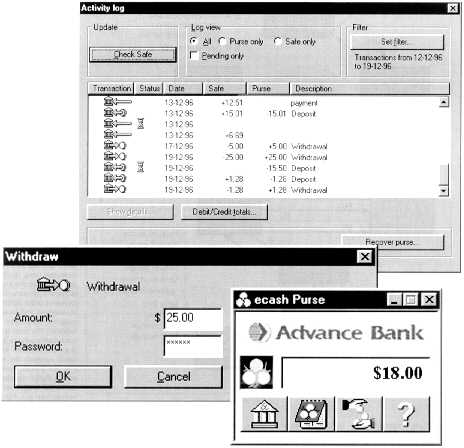
Customers of Australia's Advance Bank can avail themselves of its electronic cash software. The topmost screen shows transaction history -- personal information stored on the user's computer and not accessible by the bank or by anyone else.
The bottom screen shows the user interface. The readout states the amount of Australian dollars stored in the form of this electronic cash on the user's computer. The buttons access [from left] bank account information, the log of transactions, payment controls, and help system.
The remaining screen shows the user withdrawing 25 Australian dollars from the bank onto his or her computer. The password unlocks the user's secret key, which is then used to authenticate the withdrawal.
The interest in electronic replacements tor traditional forms of payment has exploded in recent years. In addition to many field trials tor value stored in chips on plastic cards (smartcards), many major software, telecommunications and financial services organizations are working on their own electronic payment techniques. While most of these aim at enhancing credit cards, a few companies have gone further and developed electronic replacements of traditional cash payment. However, the extent to which the different systems succeed in preserving the unique benefits of traditional cash and exploiting the new mediums advantages varies substantially.
Traditional cash money is a bearer instrument. It allows instantaneous payment from person to person. Cash payments are not normally traceable by a third party and therefore offer privacy. On the other hand, transporting, protecting, and refreshing coins and bank notes make them very costly for banks to handle. Bank notes can be forged on sophisticated color copier machines, coins are too heavy to carry around in any large number and both are easily lost or stolen. Because coins are virtually indistinguishable, and coins and bank notes can be passed from person to person many times without the involvement of a bank or other third party, cash is the preferred method of payment in criminal activities like extortion, money laundering, and bribery. Another inherent shortcoming has become particularly confining of late: the requirement for physical proximity of payer and payee.
The introduction of debit and credit cards has helped to overcome many of these problems. With these payment forms the actual value resides at all times within the banks and so the risks of large-scale theft and loss are reduced. A fundamental problem of these payment forms is that payments must be verified on-line by the bank; this makes transactions more expensive and can lead to unacceptable delays. Another problem is that the actual transfer of value is performed by banks, from source to destination account, and thus payments are inherently traceable. This traceability enables intensive profiling of spending behavior and, by inference, all sorts of other characteristics on personal information. Data protection laws can offer only limited protection against criminal use of spending and inferred habits, since such use typically becomes visible (if at all) only once the damage has already been done.
Electronic cash can combine the benefits of traditional cash with those of payment by debit and credit card, while circumventing both their shortcomings. As with traditional cash, electronic cash should have high acceptability and be suitable for low-value payment from person to person. With the possible exception of on-line payment platforms such as the Internet, it is preferred that payments be verifiable off-line without the banks involvement, for reasons of cost-effectiveness and speed. To facilitate electronic cash payments over the phone and the Internet, physical proximity of payer and payee should not be necessary.
Moreover, electronic cash should offer privacy of payments. In particular, payments by an honest payer should be untraceable, and information about transaction content should remain privy to payer and payee. Yet a payer ought always to be able to trace the payee; traceability suits electronic cash just as little to extortion, money laundering and bribery as a check or wire transfer. Lastly, as with payments by debit and credit card, electronic cash should be convenient to store and transport, while protecting users against loss, theft, and accidental destruction.
Each participant in an electronic cash system is represented by at least one hardware device, equipped with a chip having computing capabilities and nonvolatile memory. How to embody the devices depends on the target payment platform (say, a PC, possibly in combination with a PC Card or a smartcard, may be used for Internet payments, while a hand-held device with display and keyboard is more appropriate for on-the-street payment); the offered functionality (smartcards may be most appropriate for purposes of cross-platform portability); and the required security and privacy levels. When the holder of an account at a bank that issues electronic cash wants to withdraw some of it, his computing device engages in an execution of a withdrawal protocol with a computing device of the bank, when connected to one of its terminals (by direct or infrared communication, dial-in, the Internet or other methods). At the end of the protocol execution the computing device of the account holder holds an amount of electronic cash, represented in some suitable form, and his bank has charged the account holder by taking an equivalent amount of traditional money out of his bank account and moving it into a float pool; electronic cash is pre-paid by the account holder
To transmit to a payee who accepts electronic cash issued by the payer's bank, the account holder connects his computing device to that of the payee (again, by direct or remote communication), and the two computing devices execute a payment protocol. As a result, the representation of the electronic cash amount held by the account holder's device is adjusted to reflect the new amount. In the case the payers bank is not involved in the payment, the payees computing device should correspondingly represent in some way the received payment amount; this is called an off-line payment. Otherwise, the payee must communicate with the bank during the payment; this is called an online payment.
Ultimately, a party holding electronic cash will need to sell it back to the issuing bank. Redemption is needed in most systems because electronic cash received in one payment cannot be reused in subsequent payments, or can be reused only up to a predetermined number of times. To this end, the party connects his computing device to a terminal of the issuing bank (or of his own bank, which can then settle with the issuing bank), either by direct or remote communication, and a deposit protocol is performed. As a result, the account of the party depositing the electronic cash is credited with an equivalent amount of money [Fig 1].
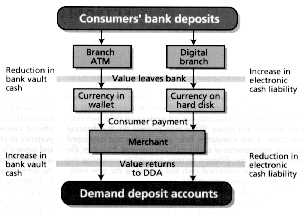
[1] Electronic cash works like traditional cash for the consumer but not for the bank. In an ATM transaction [left], the cash given to the consumer constitutes a reduction in vault cash. In a withdrawal of electronic cash [right], the value is moved within the bank and becomes a liability that is reversed when the electronic cash is presented, either on-line or off-line, for deposit.
Of utmost importance for the security of any electronic cash system is that an attacker cannot inject extra money into the system. In effect, receiving devices must be able to distinguish authentic paying devices from attackers that try to pass for paying devices. To prove their authenticity, paying devices need to be equipped by the bank with secret keys. Correspondingly, receiving devices must be able to recognize whether they are communicating with a device holding a secret key installed by the bank.
A secure authentication protocol should resist replay. In this kind of attack, a wire-tapped transcript of an execution of an authentication protocol is reused by an attacker in order to pass for a paying device The paying device should therefore perform a computation (presented by the other device in the form of a challenge) that is feasible only when knowing the secret key, rather than transmitting the secret key itself. The outcome of the computation is called the response to the challenge, and should be verifiable by the receiving device; this enables it to conclude that the outcome must have been generated by a paying device that holds the secret key.
One way for a receiving device to verify the response of a paying device is to have prior knowledge of the latter's secret key. The receiving device then simply computes the response to its own challenge as well, and verifies it for equality with the response provided; this process is known as symmetric authentication. Receiving devices need to know (or be able to generate) the secret keys of all the paying devices they have to conduct transactions with, and for this reason they must be tamper-resistant as well. Hence they must be issued by or on behalf of the bank which takes care of installing the keys of all paying and receiving devices.
Since it is dangerous to have all paying devices use the same secret key, yet cumbersome for receiving devices to store and maintain unique keys the recommended approach is to use so-called "diversified" keys. In this method, each receiving device stores a master key, generated at random and installed by the bank. The secret key of a paying device is computed as a function of the master key and an ID number unique to the paying device. This function should be such that the master key cannot be computed from a device secret key. In case a paying device has its key extracted by an attacker, and so can be simulated, the compromised device can be traced and blacklisted as soon as the fraud is detected.
A weak point of symmetric authentication is the presence of the master key in all receiving devices, so that a successful attack on any one of them enables an attacker to simulate any paying device. This vulnerability vanishes when asymmetric instead of symmetric authentication is used. As before, to prove its authenticity to a receiving device, the paying device computes a response, known as a digital signature, which is based on its secret key and a challenge; but this time to verify the response, the receiving device applies a public key of the paying device, corresponding to its secret key. Knowledge of the public key does not enable the computation of the secret key, so that receiving devices need not contain secrets that are correlated to secret keys of paying devices.
Another advantage over symmetric authentication is that digital signatures cannot be forged. The receiving device can subsequently demonstrate to the bank (or to other devices) that the proof took place by showing the digital signature of the paying device. There is no need for receiving devices to be tamper-resistant.
Two fundamental ways exist for representing electronic cash in computing devices, whether paying or receiving devices. First is to indicate the amount of electronic cash by means of the value of a counter, maintained in a chip register. For example, 100 electronic dollars spendable in 1-cent increments would be represented by a counter value of 10 000. This representation is referred to as register-based cash Since money can be forged when counters can be updated without bank authorization or bypassed, security relies critically on the tamper-resistance of the devices.
When an authentication method is combined with a register-based cash representation in paying devices, the paying device as well as the amount that is transferred must be authenticated. To this end the receiving device can encode the amount to be transferred into its challenge. The paying device must decrement the register value to reflect the amount that is transferred, and it must have been programmed by the bank to do so only when its current value represents an amount exceeding the payable amount.
The other way to represent electronic cash value is in purely informational form public-key cryptographic tokens with an associated denomination and currency. Such tokens are called electronic coins. Electronic coins must be unforgeable and verifiable solely by using a public key of the bank; their value and currency are independent of tamper-resistance, so that they form a bearer instrument in the same manner as traditional cash does. The security of electronic coins relies on the secrecy of the signature secret key of the bank.
Electronic coins can be implemented with either of two methods, depending on whether payments are verified on- or off-line. In its simplest form, an electronic coin is a pair, <message, digital signature> referred to as a coin of the "two-part form." The coin digital signature is computed by the bank by applying its signature secret key to the coin message. On the assumption that suitable coins are available to pay a specified amount, the paying device encrypts the coins using a session key derived from its secret key, erases the coins from memory, and sends the encrypted coins to the receiving device. The receiving device decrypts to recover the coins, verifies them using the public key of the bank, and then stores them. The encryption prevents wiretappers from copying the coins while they are in transit. With this method, the receiving device must be tamper-resistant as well, because otherwise the received coins could be spent many times over without there being a way to determine the origin of the fraud.
The alternative is for the paying device to encrypt the coins for the bank, using an encryption public key of the bank, instead of for the receiving device. The receiving device must then pass the encrypted coins on to the bank, for decryption and verification [Fig. 2, top]. The advantage of this approach is that the receiving device does not actually get to see the coins, and so cannot reuse them, but the downside is that off-line payment capability is lost.
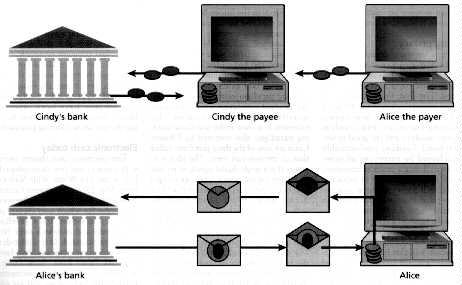
[2] In a traceable on-line electronic cash system [top], Alice withdraws digital coins from her account at the bank and stores them on her PC. Each coin is of the two-part form, and is associated with a particular denomination and currency (either in the message content or through the bank's choice of signature key). When Alice buys something from Cindy, she sends coins of appropriate denominations over the network to Cindy's shop, encrypted for the issuing bank. Cindy's software automatically sends the coins on to the bank and waits for acceptance. The bank checks the coins against its spent- coin database, and if no match occurs, stores the coins in the database and informs Cindy's bank that it can accept the payment.
Cindy can be reimbursed instantaneously, by being issued new electronic coins; since this process can be transparent, from Cindy's viewpoint she can reuse the coins of Alice to make her own purchases. (Note that Alice's bank knows that Alice has paid Cindy since it knows by whom the deposited coins have been withdrawn.)
In an untraceable on-line electronic cash system [bottom], the bank can be prevented from recognizing to whom the deposited coins have been issued. Instead of the bank creating coins of the two-part form by itself, Alice's computer this time creates the message of each coin by itself, in a random fashion. It then has the bank sign a blinded form of the message, to which end it sends to the bank an arithmetically disguised form of the message. Upon return of the signature on the blinded message, Alice's computer can extract the bank's signature on the original message, by removing the arithmetical disguise from the signature supplied. Alice can then spend the obtained coin as before.
For off-line payment, an electronic coin is best defined as a triple, <secret key, public key, certificate>, or a coin of the "three-part form." The coin secret key belongs to the paying device, and may not be known to anyone else besides the device (and possibly the bank); the coin public key corresponds to the coin secret key, and the coin certificate is a digital signature of the bank on the coin public key. To spend a coin of the three-part form, the paying device computes a digital signature on a challenge message of the receiving device, using the coin secret key, and sends this to the receiving device together with the coin certificate and the coin public key The receiving device cannot reuse the received cash, as it has not been provided with the coin secret key, so cannot by itself compute a digital signature for another challenge. Instead, the receiving device must deposit the coin.
Experience has shown that organized crime can command expertise comparable to that of national laboratories, and even individual computer criminals today have access to sophisticated tools. When secrets from paying or receiving devices can be extracted and abused, counterfeits are indistinguishable from electronic cash issued by the bank. When estimating the expected fraudulent profit that can be made, one also needs to take into consideration the economics of large-scale cracking; to crack a single smartcard, equipment and expertise running into hundreds of thousands of dollars may be needed, but this is largely a one-time investment. The damage that can be done ultimately depends on the measures incorporated in the system for preventing or discouraging unauthorized injection of electronic cash. At the very least, the bank should be able to detect and trace the injection of substantial amounts of forged electronic cash into the system. Once such a forgery has been detected, the bank should then be able to trace it to its source. (The ability to trace forgeries need not necessarily conflict with the inability to trace honest payments, as will be seen below.)
In order to hold a traced party responsible for all or part of the financial damage, it must be possible to isolate that party's liability; for example, so as to have firm ground for holding a traced party liable for the double-spending of coins, it must be ensured that the double-spending is unlikely to have been the work of a thief, unless the traced party ignored all manner of obligatory safeguards. Finally, it should be possible to quickly and efficiently distribute blacklists that enable payees to reject forged money (containment). A secure electronic cash system should provide for all of these .
To account holders, security aspects other than protection against forgery are of importance. The electronic cash held by the device of an account holder should not disappear in any other way than by being spent at the discretion of its legitimate holder. It should also not be possible for attackers to redirect a payment made by a device to any party other than the one intended by the legitimate holder of the device.
Account holders also need to be able to substantiate their position in case of erroneous or false accusations of fraudulent behavior. When parties with different interests authenticate their communications using symmetric authentication, the transcript of a communication cannot later on be used by one party to demonstrate that the communication with the other took place since it could have computed the transcript by itself. True non-repudiation requires the use of secure digital signatures, since these can be computed only by the party associated with the public key needed for verification. When crucial parts of the withdrawal, payment, and deposit requests are digitally signed, all parties can substantiate their position.
Privacy is by many deemed likely to decide the ultimate success of electronic cash with consumers. Two aspects of privacy in electronic payment systems can be discerned. The first confidentiality of transaction content, refers to the ability of account holders to prevent wire-tappers from learning transaction details such as the amount involved and the good or service purchased. Payment confidentiality can be achieved by encrypting all sensitive data sent during a protocol execution .
A more fundamental form of privacy is untraceability. If proper technical measures are not in place, electronic cash payments automatically leave detailed tracing information in the hands of a central party, typically the bank. Straightforward approaches to privacy (anonymous accounts, aggregated transaction logs that hide unique transaction identifiers, and anonymously issued paying devices) downgrade security for the bank by hindering the ability to trace counterfeiters, and at best offer a weak form of untraceability ("pseudo-anonymity"). Namely, payments by the same device are inherently linkable, and user-identification in any one transaction (as when reloading from account) makes all payments of that user traceable.
Fortunately strong cryptographic techniques exist that enable the bank to detect any unauthorized injection of electronic cash and moreover to trace it to the party that is responsible for the fraud while at the same time offering strong privacy of payments to honest account holders.
The basic cryptographic paradigm is called blinding. Invented by author David Chaum, blinding enables a receiver to cooperate with a signer in an execution of a protocol, and to obtain from the signer a digital signature on a message, in such a manner that both message and signature remain completely hidden from the signer. By representing coins in the two-part form, this technique enables an account holder to withdraw coins that cannot possibly be linked to the holder at the time of payment; this holds even if the bank were to have infinite computing power [Fig. 2, bottom].
On the other hand, the bank can always recognize its own coins, by verifying its own coin digital signatures, and can prevent double-spending by keeping track of a list of all deposited coins and checking for double-spending at the moment of payment; in case of a double-spending attempt, the bank can then simply send a message to the receiving device, telling it not to accept the payment. Note that paying devices need not be tamper-resistant, so that this method can be used to make on-line payments over the Internet using merely a personal computer and a software package.
A defect in the above blinding paradigm is that the bank can never trace double-spending attempts, since all payments are unconditionally untraceable. Consequently, while suitable for on-line payments the basic blinding paradigm is inappropriate for off-line payments.
An important extension of the basic blinding paradigm exists that enables off-line payment verification while maintaining security against double-spending. This extension is known as the one-show blinding paradigm, also invented by Chaum. Coins are now of the three-part form, rather than of the two-part form. The idea is to ensure that a single digital signature, provided by the paying device when spending a coin once, reveals no information that helps tracing, while any two digital signatures, with respect to the spending of the same coin, do reveal trace information. The bank must encode this trace information into the coin secret keys at withdrawal time. In this way, secure off-line payments can be made the tamper-resistance of paying devices is the first line of defense against double-spending while the traceability of double-spenders is the second line of defense.
The one-show blinding paradigm requires the design of a withdrawal and a payment protocol that act securely in concert. The most practical cryptographic techniques known for this purpose have been developed by author Stefan Brands.
When (one-show) blinding is performed by tamper-resistant devices issued by or on behalf of the bank users have no guarantee that the blinding is performed properly, or that no additional or subliminal information is leaked by their devices during payment To overcome this final problem, Chaum has proposed the so-called observer paradigm, whereby the functionality of the paying device is separated into two parts, each provided by a separate device. One device (referred to as the observer) is tamper-resistant and ensures prior restraint of double-spending, while the other is a user-controlled computer that controls all the blinding operations. The observer is interfaced to the user-controlled device in such a manner that all information flowing from the observer to the outside world, and vice versa, necessarily passes through the user-controlled computer; natural hardware embodiments are a smartcard in combination with a PC, for use on the Internet, or a smartcard in combination with a hand-held device for on-the-street payment. The software for the user-controlled device, and the device itself, may be purchased from any source (and could even be manufactured or modified by the user himself), so that at least in principle each user can verify for himself that the device is properly performing its tasks.
This hardware configuration enables the user-controlled device to stop any added identity-related information from being revealed by the tamper-resistant device when making a payment. Also, given proper cryptographic design of the withdrawal and payment protocols, the user-controlled computer should prevent any subliminal channels between the tamper-resistant device and the outside world. Practical cryptographic techniques for this purpose have been invented by Brands, based on his techniques for realizing the one-show blinding paradigm .
True electronic cash (bearer instrument with privacy) was first demonstrated publicly at the first World Wide Web conference (May 25, 1994) between Geneva and Amsterdam over the Web. Subsequently, a trial began for which over 70 000 people signed up to receive 100 CyberBucks (a trademark) and in which over 70 merchants participated. U.S. dollar-denominated electronic cash was then launched by Mark Twain Bank, Saint Louis, Mo. Since then, banks on three continents have licensed the technology and are offering their own national currency over the Internet. The technology enables on-line payments and is based on the basic blinding paradigm.
The first electronic wallet with observer has been built for the European Commission-sponsored project Conditional Access for Europe (CAFE), which is running a trial in the Commission headquarters in Brussels. The project involved 13 partners from several European countries, including leading scientific research centers and industrial partners. This system enables offline payments based on the one-show blinding paradigm.
_____________________
About the authors
David Chaum is the founder and chief technology officer of DigiCash Inc., Amsterdam, and is a member of its board. He earned his Ph.D. at the university of California at Berkeley and was on the faculty at New York University and the University of California. Until 1992, he headed the cryptography group at the center for Mathematics and Computer Science (CWI) in Amsterdam. Holder of over a dozen basic patents in cryptography, he founded the International Association for Cryptologic Research, and is on the editorial board of its journal
Stefan Brands did his Ph.D. research at CWI, and after working for his own consultancy company, joined DigiCash in 1997 with the title of Distinguished Scientist He holds patents on cryptographic techniques for all kinds of privacy-protecting electronic tokens. His techniques for untraceable off-line electronic cash form the basis of the CAFE system, and are being implemented by DigiCash.
The basis for parts of this article is Stefan Brands's "Electronic Cash,"a technically oriented overview that will appear in Algorithms and Theory of Computation Handbook. Edited by M. Atallah, the book is to be published in December 1997 by CRC Press, Boca Raton, Fla.
The basic blinding paradigm is described in D. Chaum, "Blind Signatures for Untraceable Payments," in Advances in Cryptology -- Proceedings of Crypto '82, edited by R.L. Rivest, A.T. Sherman, and D. Chaum (Plenum Press, New York, pp. 199-203).
Several relevant papers appear in the series Lecture Notes in Computer Science, put out by Springer-Verlag, New York. First, D. Chaum, A. Fiat, and M. Naor describe the one-show blinding paradigm in their "Untraceable Electronic Cash," Advances in Cryptology -- Crypto '88, edited by 5. Goldwasser (Vol. 403, pp. 319-327). Then D. Chaum and T.P. Pedersen discuss the observer paradigm in "Wallet Databases with Observers," in Advances in Cryptology -- Crypto '92, edited by E.F. Brickell (Vol. 740, pp. 1-14).
Also, practical cryptographic techniques for implementing the one-show blinding paradigm and the observer paradigm are dealt with by S. Brands in two papers: "Untraceable Off-Line Cash in Wallets with Observers," in Advances in Cryptology -- Crypto '93, edited by D.R. Stinson (Vol. 773, pp. 302-318), and "Off-Line Electronic Cash Based on Secret-Key Certificates," in Advances in Cryptology -- Eurocrypt '95, edited by L.C. Guillou and J. Quisquater (Vol. 921, pp. 231-247).
A nontechnical overview of the various paradigms appears in David Chaum's "Achieving Electronic Privacy" (Scientific American, August 1992, pp. 96-101).
Peter S. Gemmell
Sandia National Laboratories
The widespread success and acceptability of electronic cash systems ultimately will involve striking a balance between anonymity and traceability
To be widely acceptable and therefore successful, electronic cash systems will ultimately have to strike a balance between anonymity and traceability. Traceable e-cash would make it harder to commit many crimes but would also threaten users' privacy. Completely untraceable digital cash would pose new difficulties for law enforcement agencies.
Although physical cash has certain properties of an anonymous medium, its anonymous use is significantly constrained by the following considerations:
These properties can hamper certain types of criminal activity including mugging, kidnapping, and other forms of extortion. One of the major challenges for a kidnapper, for example, is to get the payer to provide ransom in an anonymous form. With physical cash, the problem can be difficult if the payer and the police cooperate, it can be hard to transfer a briefcase full of bills -- despite even the coercive leverage of the kidnapper. Moreover, once the bills have been transferred, spending them without being identified is often troublesome because the serial numbers may well have been recorded. For muggers, too, it is not easy to remain anonymous after getting victims to hand over their loot. What's more, the mugger is limited to the anonymous money in the victim's pockets and perhaps to a few hundred dollars more obtained from a risky trip to an automatic teller machine and its camera.
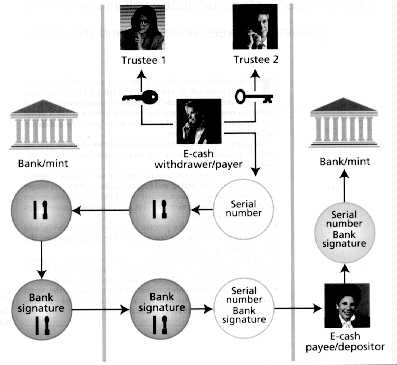
To withdraw anonymous e-cash from a bank, a payer creates the shell of a coin at her computer and gives it a serial number. She then obscures the coin from her bank mathematically, although mathematical "keyholes" remain to allow trustees to reveal the coin (if necessary), and transmits it her bank The bank signs it and returns it to the payer, who then uncovers the now-validated coin, which shows the original serial number and the bank's signature. The payer then transfers the signed coin to the payee, who can then redeem it at her bank.
By contrast, with completely anonymous e-cash, the criminal's problem would be reduced to obtaining anonymous use of any one bank account. This might be achieved by setting it up under a false identity before an attempt at extortion began or by using a third party's account. Either way, once the account had been set up, the payer-victim would put the money in it, either directly or through the criminal, who would withdraw the money in a completely anonymous form.
Money laundering, too, is hampered by physical cash and would be made easier by a completely anonymous electronic counterpart. Currently, if people suspect that the government is tracing physical cash, they may be forced to transport it to a foreign financial institution that will not continue the trace and there exchange it for different bills. This may be quite an inconvenience. With anonymous e-cash, money-laundering would be as simple as depositing one set of electronic "coins" in an account under an assumed name and withdrawing another set from the same account.
Moreover, it is now difficult for criminals to transport large amounts of money from one country to another; its sheer bulk makes it awkward to get past customs inspectors. With anonymous e-cash, however, it would be easy for a payer in one country to transfer funds to an overseas payee who would never have to explain where they came from.
Furthermore, consider the case of counterfeiting. With physical cash, even someone ambitious enough to acquire all the information, materials, and equipment needed to make apparently perfect counterfeit bills still has a problem they would have serial numbers duplicating those of legitimate bills or made-up serial numbers that did not match those on any legitimate bill. In the former case, banks would eventually notice the existence of two or more bills with the same number and alert the proper authorities -- in the United States, the Secret Service. In the latter, banks could in theory find out about the counterfeiting by comparing the numbers of bills they received with a database of legitimate numbers.
In completely anonymous e-cash systems, though, if a digital minting key used to create electronic coins were compromised, the result would be counterfeit cash indistinguishable from the legally "minted" electronic variety. So long as the system managers were unaware that the digital minting key had been compromised, the counterfeiting could go on undetected. Of course, once system managers became aware of the crime, they could shut down the system temporarily, cash in the old money, and start up again with a new minting key. But there would be only one sure-fire way for them to find out that they had a problem namely, observing that too much money had been deposited into accounts given the amount minted legitimately, together with the presumed amount of money currently in consumers' pockets and wallets.
Governments and financial institutions have been unwilling to support completely anonymous e-cash systems because of these threats. Yet until now, the only alternatives have been systems with little or no protection for the privacy of users. The challenge has been to develop a system that would provide such protection while also permitting law enforcement authorities to trace suspect transactions.
Sandia National Laboratories, Albuquerque, N.M., has attempted to develop computer protocols that strike a balance between these needs by giving the government and financial institutions the ability to control crime while maintaining privacy in other respects. A number of trustees, or key-escrow agents, would share the power to trace electronic transactions. Trustee-based tracing would be undertaken through cryptology. In this system, a tracing key or keys with a number of bits specific to a particular user and a particular withdrawal would be employed, and the operation would resemble the opening of a combination lock to identify anyone who received money, it would be necessary to know the correct bits in the correct sequence.
Once a trace had been authorized, the tracing keys of a previously determined subset of trustees (for example, three out of five) would have to be combined for a search to be effective. Thus, if too few trustees revealed their shares of the tracing key, users' spending would be completely unlinkable to their withdrawals.
Such unlinkability protects users from the possibility that one or two trustees might be corrupt and is provable in the same sense that unlinkability is provable for completely anonymous protocols. Trustees could be individuals or organizations appointed by businesses operating e-cash systems or by a consensus of all parties involved. At the national level, trustees could be appointed to enforce national e-cash security.
Trustee-based tracing might resemble the current U.S. system for obtaining search warrants if a law enforcement agency believed that it had a legitimate reason to trace an individual's spending patterns, it would seek permission from the courts. Should a judge deem the request legitimate, the trustees could be authorized to conduct a search and then make the information from it available to law enforcement authorities. Such a system would guarantee users that their spending patterns could not be detected by anyone or for any reason. At the same time, it would also give governments and other legitimate entities the ability to trace a users spending with certainty but would otherwise be completely anonymous.
In a different trustee-based e-cash system, the users' "wallet" software would require them to supply the authorities from time to time with transaction records stored in their electronic wallets and encrypted with their tracing keys. These records could be decrypted only if the trustees used their shares of the tracing keys.
Another possible way of solving the anonymity problem might be to allow individuals to withdraw a modest amount of completely untraceable electronic cash a day -- say US $100 -- remotely, that is, from their homes; there might be higher limits for withdrawals made in person at the bank. Any remote withdrawal above that sum would be traceable through the trustee-based system.
A number of variations on the trustee-tracing theme are possible. In some systems, users change their money with a number of electronic cash-issuing servers. In another, pseudonyms would be acquired from servers. Both ideas involve the creation of a trail that would have to be followed with the servers' cooperation for a trace to be conducted.
Anonymous electronic change is another important area. In a totally traceable e-cash world, anonymous change would not be an issue. But in a trustee-tracing or completely anonymous environment it is a necessity. For older e-cash systems, including those aiming at total anonymity, it would be hard to make anonymous electronic change. If a consumer purchased a $5 item with $10 in electronic coins, for example, the $5 change could take the form of traceable electronic coins.
A simple approach to change might be for users to withdraw all their anonymous money in electronic "pennies" (that is, the smallest possible denomination), so that they would always have correct electronic change. Unfortunately each electronic coin would require at least several thousand bits, so this approach is hardly feasible in most situations.
In early attempts to create anonymous electronic change, it might have been impossible for someone illegally tracing user spending to link a purchase directly with a user, but the tracer could easily tell when a user had made two different purchases. In this sense, a users purchases would be linked to one another, and if the user were somehow to be identified in just one purchase, all the others would be linked indirectly to that user.
Anonymous electronic change remains potentially troublesome in off-line scenarios, in which only the payer and the payee need be active at the time of payment. However, Sandia National Labs has developed on-line anonymous change concepts that would let users and a bank anonymously exchange a set of electronic coins for another set with equal value but different denominations. The bank would not learn the user's identity, and the system would be protected from multiple spending of electronic coins. Without multiple spending or the help of trustees, it would be impossible to link the old coins to one another or to the user. Such anonymous change could be used in either trustee-tracing or completely anonymous environments.
____________________
About the author
Peter s. Gemmell has been a senior member of the technical staff at Sandia National Laboratories in Albuquerque, N.M., since May 1995. His research interests include the design and cryptanalysis of cryptographic algorithms and protocols for such purposes as distributed cryptography and e-cash. He has also undertaken extensive work on formal techniques for establishing the reliability of software. This article reflects inventions made at Sandia by Ernie Brickell, David Kravitz. and the author.
For more on Sandia's electronic cash systems and Peter Gemmell's work, see www.cs.sandia.gov/psgemme/main.html
Techniques for preventing the fraudulent replication of electronic cash are discussed by W. Mao in "Lightweight microcash for the Internet," which appeared in in Esorics 96: Fourth European Symposium on Research in Computer Security, Rome, Sept. 25-27, 1996, edited by Elisa Bertina (Vol. 114, Lecture Notes in Computer Science, Sprinqer-Verlag, New York).
Stanley E. Morris
Financial Crimes Enforcement Network
Department of the Treasury
Cash can leave a paper trail, but electronic payments could be an effective means of laundering money from illegal activities
New technologies have emerged that have the potential to change many fundamental principles associated with a cash-oriented society -- indeed, the whole way we conduct all kinds of financial transactions and operate all payment systems.
As things stand, law enforcement agencies around the world recognize that "following the money" leads to the top of criminal organizations. Criminals have to move funds through the financial system to hide and use the proceeds of their crimes. Currency is anonymous, but it is difficult to hide and transport in large amounts. New electronic payments systems may well alter this. The speed that makes these systems efficient and the anonymity that makes them secure are desirable characteristics to both the public and law enforcement agencies. Yet the same characteristics make these systems equally attractive to those who seek to use them for illicit purposes.
Legitimate uses of these technologies are easy to illustrate. A shoe store in the United States could accept smartcards for purchases. As the store's revenues increased, it could transfer the value of its revenues to another smartcard or download the value into a computer. This sum could in turn be transferred through the Internet to financial institutions, businesses, or people around the world and used to pay invoices to order materials, and to pay suppliers -- stimulating commerce, making trade less expensive, and providing benefits to consumers.
But now suppose that the retailer is a group of narcotics traffickers. Consider the invoices they might pay, the supplies they might order, and the transactions they might undertake successfully if they could download an unlimited amount of value from a smartcard to a computer and then transmit those funds to other smartcards or to computers in locations around the world. Again, all this would happen anonymously, without an audit trail, and without any need to use traditional financial institutions.
Historically law enforcement and regulatory officials have relied upon the intermediation of banks and other types of financial institutions to provide "choke points" through which funds must generally pass. In fact, many regulations, such as the Bank Secrecy Act enacted in 1970 and repeatedly amended, have been designed specifically to require financial institutions to file reports and keep certain records, ensuring the existence of a paper trail for law enforcement investigations. In an open environment like the Internet, exchanges of financial value could occur without the participation of a financial intermediary, thus, eliminating the choke point.
New systems will also diminish the effectiveness of traditional investigative techniques, which have typically relied on the analysis of financial documents. The ability -- or inability -- of financial institutions to know their customers in a potentially anonymous, paperless payment system is also a concern. Another challenge facing law enforcement is the fact that these payment systems are being designed to operate internationally in multiple currencies, so it will become harder to determine the correct jurisdiction.
Because of these potential vulnerabilities, the Financial Crimes Enforcement Network (FinCEN), a branch of the U.S. Department of the Treasury, has been meeting with developers of advanced electronic payment systems, our law enforcement and regulatory partners in the United States and abroad, and representatives of the financial services industry to examine how criminals might use these new systems to move and launder the proceeds of their illegal activities.
Too often, the government has attempted to thwart potential threats by imposing a regulatory burden that does not reflect their true nature or the business practices of the industries affected. We cannot make the same mistakes with cyberpayment systems. The technology is developing too rapidly, and the potential efficiencies and other benefits are too important.
Yet if law enforcement concerns do not receive thoughtful and balanced consideration now the prospect for abuse by organized crime, money launderers, and other financial criminals could be great. Moreover, we need to look beyond our borders to ensure both the integrity of these systems and fair competition in the global market. The secretary of the treasury has accordingly designated Eugene Ludwig, comptroller of the currency, as coordinator of Treasury's efforts in this area. Working with him are the U.S. Customs Service, Internal Revenue Service, Secret Service Bureau of Alcohol Tobacco and Firearms, the Office of Foreign Assets Control, and FinCEN.
Clearly, electronic payment systems are still in their infancy. How they develop will depend on their effectiveness and the markets response. Therefore, it is necessary to consider prescriptive solutions to theoretical problems. Still, it would be a disservice to the public and to the developers of cyberpayment systems for law enforcement and regulators to put off framing the issues that must be addressed as markets and technologies mature. Our goal is to inoculate these new systems against crime and misuse to the greatest extent possible, and to permit their healthy growth into the next century.
_____________________
About the author
Stanley E Morris has been director of the Financial Crimes Enforcement Network (FinCEN) since 1994. FinCEN is the U.S. Treasury Department's organization that has primary responsibility for setting, overseeing, and implementing policies against money laundering and for administering the Bank Secrecy Act. He has served in the Federal government for more than 28 years in a variety of positions, including chief of staff for the under secretary of the Treasury for enforcement, deputy director for supply reduction in the White House Office of National Drug Control Policy, director of the U.S. Marshals Service of the U.S. Department of Justice, and associate deputy attorney general of the Department of Justice.
Robert W. Baldwin & C. Victor Chang
RSA Data Security Inc.
A variety of cryptographic techniques are being used to minimize threats to electronic transactions
One of the first devices that improved the daily routine of commerce was the cash register which enforced business rules about when cash drawers could be opened and allowed the shop owner to know how much money should be lying in the drawer at the days end. This relatively simple device also improved the accuracy and the speed of the check-out procedure while reducing the risk of theft by employees.
Today, merchants, banks, and consumers face much larger risks. The explosion of the Internet has permitted even small merchants to sell goods and services to a worldwide market, yet it has also exposed them to the depredations of a large pool of attackers whose motives range from greed to boredom. If the attacks come from other countries it may not be practical to seek legal recourse. Moreover, as the value of on-line information increases, so does the temptation to engage in insider theft: system administrators, for example, may discover that they can transfer US $10 million to offshore banks and can even charge their employers for airplane tickets to other countries.
Fear of these risks has created a demand for security features built directly into electronic commerce systems. The good news is that existing security mechanisms can be combined to minimize a wide range of threats to electronic commerce.
Security isn't the only problem. European banks will soon have electronic stored-value cards that are as good as cash. A vending machine in the middle of a golf course will be able to accept payment from these cards, without any need for a network connection. Forgetting the password for a stored-value card could be as troublesome as losing a wallet.
The mechanisms used to solve security problems can be divided into four areas--privacy, authentication, integrity, and scalability -- though a single mechanism can often mitigate more than one kind of problem. Privacy includes the desire to keep documents and communications secret, as well as to hide the very existence of certain kinds of information and to protect the identities of the parties communicating. Authentication and integrity refer to the need to confirm the identity of users, the authenticity of messages, and the integrity of messages or connections. Scalability mechanisms, likely distribution centers and digital certificates, are crucial to the success of electronic commerce systems, because they help in creating systems that involve millions of users, transactions and documents.
The cornerstone of all privacy mechanisms is encryption. An encryption algorithm transforms a plaintext message into an unreadable ciphertext using a key [Fig. 1]. The correct key can reverse the process, permitting anyone who knows it to get the plaintext message. A strong encryption algorithm will resist even serious attempts to read the message by means other than application of the correct key. The benefit of encryption is that the ciphertext does not have to be kept secret; it could be broadcast over a satellite or published in a newspaper since only someone with the correct key can read the message. If the encryption key and decryption key are identical, the system is termed symmetrical.
[1] In a conventional encryption system, Alice encrypts a document with a data encryption system (DES) key, and Bob decrypts it with the same key. Sharing secret keys in such systems requires a prior relationship between the parties.
Encryption has transformed the problem of keeping lots of messages secret into the problem of keeping a single key secret. A key is relatively small (40 to 2048 bits long) and can usually be used for long periods of time so it is not extremely hard for systems of moderate size to distribute keys securely.
In the early 1970s, a new class of encryption algorithms -- asymmetric, or public key, cryptography -- was invented [Fig. 2]. Before then, if two people wanted to communicate securely, they had to agree on a secret key in advance. This was cumbersome when a large group of people needed to communicate, since the number of secret keys grows with the square of the community's size. The important feature of public-key algorithms is that the key used to encrypt a message differs from the one used to decrypt; in fact, if an attacker knows one of the keys, it is still impossible to deduce the other For example, Alice could publish her encryption key so when Bob wanted to send her a message, he would encrypt it with her public encryption key. Only Alice would be able to decrypt this message since her decryption key is secret. This approach works for large communities because each person has to publish only a single key; thereafter they can all receive private messages from the others.
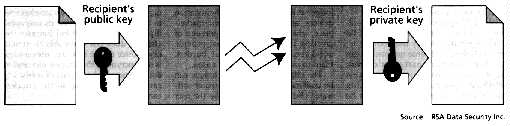
[2] In the public-key cryptography anything encrypted with a public key can be decrypted only with the corresponding private key, and vice versa.
Public-key algorithms are slower than symmetric algorithms since the former are usually based on arithmetic, with numbers at least 300 decimal digits long. This limitation was overcome by a security mechanisms called a digital envelope [Fig. 3], an encrypted binary message that has a standard format for specifying recipients, cryptographic keys, and data encoding. The bulk of the envelope is occupied by the message body, encrypted with fast symmetric-encryption algorithms using a message key newly generated to increase the security of the overall system. This message key is then encrypted with the recipient's public encryption key, and the two parts are sent ott as a single digital envelope. The recipient uses a private decryption key to extract the message key, which in turn decrypts the body of the message. Digital envelopes work well for store-and-forward messaging environments or even file encryption.
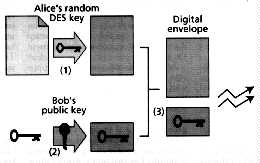
[3] Alice encrypts the document with a random DES key [1] and then looks up Bob's public key and uses it to encrypt the DES key [2]. Together, the encrypted document and the key form the digital envelope [3]. Only Bob's private key can open an envelope addressed to him.
In commercial applications, the thing being protected is often an Internet interactive communication channel between a consumer and a merchant. Such interactive sessions can be protected by digital envelopes or by a session-key mechanism like the Diffie-Hellman (DH) Key Agreement protocol. The DH protocol is an exchange of messages that allows two parties to agree on a shared secret key, which can then be used to protect the privacy and integrity of all subsequent traffic. A typical shared secret key produced by the DH protocol has a length of 128 bytes, and hash functions are used to cut that down to, say, an 8-byte Data Encryption Standard (DES) cipher key.
This DH protocol might be used to set up encryption keys for a Web shopping session. The buyer picks a secret random value, BuyerSecret, and sends the seller a DH function of BuyerSecret. The seller, too, picks a random value, SellerSecret and sends a DH function of it to the buyer. Now that the buyer and seller each know their own secret and a DH function of the other party's secret, they can compute another DH function of these values. Both parties will end up computing the same value, although they are starting with different inputs.
The security of DH is based on the fact that it is easy to raise numbers to a power (for instance, 2 raised to the third power is 8), but hard to invert that operation (for example, computing the log to the base 2 of 8 is 3). Computing logarithms is not excessively hard for ordinary integers, but becomes very hard indeed when the numbers are large and clock (modulo) arithmetic is used with primes. For example, 2 raised to the 3rd modulo 5 is 3, not 8.
A shared secret can be set up with a total stranger; even if an attacker records the setup messages, the secret cannot be deduced. After a DH setup, the user has no idea whom he or she is talking to, but does know that no one else is listening. This creates an important security feature perfect forward secrecy, which means that even if the attacker were to find out everyone's private keys (perhaps as a result of a court order), it would be impossible to decrypt any of the messages transmitted under the DH key The latter depends on fresh random values that each person picks, and if they are forgotten, a recording of the messages cannot be decrypted. The encryption key for a DH-protected session does not depend on any long-term secret key the attacker can discover.
If a DH system requires authentication digital certificates can be exchanged after the key has been set up, and a challenge-response mechanism can confirm that each party has current access to the matching private key. Without resorting to traffic-tracing mechanisms, an attacker would not be able to decrypt the authentication exchange and would therefore not be able to tell who was talking to whom This feature is important when a business does not want its competitors to find out with whom it is doing business.
The most basic form of authentication is validating the identity of system users. Traditionally, passwords have been used to do so, but they become a weak link when an attacker can monitor connections between users and the target system. Many news stories show how easy it is for attackers to grab passwords from a network.
One mechanism that offers substantially better user authentication is a credit-card-sized authentication device -- a token or smartcard -- that can store a secret key and perform a cryptographic challenge-response. To access the system, the user must have the authentication token as well as a password.
In their strongest form, authentication devices require the user to activate the token by entering their passwords on its keypad . When the user logs in over the Internet, the company's firewall sends back a random numeric challenge that must also be entered on the token's keypad. The token encrypts the challenge under its secret key and displays this result to the user. The user sends the firewall this result. Since the firewall also knows the token's secret key, it can check the response to ensure that the user has the correct token. In the end, the firewall has high confidence that it is communicating with an authentic user. Additional steps can be performed to authenticate the firewall to the user and thus ensure that the user's network connection has not been incorrectly routed to an attackers site.
A substantial simplification of the full challenge-response mechanism involves basing the challenge on clocks kept synchronized between the user and the system, eliminating the need for the user to type in the challenge. Instead, the device simply displays new values every minute. When users connect to a Web page that requires extra authentication, they type in the number from the card instead of a password. The number can be recorded, but unlike a password it cannot be reused the authentication server will allow a particular number to be used only once during a given minute, and after that, it is no longer valid. Time-based authentication devices are very popular in the marketplace, which points up the importance of creating security systems that provide good security without undue burden. Hard-to-use systems are just not used.
The challenge-response technique can be undertaken entirely in computer software. The secret key shared by the user and the system can be stored on the users computer with some kind of password-based encryption, and the challenge-response actions can be performed without any user intervention. The drawback--somewhat diminished by the popularity of laptops -- is users must have their computers with them to access the system. Moreover, software secrets can be surreptitiously copied by local attackers, who could then, in the safety of their own homes spend hours trying to find the password by having a program put forward every word in the dictionary, along with such common variations as substituting the digit 1 for the letter l. Authentication tokens cannot be copied as easily as disk files, so they resist this threat.
Once users have been authenticated, the next problem is authenticating the individual messages. An electronic funds-transfer system has to know that its instructions come from the expected source and have not been modified by an attacker. The core mechanism for achieving this kind of authentication is called a one-way digest.
The functions are called "digests" because they take as input an arbitrarily long message and produce a summary -- or digest -- of it that is fixed in size. One example of a digest is a checksum by parity check. Cryptographic digests are one-way in the sense that it is easy to compute them, but computationally infeasible to find a message that has a given digest; that is, computing the function is easier than computing its inverse. Ordinary checksums do not necessarily have this property -- for example, it is easy to modify the digits of a bank account number without changing the check digit. This one-way property means that the digest will detect message-tampering with very high confidence. An attacker cannot modify a message without changing the digest.
One-way digests and public keys can be combined to create digital signatures attached to electronic mail, purchase orders and other business documents [Fig. 4]. Alice can sign a message by computing the digest and then encrypting it with her private key. Bob verifies that the message came from her by decrypting the digest using Alice's public key and comparing that value with the digest he computed for the message. If an attacker modified the message, the digests will not match. If an attacker tries to modify the message and its encrypted digest, that, too, will fail because the attacker does not know Alice's private key. Notice that in this case, the message is not encrypted; the attacker can read it. But anyone who knows Alice's public key can detect tampering, so the attacker cannot engage in it.
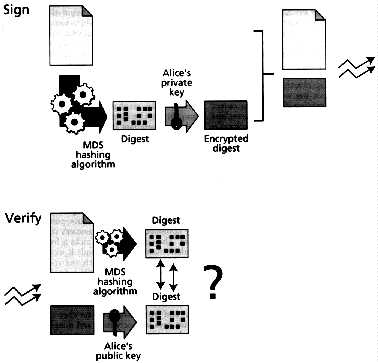
[4] To sign a document with a digital signature, Alice passes her document through a hashing algorithm so as to produce the message digest. then encrypts it with her private key, forming a digital signature. Next, she transmits the signed document to Bob. After receiving her transmission, Bob employs the same hashing algorithm to create another message digest and also decrypts the signature using Alice's public key. If the two digests match, then the signature is valid.
Privacy and authentication mechanisms can be combined to create a signed digital envelope that ensures both privacy and integrity. In this case, the message has three parts: the encrypted plaintext body, the plaintext encrypting key encrypted under the recipient's public key, and the plaintext digest encrypted with the sender's private key. The first two are used as before to allow the proper recipient to read the plaintext; the digest in the third part is used to check for tampering. The result is a signed and sealed digital envelope whose contents could be a short e-mail note or the detailed design specifications of an automobile engine.
One-way digests can also be combined with shared secrets to create a high-performance integrity-checking mechanism called a message authenticity check (MAC). Integrity checking is intended to make sure that if an attacker tries to tamper with messages, or even with a single character of a single message, the mechanism will detect the modification and reject the message. For example, the system may require an integrity check on each character transmitted over a network connection. If so, the performance overhead of a public-key operation may be unacceptable.
An alternative is to set up a shared integrity-checking key that becomes one of the inputs to the one-way digest. Like symmetric encryption keys, this integrity key must be kept secret, since attackers can tamper with a message if they know the integrity key. The integrity of a single byte can be ensured by sending the string digest, which consists of the single byte being sent appended to the integrity key and a byte counter. Recipients know the key, the byte counter, and the received byte, so they can check the digest to detect modified or missing bytes. Attackers do not know the integrity key and thus cannot compute a digest that will pass inspection. For instance, to ensure that an order to sell 5000 shares cannot be changed to an order to sell 9000 shares this mechanism could guarantee the integrity of a real-time connection between a stock broker and the trading floor of an exchange.
The basic cryptographic primitives needed for electronic commerce were created by researchers in the 1970s and '80s and have by now moved into mainstream communications engineering. Newer primitives and constructs deal with problems of scale -- for instance how to provide digital certificates for everyone who has a credit card -- and are being forced into mainstream engineering by the exponential growth of the Internet. Some of the newer problems do not have solutions, and some apparent solutions have turned out to be wrong. Still, certain mechanisms do appear to have enduring value.
Dealing with millions of users is the first scaling problem. A traditional symmetric key system requires every pair of users to have a unique key. Thousands of users would require a million or millions of keys, millions of users an unmanageable number of them. This problem can be handled by using either asymmetric public-key cryptography or key distribution centers (KDCs) that facilitate high-performance symmetric cryptography. A KDC is a system that a user trusts with their secrets. In particular, each user shares a secret key with the KDC and takes advantage of that key to generate the key employed to communicate with all other users.
For example, if Alice wants to send a message to Bob, she firsts sends the KDC a message requesting a key for talking with him. That request and the response from the KDC are protected by the secret key (actually an integrity-checking key and a message-encrypting key) that Alice shares with the KDC. The response from the KDC includes a packet of bits that Alice will pass on to Bob with the message. The packet contains a copy of the message key encrypted under the secret key Bob shares with the KDC. When Bob gets the message, he decrypts the packet of bits to find the message key. To reduce the overhead of communicating with the KDC, Alice and Bob can decide to reuse the message key for a sequence of messages or for a predetermined time. For example, a connection between a stock broker and a trading floor could be set up in the morning and the same keys used for all buying and selling messages sent during that day .
Many of the benefits of KDCs are also drawbacks. The KDC generates all message and session keys, so they are all uniformly good and uniformly protected. There is no need to worry about a laptop that generates very predictable message keys. Of course, if the KDC is physically or logically compromised, so is the whole system. The KDC can provide key escrow (allowing authorized entities to invade the privacy of the users) by recording all message keys or by producing them in a reproducible way. Some environments require key escrow.
A variation on the KDC system is to hand out access-control tickets instead of session keys. The packet of bits Alice gets from the KDC could be a message encrypted for a funds-transfer server, stating that she may transfer up to $1 million during a particular eight-hour period. Alice would include these bits whenever she needed to use the funds-transfer system, which could decrypt the packet and establish that Alice was complying with the business rules.
In small-scale systems, keys are rarely compromised and are never changed. However, in global electronic commerce systems, these are common events. Mechanisms for handling key changes for both symmetric and asymmetric cryptography are similar. The main idea is to attach names and attributes to keys. These names could be short printable strings or they could include such attributes as the range of dates for which the key is valid. Key names are then added to all messages, and recipients maintain a key chain that can be indexed by the key name to find the correct key.
To reduce the size of key chains, keys can be divided between two classes: key-encrypting keys (KEK) and data-encrypting keys (DEK). Only the KEKs are given names and thus put on key chains. To create an encrypted message, the sender creates a fresh DEK (which does not have a name) encrypts the data with it, and then encrypts the DEK under a named KEK. The final message includes the KEKs name, the encrypted DEK, and the encrypted data. This refinement dramatically reduces the total number of bytes encrypted with named keys, reducing the risk that an attacker will get enough information to break the cipher.
With asymmetric cryptography, public keys can exploit a similar scheme. To check and trust a digital signature, the recipient must have a high-integrity source for the senders public key. How is this possible? What prevents an attacker from tampering with the trusted database of public keys?
The solution involves creating a digital certificate, a signed message stating that someone's public key is a 1024-bit number and that this key is valid for a specified time. Digital certificates are created by trusted third-party organizations called certificate authorities (CAs), which have good physical security. In small systems, every recipient has a built-in tamper-resistant copy of the CAs public key, so they can all verify signatures on digital certificates. In larger ones, the recipient might need to look up the CAs public key by finding the CA's digital certificate, which is of course signed by a higher-level CA.
This process is repeated until it reaches one of the public keys trusted by the recipient. These trusted keys are called "root keys" because they form the root of the tree of certificates, each signing the certificate immediately beneath it in the tree. Root keys must be built into the recipient software. For example, a company called VeriSign Inc., which runs a CA for commercial Web servers, will issue digital certificates only to companies that give it certain notarized business documents. Web browsers have the root public key for VeriSign compiled into their software, so they can validate a commercial Web server certificate.
One major benefit of asymmetric cryptography is that the root public key does not have to be secret, just tamper proof. In fact several root public keys appear regularly in The New York Times. People can confirm that their copy of the key has not been altered by comparing it with the published version.
In the early days of public-key cryptography, some users tried to create a single root key and a single hierarchy of certificates that would identify all the people in the world. This approach failed because it assumed that digital certificates were proofs of identity. It makes more sense to regard the certificate as a contract that identifies two or more of its signers and specifies some of its parameters.
For example, the digital certificate someone might use to buy goods with a bank's credit card includes information about the card, the bank, the user, the account, the certificates expiration date, and perhaps a separate date for the expiration of the account. It might even include information on spending limits to distinguish high-dollar corporate purchasing cards from retail credit cards. This model implies that different certificate hierarchies support various classes of contracts. The proof-of-identity certificate is a special "is-a-citizen" contract.
Root keys for certificate hierarchies bring up another problem of scale. The monetary value of the private key that signs all the digital certificates used by credit card companies is enormous. Even if no fraud were ever committed with the compromised key the cost of changing the root key would be huge. New mechanisms are needed to handle key management in cases when potential losses scale up from thousands to billions of dollars.
VeriSign's root private key is already protected by a mechanism called secret sharing. The idea is to take an important secret and break it into parts that can be given to different trustees, so that the original secret can only be reconstructed if enough trustees provide their parts of the secret.
For example, one commercial root private key might be split into five parts, with at least three required to reconstruct the private key. Since the private key is needed only when a new certificate authority is created, the overhead of gathering physical trustees is acceptable. All-electronic forms of this scheme do not require people to fly to the same location. For instances, a work-flow automation product can use such a scheme to enforce a dual-signature business rule on large purchase orders the purchase order could be signed with a private key that would have to be created from any two of the keys owned by people authorized to sign large orders.
Secret splitting is based on the idea of fitting curves to points on a plane (for instance, drawing a line that passes through two points, or a parabola that passes through three). Suppose you want to split a secret into five parts and to require that anyone have at least two to reconstruct it. Any two points uniquely determine the slope of a line, but one point tells you nothing. If the secret can be represented by the slope of a line, the five shares of a secret can be created by picking any five points along any line with the correct slope. Any two of these points can be used to reconstruct the secret, but one point does not help an attacker.
To get such higher thresholds as three out of five this scheme can be extended to higher-order curves, like quadratics and cubics. Another extension that helps with a large secret involves breaking it into small pieces of perhaps 1 byte a piece, and using the secret splitting algorithm with each of them. If knowledge of one piece does not help deduce the values of the others this extension is as secure as the original mechanism. Root private keys have this property.
Electronic commerce systems arc secured by combinations of the basic mechanisms. Engineering tradeoffs achieve a good balance among improved productivity, easy of use, performance, and risk management Cryptographic security mechanisms are added to improve the latter, usually at the expense of the other desiderata.
In any case, cryptographic security mechanisms can cut costs and improve productivity by eliminating the need for face-to-face contact. Bank teller machines are a prime example. Each of them uses a secret key, stored in hardware, that is shared with its parent bank's key-distribution center. That center acts as a translator to connect the machine to other centers with which it shares a different secret key. This chain of pair-wise secrets eventually leads to the users own bank, which approves the transaction. The system uses a hierarchy of shared secret keys to build up an international money-transfer operation.
Payment systems are among the most active engineering areas for electronic commerce. If merchants can be assured of receiving payment, they can accept orders from the growing market of Internet users. Several systems are in use today, and new ones will be deployed in coming years. A San Diego, Calif., company called First Virtual (FV) has the simplest deployed system, which uses ordinary insecure e-mail as a communication mechanism and relies on legal contracts to provide all security.
Consumers and merchants set up accounts with FV. When the consumer orders goods, the merchant sends FV email with the transaction details and purchase amount. FV then sends e-mail to the customer asking for confirmation. If the answer is yes, FV tells the merchant that FV will pay for the goods after 90 days. FV then places a charge against the customers credit card The 90-day wait is the systems hook into the existing legal system for credit card fraud. If the merchant or consumer notice a problem, they have 90 days to send FV a report. Should the waiting period go by without any reports no one has the right to dispute the transaction, so FV can pay the merchant. The amazing thing about the FV mechanism is that the demand for electronic payment is so high that merchants and consumers are willing to accept its limitations.
Visa and MasterCard are preparing to deploy a more secure system for credit card transactions Their Secure Electronic Transactions (SET) protocol uses public-key cryptography to provide authentication, privacy, and integrity. Several companies are building software systems that will incorporate this protocol, which uses digital certificates for authentication and for creating signed and unsigned digital envelopes. The certificates are issued by consumer banks to the card holders and by credit card processing centers to the merchants.
All the certificates chain back to a global root public key shared by MasterCard, Visa, and other payment-card issuers -- that is built into browsers, electronic wallets, merchant servers, and other commercial software packages. The problem of looking up certificates is solved by requiring SET messages to contain all the certificates needed for their authentication unless the sender knows that the recipient already has appropriate certificates.
SET has highly specific privacy goals. It does not attempt to secure such shopping information as the list of goods being purchased, for other protocols, like the Secure Sockets Layer, can protect that. Rather SET has been designed carefully to prevent the merchant from finding out the cardholder's credit card number. Today merchants always learn the card number, and this is a major source of fraud. Cardholders who use SET put their card numbers in an envelope that can be opened only by the card-processing center, not the merchant. The merchant trusts the processing center to check the cards validity.
SET was designed to conform to U.S export control laws, so SET-compliant software can be produced in the United States and sold worldwide. (RSA Data Security has actually been granted the right to sell its SET software, S/PAY, globally.) However, the SET protocol's business model does not meet the needs of all countries. For example, in Japan most electronic payments involve direct transfers between bank accounts, not credit cards buyers tell their banks to transfer payments directly into sellers' bank accounts, avoiding the 3 percent service charge levied by most credit card associations. In Japan, consumer bank accounts are often tied to an automated system of loans linked to the quarterly and yearly bonuses that make up the majority of the income of most Japanese consumers. The current SET protocol does not deal with the banking regulations that govern these loan accounts, but work has started on a SET-like protocol that would meet Japan's needs.
Stored-value cards offer another approach. The idea is to trust a computer about the size of a credit card to store and track your money (see "In your pocket: smartcards"). Funds can be added to the electronic wallet by the consumer and removed by the merchant. The security of stored-value cards is based on keys stored in the hardware and used to convince merchants that card are legitimate and backed by enough money. The card must also recognize legitimate banks so that it cannot be tricked into adding funds that are not truly available.
The primary benefit of stored-value cards is that they eliminate the need for on-line communication with banks -- a highly desirable feature for developing countries that do not have extensive phone systems. Such countries can directly convert the basis of their economies from cash to stored-value cards, without passing through the paper check and plastic credit card stages. A similar technological leap has already happened in telecommunications countries that had only a few copper-wire telephones installed very quickly acquired many of their satellite and cellular counterparts.
Another approach that avoids on-line communication with banks has cropped up for micropayments, transactions for such low-value goods as a piece of candy or a copy of a newspaper The low profit on these small transactions does not permit high processing or communication costs. Though differing quite a bit on the details of initial setup, user authentication, and grouping of transactions, most micropayment schemes are based on the one-way properties of cryptographic digest functions. The basic idea is to use a cryptographic function to create a roll of numbered coins. You spend a coin by telling the merchant the coin number and numbers can be chosen to prevent anyone but a legitimate merchant from presenting them to the bank for payment.
In one simple micropayment protocol, the number on the first coin is chosen at random. The number on each successive coin is the digest of the number on the preceding one. With a knowledge of a single coin number, any person can compute the numbers on all subsequent coins in the roll, but no one else can know the number of the preceding coin, since the digest is a one-way function A merchant can prove to a bank that a consumer has spent 10 coins by presenting the first coin in the 10-coin sequence along with a digitally signed note from the consumer identifying the last coin in the sequence, something only the consumer could have known. The performance benefit is that only the last coin requires a digital signature operation all the others can be checked with the fast digest functions.
Of course, electronic commerce is more than just payment systems; it also deals with entering and tracking orders, the sharing of design specifications, and the creation of contracts. The problem is how to share information securely and how to give outsiders controlled access to internal corporate information systems. Two protocols address this.
The Electronic Data Interchange (EDI) standard is a collection of agreements for representing business information ranging from electronic circuit designs to purchase-order forms. The overhead of setting up an EDI system for a particular application is very large, so this approach is mostly restricted to high-volume transactions between long-term business partners, such as automobile makers and their suppliers.
From a security perspective, an EDI document is like an e-mail message that must be transferred from one company to another with very high reliability, integrity, authentication, and privacy. In the past two years several e-mail vendors have adopted an e-mail security standard called Secure Multipurpose Internet Mail Extensions (S/MIME) which addresses most of the problems involved in sending EDI documents over the Internet. S/MIME uses digital envelopes and signatures to ensure the authenticity, privacy, and integrity of e-mail, and companies are now offering EDI systems that transmit documents using S/MIME. To meet EDI's stringent need for reliable delivery, these EDI products add return receipts and other end-to-end security features.
The leading choice for low-volume business information exchanges are the World Wide Web standards the Hyper Text Transfer Protocol (HTTP) and the Hyper Text Markup Language (HTML). Together, they provide a way of creating cross-platform graphical business forms (via HTML) and of submitting these forms to business systems and viewing the results (via HTTP). Unlike EDI, these mechanisms are used interactively over a network connection that can be thought of as a stream of bytes similar to a modem connection over a phone wire. The security problems are identical to those presented by EDI, but the most common solution protects the underlying network connection, and not the HTML or HTTP messages.
The protocol called the Secure Sockets Layer (SSL) was invented to protect HTML-over-HTTP connections, though it can be used with other byte-stream protocols, such as FTP or Telnet. When a consumer connects to a merchant's server over the Internet, SSL sets up a unique cryptographic key used to protect the privacy and integrity of the remaining bytes of the network session. In the simplest case, only the merchant has a digital certificate and the public key inside that certificate is used to transmit the shared secret key chosen hy the consumer.
The merchant can send the consumer a certificate over an insecure channel, since the consumer can verify the certificate's integrity and authenticity with a global-root public key compiled into the consumer's software. The consumer then picks a fresh random master key and sends it to the merchant encrypted with the merchant's public key. Only the intended merchant will be capable of decrypting this message.
Now both parties share a secret master key, and from that point on they can derive keys for encryption and integrity checking. Henceforth, no one can see the contents of the data stream, so the consumer can fill out HTML forms that include such sensitive information as account numbers, passwords,and stock purchase transactions. The more advanced form of SSL includes digital certificates for both merchant and consumer, providing for greater authentication and for the creation of a shared master key that depends on random values chosen by both parties.
The goods sold and sent over the Internet include such things as news articles and software. With software, consumers want to protect themselves against viruses. With news articles, they want to be sure of the information authenticity. Digital signatures can address both of these concerns. If an application appears to be from Microsoft, the consumer can check its digital signature to prove its provenance and to ensure that it has not been altered by an attacker. Of course, attackers, too, can get digital certificates and create digital signatures, but they will not be able to masquerade as a well-known business.
Existing security mechanisms can be combined to create systems that greatly reduce the risks of electronic commerce. Doing so will crucially promote its large-scale adoption, especially in international business, where the cost of legal disputes involving more than one country is inordinately high. New mechanisms are needed to handle the increasing scale of electronic commerce, though digital certificates and hierarchies of certificate-issuing entities provide an adequate start.
Tax and tariff laws interact with all electronic commerce systems. Normally, a purchase is a transaction between two people -- the seller and the buyer -- but the governments at both ends are also involved. Strong privacy may tempt some people to bypass local, regional, or international laws. The simplistic approach is to outlaw strong privacy. Better ones would extend traditional business record-keeping laws and add features for unannounced tests of compliance.
Illegal commerce is not a new problem. Governments currently balance the costs of tight enforcement against the benefits of an open growing economy. The need for high cryptographic security in international electronic commerce systems increases both the costs and the benefits. Each country will have to find its own new balance.
____________________
About the authors
Robert W. Baldwin is a senior engineer at RSA Data Security Inc., Redwood City, Calif., where he is responsible for the SET engine product for secure credit-card transactions over the Internet. He has designed security products, and led teams that built them, at Oracle Systems, Tandem computers, and LAT.
C. Victor Chang is vice president of engineering at RSA Data Security. Before joining the company, he spent seven years at Apple computer Inc., where he managed the development of collaboration software technologies and served as the cross-functional program manager for the Macintosh System 7 Pro which includes digital signatures and other cryptographic features. At Intel, Xerox, and First Pacific Networks he led development of communication, network server, and real-time operating system products.
Applied Cryptography: Protocols, Algorithms and Source Code in C, 2nd edition, by Bruce Schneier (John Wiley & Sons, New York, 1995), is a compendium of security mechanisms and protocols that use cryptography to counter many threats.
"Answers to Frequently Asked Questions about Cryptography," by RSA Laboratories (www.rsa.com/rsalabs), provides short answers to common questions.
"Public Key Cryptography Standards (PKCS)," by RSA Laboratories (www.rsa.com/rsalabs), is a series of memos that document security mechanisms that software vendors have agreed upon to ensure both interoperability and high security.
Several security protocol specifications are available via the World Wide Web. The SET protocol is described in www.visa.com/cgi-bin/vee/sf/set/intro.html, the SSL specification in gold.lsn.com/ssl.htm.
Carol Hovenga Fancher
Motorola Inc.
The worldwide boom in smartcard deployment is accelerating their evolution
Take a look in your wallet and what do you find? In all likelihood, bills and coins. A variety of credit cards. A driver's license. A transit pass. A voter registration card. A library card. A video rental card. Insurance cards. Frequent flyer and car rental cards. A telephone charge card.
By the end of the century, all of these documents might be replaced by just two or three smartcards. Because they can store and protect relatively large amounts of data, smartcards are being used in a number of ways around the world, replacing a wallet's contents bit by bit. Stored-value cards were in place last year in Atlanta, Ga., at Olympic venues standing in for coins and bills. A health card identifying the holders insurance provider and account number has been issued to every citizen of Germany, and plans are in place to add such medical information as the name of the holder's doctor, blood type, allergic reactions, medications, next of kin, and instructions in case of emergency. Smart social security cards in Spain interface with a kiosk system that can provide updated information on benefits and eligibility, as well as pertinent job opportunities.
Today, most smartcards handle a single application, but will realize their true value when a single card can address multiple applications. For example, a credit card could have a stored-value function for small purchases in addition to frequent flyer and rental car information. It might work with a cellular phone to connect the user to a home banking service. One step toward this goal was last falls announcement by VeriFone Inc. Redwood City, Calif., of a system called VeriSmart, which permits a smart phone or a PC to act as a "personal ATM" (automatic teller machine) in the home, loading cash value onto a smartcard.
The smartcard will also be a tool for addressing the "customer of one" applications of special interest to the card holder will be loaded onto the card to make life easier. Eventually, people may customize generic cards themselves from a menu of applications. In a report on the smartcard industry semiconductor industry analyst Dataquest Inc., San Jose, Calif., recently wrote, "Although some standards issues, infrastructure issues, and software issues remain to be resolved, chip cards hold the promise of being one of the worlds highest-volume markets for semiconductors."
As a single card comes to hold more information and relates to more aspects of its holder's life, privacy concerns will have to be addressed. Note, however, that the information stored in a smartcard is usually already available in some format or another; the smartcard merely makes that information portable and puts it at the disposal of the card carrier.
The smartcard application that will be most popular in North America may involve a portable token -- a card, a key, or some other familiar shape -- for conducting transactions over the Internet, particularly for home shopping and home banking. How can such sensitive information as financial transaction data be safely communicated across a hacker's paradise like the Internet?
Advanced cryptographic functions will be required. Public key encryption (PKE) will be part of the solution in at least two ways [see "Locking the e-safe,"]. First, PKE (often a one-session key) will be used to encrypt data to be transferred with the receivers public key. This data will be readable only by a receiver with the secret key. The second use will be for digital signatures: a piece of data encrypted by the senders private key, proving that only the authorized sender could have sent a message or that it has not been modified. PKE capabilities using Smartcards provide for portability, cutting the tie to any specific computer, phone, or other "site."
These smartcard applications require the development of infrastructures that are global, interoperable, easy to update, and capable of supporting several applications concurrently. The Dataquest report on the smartcard market indicated that 156 million smartcard microcontroller devices would be shipped in 1996, increasing to 990 million in the year 2000. Suppliers of smartcard silicon include Motorola, SGS Thomson, Philips, Siemens, and Hitachi.
Defining terms
Access card: a machine-readable card that is used to achieve computer access, physical entry, or passage.
Contactless card: an integrated-circuit card that enables energy to flow between it and the interfacing device without needing contacts. Instead, induction or high-frequency transmission techniques are used through a radio frequency interface.
Electronic purse: a card application that stores value for small transactions. A card may be dedicated to the purse function or contain memory and programs for other applications, as well.
Electronic wallet: in general, an IC card or super smartcard that can execute a variety of financial transactions and identification functions. More sophisticated than an electronic purse, an electronic wallet may serve debit, credit, prepayment (cash) card, and other functions.
Integrated-circuit card (ICC), IC card, or microcircuit card: a card containing one or more embedded integrated circuits. The category includes both memory cards and smartcards.
Memory card: an IC card that can store information but that lacks a calculating capability -- that is, it lacks a microprocessor.
Multi-application card or universal prepayment card: a card that can support a number of applications, which may be provided by different parties.
Prepayment card, cash card, stored-value card, or decrementing-value card: a card purchased complete with stored value, which is decremented whenever the card is used.
Smartcard: an IC card with memory and a microcontroller, so that the card is capable of making decisions.
Physically, a smartcard resembles a credit card having one or more semiconductor devices attached to a module embedded in the card's top left corner, providing contacts to the outside world [Fig 1]. Also referred to as an integrated-circuit card, or ICC, the card can interface with a point-of-sale terminal (POS), an ATM, or a card reader integrated into a phone, a computer, a vending machine, or any other appliance.
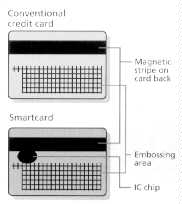
[1] An area in the smartcard has been defined to hold the module containing the integrated circuit. The smartcard complies with the magnetic-stripe and embossing areas defined in the ISO 7813 standard for financial-transaction cards. This module provides contact with the card reader.
The semiconductor device embedded in a true smartcard is a microcontroller. It is the microcontroller that makes a card smart and capable of undertaking a range of computational operations, protected storage, and decision-making. Other silicon chips, such as memory devices can be embedded, too, but cards with these alone are called memory cards.
Smartcards have two main advantages over magnetic-stripe cards. They can carry 10-100 times as much information (current smartcards provide up to 8KB, about two typed pages) and hold it more robustly and securely than do typical magnetic-stripe cards. (Anyone with larceny in mind might want to know that most magnetic-stripe cards can be read and written with equipment readily available from many hobby stores.) In conjunction with a terminal, smartcards can also execute complex decision-making tasks, including handshake routines that prove the cards validity to the terminal and the terminals validity to the card -- a form of mutual authentication that can reduce fraud and misuse [Fig. 2].
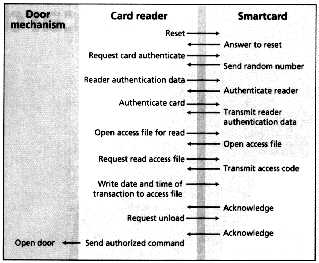
[2] The interaction between the card reader and the smartcard ensures that both are authorized to undertake operations. When the reader has a card inserted in it, it resets the card, which responds with an answer to reset (ATR). Its ATR provides specific information and often conforms to the ATR described in the ISO 7816 standard. Both the reader and the card use a random number in an algorithm to obtain a result that, when successfully compared, authorizes the card and the reader to continue with the desired operation.
The main benefits of smartcards are increased data security, an active anti-fraud capability, flexibility in applications, a multipurpose capability, and off-line validation. In practice, these features are interrelated, but perhaps the most important of them is a higher level of security than such alternative technologies as magnetic-stripe cards or simple memory cards can provide. This makes smartcards viable in applications involving money, proprietary secrets, and personal data. A smartcard, for example, can be combined with biometrics -- information representing fingerprints, hand geometry, and so forth -- to uniquely "connect" the card holders identity to the card.
Current standards define the mechanical, physical electrical, and handshake interfaces between the card and the reader without restricting the silicon embedded in the card to a particular application. Because smartcards have global applications, standards are necessary to provide for future uses and for technological advances while also ensuring that the cards will be universally accepted and that tomorrow's applications can work together.
Standards dealing with digital cellular telephones, Internet access, airline ticketing and frequent flyer programs, and financial applications are being addressed globally [Table 1]. The EMV (Europay/MasterCard/Visa) standard addresses the use of smartcards in financial payment systems, defining the basic protocols for communication between cards and readers. In 1996 Microsoft Corp., Redmond, Wash., announced a joint effort in this area with Hewlett-Packard, Bull CP8, Schlumberger Electronic Transactions, and Siemens-Nixdorf Informationssysteme. Their aims to promote the acceptance of smartcards in the PC environment, and to develop a set of open standards enabling PCs to work with such smartcard applications as network access and electronic commerce. Microsoft also announced its Internet Security Framework, which uses digital certificates -- either in software on a users PC or on a smartcard device -- to secure Internet connections.
Table 1. Smartcard-related standards and specifications
| Standard | Title/Description |
|
ISO standards for identification cards |
- |
| ISO 7810 | Physical characteristics |
| ISO 7811 | Recording techniques (six parts) |
| ISO 7812 | Identification of issuer |
| ISO 7813 | Financial cards |
| ISO 10373 | Test methods |
| ISO 7816 | IC-cards with contacts (six parts) |
| ISO 10536 | Contactless (close coupling) IC cards (CICC) (four parts) |
| ISO 14443 | Contactless (remote coupling) IC cards (four parts) |
|
General ISO Security Standards |
- |
| ISO 9796 |
Information technology -- Security techniques -- Digital signature giving message recovery |
|
Industry-specific standards (financial, telecommunications, airlines) |
- |
| ISO 9992 |
Financial transaction cards--Messages between the IC card and the card-accepting device. (two parts) |
| ISO 10202 |
Security architecture of financial transaction systems using IC cards. (eight parts) |
| EMV |
IC card specifications for payment systems developed by Europay EMV International SA, Mastercard International Inc., and Visa International Service Association (three parts) |
| ETSI GSM 11.11 |
European Digital Cellular Telecommunications System (Phase 2): specification of the Subscriber Identity Module-Mobile Equipment (SIMME) Interface |
| ETSI GSM 11.14 |
European Digital Cellular Telecommunications System (Phase 2+): specification of the SIMME Interface for SIM Application Toolkit |
| ANSI T1P1 | U.S. Telecommunications Standard |
| IATA JPSC 791 |
International Airline Transportation Association (IATA) Joint Passenger Service Committee (JPSC) Smartcard specification |
Source: Smart Card Forum
The microcontroller used in Smartcard applications [Fig. 3] contains at a minimum a central processing unit (CPU) and blocks of memory including RAM, ROM, and nonvolatile memory -- usually electronically erasable programmable ROM (EE-PROM).
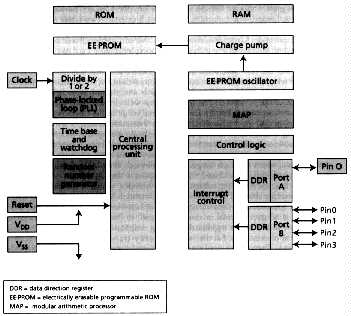
[3] The five I/Os of the smartcard microcontroller conform to the ISO 7816 smartcard standard. The three types of memory vary in their retentiveness: ROM contains unchanging data and the operating system; RAM retains data only while power is applied, so is used as a scratch pad by the CPU for its calculations; and EE-PROM stores data that changes (transaction data, say) but that must remain constant when power is removed. The charge pump raises the voltage as needed to write to the EE-PROM. On some devices [lightly shaded], a co-processor enhances performance of the encryption or decryption algorithm. The phased-lock loop increases the externally provided clock frequency for internal use in the modular arithmetic processor (MAP), an accelerator that optimizes calculations used for encryption and decryption algorithms. Numbers created by the random number generator serve as the algorithm's keys or seeds.
The inclusion of a variety of memory types helps suit the smartcard microcontroller to a range of applications. For example, RAM serves to calculate results and stack memory, ROM to store the operating system, fixed data, standard routines, and lookup tables. The nonvolatile memory is the most versatile; EE-PROM, for instance, serves to store information that must not be lost when the card is not connected to a power source but that must also be alterable to accommodate data specific to individual cards or any changes possible over their lifetimes. This information might include a card identification number, a personal identification number (PIN), authorization levels, cash balances, and credit limits. Typical features for today's applications include an 8-bit CPU, 128-780 bytes of RAM, 4-20Kb of ROM, and l-16Kb of EEPROM on a single die, plus, as an option, an on-chip hardware encryption module.
Although the smartcard microcontroller works like any microcontroller, it is fundamentally different while maintaining instruction set compatibility, it is designed with security in mind. For example, the smartcard and nonsmartcard versions of the Motorola 68HC05 8-bit microcontroller display several clear differences.
Probably the most obvious is the single I/O of the microcontroller in the smartcard versus several 8-bit ports for a normal microcontroller. In fact a smartcard device has only five standard pinouts: I/O, clock, power, ground, and reset, whereas other microcontrollers usually have at least 16 pins and sometimes more than 50.
Memory configurations are different, too: a smartcard uses only on-board memory with relatively large amounts of nonvolatile memory usually EE-PROM. The EE-PROM is programmed by an on-chip charge pump controlled by the CPU and not accessible directly by external command. A third difference is that the device appears stripped down as compared with nonsmartcard devices, since it contains no additional peripherals such as analog-to-digital converters, pulse-width modulators, and serial or parallel interfaces.
Smartcard devices, which are very constrained by die size, use very dense memory elements. Surprisingly, this restricted die size does not automatically lead to the use of state-of-the-art fabrication geometries. First, cost is a great factor in smartcard applications, which may involve issuing tens of millions of cards. Second large volumes also require established and extensive fabrication facilities. Third, the need for security means that a well-defined, characterized and tried-and-true process is needed, since a new one might include some as-yet-undetected anomaly that could compromise security For these reasons, smartcard microcontrollers tend to be fabricated in 0.7-1.2-mum CMOS technologies, moving to finer geometries as they become less expensive and fully characterized.
The use of smartcards in security-sensitive applications heavily influences the design and handling of the card -- silicon and software alike. Microcontrollers used in smartcards are specifically designed to restrict access to stored information and to prevent the card from being used by unauthorized parties. To accomplish this, each microcontroller manufacturer includes its own set of security features, many of which are never discussed since they are useful only if potential hackers do not know that they exist.
Smartcard devices are designed to work only in well-characterized operating environments since one attack scenario involves attempts to force cards to operate outside normal operating voltage or clock frequency ranges, in hopes of uncovering weaknesses that can be exploited. Most devices therefore detect and reset whenever they are pushed outside their normal operating ranges. A card's reactions upon sensing attempt at fraudulent access range from ignoring the access request to locking up the card from all future use. Other features provide special functionality to areas of memory or make it difficult to access portions of memory or circuitry directly Such techniques as memory-scrambling, hidden layers, and dummy circuitry may be added to confuse hackers.
No system can be considered entirely secure all must constantly be evaluated and improved. Given enough resources, time, ingenuity, and perhaps luck, almost any system can be broken. But we are not without recourse. Security aims to make a system more difficult to break than the effort would be worth to criminals. As a result, we see different levels of security precautions, from simple PIN numbers to full biometrics, or from simple algorithms to Data Encryption Standard (DES) or Rivest Shamir, Adelman (RSA) encryption. For example, in financial cards, a device can use PIN numbers, or fingerprints or some other biometric, to verify users. The microcontrollers ability to perform certain algorithms enables the card to verify the reader as well as the reader to verify the card, frustrating such scenarios as occurred in a Washington, D.C., mall, where a fake ATM machine was set up to collect names plus account and PIN numbers for fraudulent use. The EE-PROM can record transaction data for later reconciliation.
But any system is only as secure as its weakest link. Security must be regarded as a system-wide undertaking, for it is pointless to double-lock the front door if the back one is wide open. Also, technology is a wonderful thing but criminals, too, can use it as new equipment and techniques become available or less expensive the barriers to cracking a system may weaken. Recently Bellcore announced a paper, "Cryptanalysis in the presence of hardware faults" (available at www.bellcore.com), that proposed a theoretical method for breaking an asymmetric encryption code once a computer (or a smartcard microcontroller) had been forced into faulty behavior
The Smart Card Forum, a multi-industry membership organization headquartered in Tampa, Fla., has stated that it does not regard this approach as a real-world risk, since in smartcard applications more than one technique is used to protect the security of the entire system. But the Bellcore methodology for breaking algorithms -- as well as similar theoretical approaches, such as the one taken by two Israeli researchers, Eli Biham and Adi Shamir -- highlights the need to analyze and evolve the security of any system continually.
Although most smartcard microcontrollers are based today on 8-bit machines, the only real limitation on the type of CPU, memory, or technology used comes from the fact that they must be embedded in a flexible plastic card. To prevent cracking, it is therefore desirable to minimize the size of the silicon die. Most references suggest a maximum of 25 mm2 but an even smaller die is preferred. As IC feature geometries shrink more processing power and memory can be fitted into a given amount of silicon. Die thickness is also a factor, not only because it must fit within the card's thickness but also because thin enough silicon actually bends with the card, again reducing the risk of cracking.
Silicon used in future smartcards will be driven by the intended uses. Newer applications make ever-increasing demands for data management and for various algorithmic calculations involving security and data compression. Support for such encryption algorithms as an RSA public key for higher-security applications is another requirement. Multi-application cards will create additional demands for security and control on the silicon.
Moreover, as the world moves toward more mobile electronic devices, such as portable phones, computers, and personal digital assistants (PDAs), the lower voltage/current drain ICs designed for them are affecting smartcards, too. The voltage level began at 5 V, has now reached 3 V for such applications as GSM (Global System for Mobile Communications, the European digital cellular telephone system), and will migrate to 1.8 V in future.
Nonvolatile memory will eventually have to provide larger data storage capacities for individual applications such as health and ID cards and for the migration to multi-application cards. With this increased need for capacity, read write times become important to avoid unacceptably long transaction times and to personalize the card in ways that are not too time-consuming and costly for the issuer.
Another area that will be transformed technologically is the reader, or card-accepting device. New markets will require new products, such as electronic "wallets" and biometric readers of voices, fingerprints, and hand geometries. These products will each drive developments in such areas as low voltage/current drain security and data storage -- by and large. They will also drive other technological changes. Some electronic wallets, for example, will require a form of RF communication for "over the air" communication and networking capabilities will be needed to interface smartcards to the vast array of electronic devices, such as desktop laptop computers PDAs, and the new generation of set-top boxes for homes. Small, high-density packaging and greater integration will be key.
Most smartcards are "contact" cards; they require physical contact between the card and the pins in the reader. A growing set of applications use "contactless" cards, where there is no such direct physical contact. Close-coupled cards operate through inductive or capacitive coupling between the card and a reader less than 1 mm away. Remote-coupled cards operate over distances up to 10 cm and communicate by radio frequency signals, which also supply the card with power -- an arrangement calling for very low-power devices.
Remote-coupled contactless cards are attractive in applications where throughput is a critical factor. Transit applications benefit from contactless cards because they remove the time-consuming need to insert a ticket or card into a reader Instead, the commuter simply waves a card in the general proximity of a reader or walks through a specially equipped turnstile. Transit systems that have tested contactless cards include those in Washington, D.C.; Hong Kong; and Manchester, England.
Contactless cards can also be more physically robust than their contact-type counterparts because there is no potential for wear and tear on the contacts, and in addition the readers are less vulnerable to wear and to vandalism. Thanks to these advantages, many contact-type applications will evolve into contactless ones as standards proceed to solidify and the costs fall to near-panty.
Contactless cards include capacitive plates or a coil for coupling with the reader and a microcontroller with analog circuitry to condition the data transmitted over the interface. Currently, most contactless-card solutions involve two silicon devices one, similar to those used in contact cards, that is either a microcontroller or a memory device, as well as another device to provide the RF interface.
Here, the challenge is to combine digital and analog circuitry in one device. One-chip silicon solutions have begun to appear in the market but have yet to reach volume production. In the meantime, efforts are under way to standardize hybrid cards that can communicate in both contact and contactless systems. Lufthansa AG, Germany's national airline, has already begun issuing a hybrid card to frequent fliers; the contactless part serves as an ID card for its paperless ticketing system, and the contacts conform to the specifications for a standard European smart credit card.
The smartcard industry has been evolving for over two decades. In the early to mid-1970s, the concept of a microcontroller on a credit card emerged in Europe and Japan. In 1974, Roland Moreno created Innovatron SA and filed the first of his many patents in the field of IC card systems. Innovatron, which continues to license its smartcard technology, has established several operations that promote smartcard applications.
The initial drive to develop smartcards was prompted by losses being suffered in France from credit card fraud and the production of counterfeit magnetic-stripe cards. In the mid-'70s, the French government, French banks, and Bull CP8 started working together to find a way to reduce financial fraud in the French banking system The concept of a credit card with a microcontroller that would control access to information and reduce counterfeiting appeared to be the solution.
For the smartcard industry, the years from 1977 to 1988 were a period of development. In 1977, the first actual smartcard was produced, an interim two-chip solution, jointly developed by Bull CP8 and Motorola, that contained a microcontroller and a separate memory device. This was quickly followed, in 1980, by the introduction of Motorola's first one-chip solution, known originally as CP8 and then as SPOM 01. This device was for many years a staple of the French banking system, used as a bank card with account and PIN information and a record of financial transactions that could be used to reconcile questionable activity.
By 1989, the smartcard was becoming a known and viable tool in the European and more especially the French market. In that year, Bull CP8 began to license smartcard technology for use outside the original French banking application.
During the early '90s, smartcards were incorporated into a variety of applications. In 1990 they were first used as a subscriber identification module in the GSM digital mobile phone application. They were also employed to reestablish security in pay-TV applications: a card inserted into the set-top box provided a unique address, security algorithms, channel access, keys, and so forth; whenever a system was "hacked," the service provider could reissue a card with new information -- and without having to recall the set-top box. The original application in French banking reached full implementation in 1993, when all banking cards were converted into smartcards.
Several cultural, infrastructural, and political factors greatly affected the spread of smartcards in Europe. The formation of a centralized government-backed organization, Groupement des Cartes Bancaires, to oversee the introduction of the technology helped get it off the ground. Also, the high cost and the less developed infrastructure of telecommunications in certain European countries made it advantageous to look for a way to perform off-line transactions. Many countries in Eastern Europe and in what used to be the Soviet Union are analyzing smartcards to address problems with poor or outdated infrastructure, fraud, and rapidly changing circumstances.
Why has it taken so much longer for smartcards to take off in the United States? In the first place, some of these cultural and political drivers are absent. The country has an excellent telecommunications infrastructure. There is no governmental or centralized mandate in any of the traditional application areas of smartcards. But the industry is evolving. The activities of Europay, MasterCard, and Visa (EMV) in developing specifications for financial-transaction cards will have a major impact on the U.S. market and the rest of the world. Nonetheless, it is felt that a smartcard will have to be able to handle several applications for the technology to gain widespread acceptance in the United States.
The use of smartcards as stored-value cards -- holding the digital equivalent of cash directly, instead of pointing to an account or providing credit -- is currently generating great interest. When a card of this kind is used to make a purchase, the digital equivalent of cash is transferred to the merchants "cash register" and then to a financial institution. Stored-value cards are either replenishable (value can be reloaded onto the card using an ATM or some other terminal) or nonreplenishable (the card is decremented in value for each transaction and thrown away when all its value is gone). But recent trials have indicated that the stored-value function alone is not attractive enough to consumers to encourage wide use of smartcards.
French banking boasts the longest-running smartcard application to date: a bank card can authorize transactions off-line, without recourse to a central computer, when cardholders enter their PINs. Visa and MasterCard each rolled out stored-value applications during the past year: MasterCard in Canberra, Australia; Visa, along Australia's Gold Coast and in Atlanta just before the 1996 Olympics.
Visa's Atlanta program was designed to prove the interoperability of Visa SVCs issued by three banks (Nations, First United, and Wachovia), manufactured by three companies (GemPlus, Schlumberger, and Giesecke & Devrient America), and using silicon from three semiconductor providers (SGS Thomson, Motorola, and Siemens). Two types of cards were available: a replenishable prepaid one tied to the cardholder's bank account and a nonreplenishable card available in $20, $50, and $100 variants.
From a technical standpoint, the results from Atlanta were positive, since the cards and the infrastructure performed very well. In addition there was fairly good usage in the Olympic stadiums and on the transit system. However, none of the banks managed to issue the number of cards that had been targeted. Apparently, many of the cards are now being held as collectors items by card collectors and by visitors to the Olympics!
Mondex, which is also attracting a lot of attention, is an electronic purse system that lets electronic currency pass from "hand" to "hand" indefinitely without being redeposited, provides for anonymous money transfers, and handles several national currencies. The concept includes an electronic wallet used to reload the card and to perform card-to-card transactions, as well as Mondex-ready home and office phones that facilitate transactions with the bank. Mondex was developed by National Westminster Bank PLC, London, and has been undergoing trials in Swindon since 1995; a trial will take place in Guelph, Ont., Canada, later in 1997.
Over the past year, such major banks as the Canadian Imperial Bank of Commerce, the Royal Bank of Canada, the Hong Kong & Shanghai Banking Corp., and the U.S.-based Wells Fargo & Co. have signed up to use Mondex, recently spun off by Nat West as Mondex International Ltd., a joint venture with 17 bank partners worldwide. Other banks have indicated that they, too, would sign up for franchises. Last October, MasterCard announced plans to purchase 51 percent of Mondex.
Another electronic purse system was developed by Banksys, which operates the Belgian debit and credit network system. Called Proton, it has already expanded into Australia, Brazil, Holland, Sweden, and Switzerland. This year will see the launch of a Canadian pilot project, under the brand name Exact, in Kingston, Ont. The experiment is to include the use of 20 000 cards issued by the Toronto-Dominion Bank, the Bank of Montreal, and 800 merchants.
At the end of 1996, Visa and MasterCard were to start New York City trials showcasing the interoperability of smartcards from various institutions. Citibank and Chase Manhattan will be issuing cards accepted by over 1000 vendors in Manhattan. The proposed acquisition of Mondex by MasterCard will delay this project until the fourth quarter of this year.
Smartcards are only the most visible part of a larger system. Current versions, made by such firms as Schlumberger, Gemplus, and Bull CP8, range in price from less than $1 to about $20, including the cost of silicon, the module (the chip package providing connections to the outside world), and the plastic card itself. By comparison, magnetic-stripe cards cost a niggardly 10-50 cents, depending on the quality of the card; whether it includes a photo, a hologram embossing, and so forth; and the number of cards that can be made simultaneously.
Besides the card itself, there are costs associated with setting up smartcard systems. Software and networks -- for example, ATMs and POS terminals -- originally designed to handle cash, credit, or checks must be modified to deal with smartcards. More than five million devices in the United States can deal with conventional credit cards, but some are manual machines that print embossed information. A major investment will be required to update this infrastructure
As for the benefits, the stored-value financial smartcard is attractive to the consumer on two counts. It reduces the amount of change that must be carried and it can be used in small transactions where credit cards or checks would be unrealistic.
The financial players find the stored-value card attractive because it opens up a new market for financial services. Visa estimates that US $8.1 trillion worth of cash transactions take place yearly in the world's top 29 economies. Many are small-cash transactions currently ignored by financial institutions on the grounds that the overhead costs of credit cards or checks would be too high to allow a profit. Moreover, since stored-value cards carry monetary value directly, instead of pointing to an account, they can be used by children, tourists, and others who do not have local bank accounts.
Merchants appreciate the stored-value card because it reduces the need to count move, store, and safeguard cash, a "hidden" expense estimated to account for about 4 percent of the value of all transactions. In France, too, one of the benefits of telephone cards has been a drastic reduction in vandalism at phone booths.
So smartcards provide rewards in convenience, in the fight against fraud and vandalism, and in long-term savings. But who will foot the initial bill? This has yet to be resolved.
Will card carriers pay through a yearly or transaction fee? Will merchants finance the upgrading of their equipment so as to increase sales? Will banks foot the bill? And what about credit institutions like Visa and MasterCard, whose expenses might be offset by a reduction in fraud, which cost them over US $1.1 billion worldwide in 1994?
So far none of these parties has chosen to step forward. Someone will have to do so before smartcards are able to gain worldwide acceptance.
Table 2. Smartcard projects around the world
|
Program (locations) |
The players |
No. of cards, status |
Date begun and description |
|
Stored value/ electronic purse |
Over two dozen projects in operation around the world, with several having hit the 1-million-card level but with most in the pilot phase |
- |
- |
|
Mondex (worldwide) |
Shares in Mondex International held by MasterCard (51 %) and major banks on five continents |
50 000 in various pilots around the world |
1992: anonymous cash scheme, which allows peer-to-peer transfers and handles up to six currencies, was launched by NatWest; two-tier ownership, with international and country licenses established in 1996 |
|
Danmont (Denmark) |
Danmont, major banks, Danish phone company |
1 000 000 in continuous operation |
1993: the first broad-scale electronic purse system uses disposable cards, but a reloadable function is planned |
|
Proton, Cash, ChipKnip (worldwide) |
Belgian, Canadian, Swiss, Dutch, and other banks, plus American Express |
2 000 000 in 1996; 12 000 000 in '97 |
1994: system designed this year by Belgian banks and has since been licensed to banks in Switzerland, Holland, Brazil, Australia, Sweden, and Canada for their programs, but under different names in each country; American Express licensed for worldwide use |
|
Visa Cash (worldwide) |
Visa member banks |
2 000 000 in several parts of the world |
1996: pilot at Atlanta Olympic Games, programs are being initiated in over a dozen nations, using disposable and reloadable cards |
|
Clip (pan-European) |
Europay member banks |
50 000 in pilot |
1996: pilots for Clip, Europay's electronic purse scheme, began in Austria, Iceland, and the Czech Republic, with other existing national programs announcing intent to incorporate Clip |
| New York City pilot | Chase Manhattan and Citibank |
50 000 pilot launch in late 1997 |
1997: program will be the first to accept both Visa Cash (Citibank) and Mondex (Chase Manhattan) stored-value schemes at same terminals |
|
Other financial uses |
Wide variety, including credit/debit card security, bank account information, and corporate cash management security |
- |
- |
|
Group Carte Bancaire (France) |
Major French banks |
24 000 000 ongoing |
1992: since this year, every bank card in France has contained a chip for cardholder ID and transaction authorization |
|
Taiwan Financial Services Card |
14 Taiwanese banks and Financial Information Service Center |
700 000 in 1995 |
1993: system uses smartcards and point-of-sale (POS) terminals to deliver financial services to banking customers |
|
Zolotaya Korona (Russia) |
Over 100 Russian banks |
150 000, at roll-out; 400 000, now |
1994-95: debit/credit smartcards, for use with automatic teller machines (ATMs) and terminals, support varied banking applications, including electronic purse |
|
U.S. Treasury Electronic Certification Program |
U.S. Treasury |
5000 ongoing |
Early 90s: smartcard identifies disbursing officers at Federal agencies that send payment information to Treasury Financial Centers that execute transactions |
Source: Ben Miller, CardTech/SecurTech Inc.
____________________
About the author
Carol Hovenga Fancher, who joined the Motorola Semiconductor Products Sector in 1992, is the Americas smartcard strategic marketing engineer for customer-specified integrated circuits of the Consumer and Smartcard Microcontroller Division. Before joining Motorola, she held engineering and marketing positions with Tracor, Austin, Texas; Ford Microelectronics Inc., Colorado Springs, Colo.; and Fraunhofer Institute fur Integrierte Schaltung, Erlangen, Germany.
Additional information on smartcard rollouts can be found in "Get Set! Smartcards Are Coming to America," by Patrick Gauthier, published in Portable Design, May 1996, Vol. 1, no. 6, pp. 31-34.
Smartcard technology is also discussed in "Cryptographic Smart Cards," by David Naccache and David M'Raihi, in IEEE Micro, June 1996, Vol. 16, no. 3, pp. 14-24.
Various organizations are involved in developing smartcard standards. The Smart Card Forum has prepared a description of pertinent standards: Standards & Specifications of Smart Cards -- An Overview, available by calling 813-286-2339. Standards of the International Organization for Standardization and the American National Standards Institute can be ordered by phone at 212-642-4900 or by fax at 212-302-1286. European Telecommunications Standards Institute standards can be ordered from (33+4) 9294 4241: fax. (33+4) 93951 8133.
Michael C. McChesney
Security First Technologies
Home banking has evolved from the telephone to dial-up computers and now to the World Wide Web
When home banking was introduced in the United States, in the mid-1980s, the top-of-the-line computer was the IBM PC/XT which had at most 640KB of memory and a 20-MB hard drive. Fewer than half a million modems were in use, and Hayes had just introduced its 1200-baud model for $350. "User-friendliness" was still an abstract idea particularly to the in-house bank programmers providing software for home users. Is it any wonder that home banking was such a huge failure?
A short decade later, and how things have changed. Today's standard computer uses a 100-MHz Pentium chip, 20MB of memory and 1 GB of hard-drive space. New computers now routinely come with 28.8-kb/s modems and CD-ROM drives. Upward of 23 million homes are connected to the Internet. And more and more computers are being used with the new generation of home banking software. More importantly, many new access devices are being developed and brought to market that will transcend the PC-literate and ultimately reach everyone. Web TV is an example.
Even in its dimmest moments, home banking was inevitable. People in the United States have less and less patience for driving to banks and waiting in teller lines. Total non-branch activity is growing at a rate of 15 percent a year. Statistics show that automatic teller machines (ATMs), telephone banking, and computer-based banking account for over 50 percent of all banking transactions today
Yet the United States has not been as quick as some other cultures to adopt electronic commerce. Electronic banking accounts for an estimated 90 percent of Japan's financial transactions. France's proprietary network, Minitel with 14.4 million users, offers services from more than 10 000 companies. By comparison, only 1percent of U.S. banking transactions are accomplished by network. But a boom is on the way. Jupiter Communications, a New York City technology research firm, predicts that the proportion of network banking transactions will grow to 6 percent by the end of 1997 and perhaps to 75 percent by the year 2005.
North American banks are getting ready. About 79 percent of them now offer home banking services, ranging from electronic bill payment to portfolio management.
Internet banking is a new concept in the United States. The first financial institution to use the World Wide Web as its primary delivery channel was Security First Network Bank (SFNB), which opened its virtual doors on Oct 18, 1995 [Fig .1]. Virtual Financial Manager, the software behind SFNB, is being marketed to financial institutions around the world through its wholly owned subsidiary Security First Technologies, which is a merger of the former Five Paces Inc. and SecureWare Inc. To date, 14 banks -- including Huntington Bancshares, M&I Bank, Salem Five Cents Bank, West Coast Savings, the National Bank of Commerce (NCBC), Republic Bank of St. Petersburg, and Australia and New Zealand Banking Group Ltd. (ANZ) -- have adopted the package as their front-end processor for Internet access.

[1] Seated at a home computer, a customer enters a network bank through an electronic lobby [left]. Clicking on Customers provides several banking options, including bill payment, transfer of funds, or simply reviewing activity in the account's Transaction Register [below].
Meanwhile, on Sept. 9, 1996, IBM Corp. joined with 15 U S and Canadian banks to create the Integrion Financial Network, which will develop a system offering transaction-processing services comparable to those now offered by CheckFree and Visa. These services will be offered through an Internet interface.
Interest in Internet banking is global In France, for example, 16 banks have Internet home pages. One advantage is lower costs. Electronic payments cut processing fees, since fewer paper checks must be handled. By providing statements and check images on-line, a bank can save a few dollars per account each month on mailings (though paper statements must still be mailed out). Physical overhead expenses are lower, too, since fewer brick-and-mortar branches are needed. And significant savings come from the smaller number of employees needed to service customers: an average electronic transaction costs only pennies as compared with 54 cents for the average transaction handled over the phone by a combination of voice-response systems and customer call centers, and $1.10 for the average in-person transaction.
For customers Internet banks can provide 24-hour access to an account, allowing them to pay bills, to categorize income and expenses, to produce cash-flow reports and to print budgets whenever they please.
Three main models of electronic banking have emerged: PC-based banking, or "fat client"; the 'thin-client-stateless" architecture; and the "thin-client-stateful" model.
Traditional PC-based banking relies on applications, such as Intuit Inc.'s Quicken or Microsoft Money, that reside on the customers PC, the client machine. It is sometimes called a fat client because every application requires dedicated software on the PC.
Such home-banking applications store data in a database management system on the local PC. The application can add value to that data (for instance, budget categories or payee lists) and has business logic to organize and present data in useful forms. For example, the customer can tell the application to send an electronic payment for a car note or a mortgage on the 15th of each month. Communicating through an intermediary front-end processor residing on the server at the bank, customers can dial into it at any time to download account information.
While this is a convenient approach, it has drawbacks. With this type of PC-centered interface, customers must maintain the software on their own computers. They are responsible for new releases and upgrades, as well as for downloading and updating information. The connection with the bank can be made only through the computer containing the software. From the banks point of view, the software manufacturer controls the interface -- in essence, the way the bank is presented to its customers.
The second of the models of electronic banking, the thin-client-stateless architecture, runs many applications with only one resident software program an Internet browser. There is no database storage, no value-added capability and only minimal business logic on either the client browser system or the intermediary front-end processor server. Instead, raw data is simply grabbed from the legacy mainframe, often using "screen scraping" techniques, and then presented via Hypertext Markup Language (HTML) screens to the customer with little or no opportunity for enhanced features or services. This approach effectively dumbs down the browser-based service to the minimal functionality of a voice response system.
A screen scraper performs essentially the same function with a visual interface. The application can be used to pay bills and transfer funds, and it is accessible to the customer via any computer with a network connection. From the bank's standpoint the interface is inexpensive to build and maintain -- particularly since most banks already have a voice response system. The bank's difficulty in adding functionality and value to data will relegate this approach to the low end of Internet banking technology.
Most voice response systems are based on PCs running under IBM's OS/2 operating system. While this architecture can manage 60 000 or more phone inquiries a day, the processing required for Internet presentation is more complex. As the number of Internet banking customers grows, problems could develop if the system is unable to expand.
In the third model of Internet banking, the thin-client-stateful approach, the access device remains a thin client requiring only an Internet browser, so the interface resembles the one used in the thin-client-stateless model. But the business logic and database storage kept on the local PC in the fat-client model are moved to the intermediary front-end processor The term "stateful" refers to the ability to extend and add value to the data, with categories, budgets, payee lists, and so forth. Security First Technologies calls this technology a "consolidation engine."
The thin-client-stateful approach is the new paradigm for Internet banking. It offers the functionality of a PC-based financial manager coupled to Internet access. This model can also consolidate information from disparate systems Banks have traditionally gathered large amounts of information about their customers. But it is often stored in separate databases in different departments for example, mortgage applications would be in one database, checking transactions in another. Only recently have banks begun to undertake "data mining," the process of integrating these databases to provide a total financial picture. According to Information Week, 45 of the top 100 U.S. banks had installed data-mining applications by mid-1996, and 50 more were planning to.
To remain competitive in an Internet Age banks must make better use of data mining by greatly expanding the amount of detailed customer information available to the data analysis software tools. Such information should include loans, brokerage, insurance, and credit cards. Cross selling decisions cannot be made solely on the basis of demand deposit account data.
One example of how a total financial picture might work involves the incorporation of credit cards. Credit card information maintained by a separate processor, is incorporated into a relational database and electronically integrated with other customer data. The customers credit card balance, interest fees, and payment history can also be added to the data displayed on screen This ability to relate host data to transaction records demographic profiles, and customer preferences allows the bank to give users a customized interface, updated each time they log on.
For example, a customer might ask that credit card balances be automatically paid from her checking account after transferrals from money market accounts, or might want to have certain stocks tracked, or could request stock alerts when certain pricing or trading levels are reached. Each of the three approaches has advantages for certain segments of the population. A few power users will continue to keep dedicated financial management packages on their own PCs, regardless of the interface they use. It is simply uneconomical for a bank to load its server with every specialized capability a power user might desire
Another segment of the market neither wants nor needs a complex interface. They want only to be able to see their bank balances pay a few bills and occasionally transfer money. The thin-client stateless model suits not only their needs but also those of a bank seeking to expand an existing voice response system with an Internet interface.
The thin-client-stateful approach is the one adopted hy Security First Technologies for its Virtual Financial Manager, which is used by SFNB and by internal development projects at several large banks, including Wells Fargo and those in the Integrion network.
Recognizing the value of all three methods Security First Technologies adopted a three-tier architecture for Virtual Financial Manager [Fig. 2] so that customers could use it in a variety of ways. To accommodate people who want to maintain personal financial managers on their own computers, Virtual Financial Manager supports all open systems, such as Open Financial Exchange from Intuit, Microsoft and CheckFree. Customers who want only to see bank balances and pay bills have the option of a simple interface. Those who want more functions can tailor the interface by adding services to the basic ones it offers.
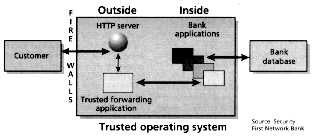
[2] Security First Technologies' Virtual Financial Manager utilizes a three-tier architecture. The presentation (or customer interface), the business logic, and the database are maintained separately to facilitate the customization of the interface and to ensure the integrity of applications.
Security is always an issue when banks consider electronic commerce. In the Security First Technologies model security procedures begin with the on-line customer application, which is filled out, encrypted, and sent to the bank. The information is verified by a credit-checking service. No credit report is run, but the file is checked to ensure that the information provided (Social Security number name and address) is consistent with the material on file. This step ensures that the applicant is serious -- not just someone playing with the site by entering false information.
For the same reason, a physical copy of the application and a signature card (required by law) must be mailed to the bank. An account-creation package with the user name and the account password is mailed to the customer to confirm the postal address. (This package may eventually include a personal authentication device such as a smartcard or a floppy disk holding an encrypted private key, and a certificate of authentication associating the customer with it.) The account is then set up.
Customers communicate with the bank via a World Wide Web browser. Every transaction sent to the bank from within the bank's Web site is automatically encrypted. The bank server receives the transaction, decrypts the message and undertakes the service requested. The only requirement is that the customer's browser must support the Secure Sockets Layer (SSL) protocol, the security standard for most browsers and on-line services.
The bank server utilizes a "trusted" operating system derived from Security First Technologies' CMW+ compartmentalized-mode workstation, a multi-level military-grade security system modified for commercial use (it is now owned by Hewlett-Packard Co. and marketed under the trade name VirtualVault). SFNB is the first non-governmental application of trusted-operating-system technology. VirtualVault provides a hierarchy of authorizations and privileges that protect the system's functions from outside interference.
The administrator of a traditional Unix system would use an account called root, which grants access to all areas of the system. By contrast, a trusted operating system replaces the root account with a privilege mechanism, which uses explicit rules for granting privileges to specific processes. The privilege mechanism limits users' actions to the commands each has been authorized to use. Unrecognized users or unfamiliar applications are denied privileges and cannot gain access.
An information-separation mechanism in the trusted operating system creates a wall between the network environment and internal bank applications The network receives and validates the user's requests. A trusted forwarding application then routes them to the internal bank environment where they are processed and passed back [Fig. 3]
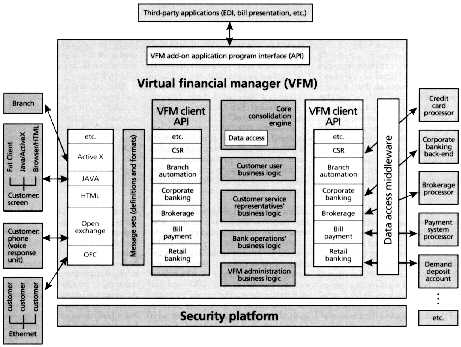
[3] A "trusted" operating system creates a wall between the network environment and internal bank applications. A "trusted" forwarding application routes communications to the internal bank environment.
Because of this separation, nothing in the outside environment can touch banking functions, and no outside process can disrupt the bank's internal operations. This feature protects it against any security breach accidental or malicious, occurring in the Web server.
The final safeguard of the system, providing accountability for all internal procedures and attempted break-ins, is its audit mechanism, which records suspicious activity, including the use of privileges, access violations logins, logouts, and unsuccessful network connections.
Further protection from intruders is provided by a system of firewalls and filtering routers, each presenting an additional barrier between the Internet and the internal bank network. To check the source and destination addresses on each network packet and determine whether to let it through, filtering routers are connected to both the outside Internet and to an organization's internal network, or intranet. Each address is checked against an internal database for authenticity; for example, to prevent outside users from masquerading as internal sources, the filtering router eliminates any outside packet with an inside source address.
Firewalls work in a similar way, examining each packet of information sent across the Internet to the customer service network. Using proxy software, they provide single-point-of-access controls and auditing facilities, serving as a barrier between internal and external computers. If an outside host wants to access an internal computer, the host communicates with the firewall and the firewall communicates with the internal computer thus protecting inside addresses from outside access.
For retail commerce, Security First Technologies chose the SSL protocol, which uses encryption to provide a secure channel for the data flowing between the browser and the bank server. The protection provided by SSL ensures the confidentiality of financial and personal data.
Most security breaches involve a password violation. For this reason, Internet banking customers are prompted to periodically change their passwords. If an unauthorized user does manage to obtain someone's password and break into that account potential damage is limited by the audit trail. Only very foolish thieves would send electronic payments to themselves. Also, the time and expense required to break into an account far exceeds the potential benefit.
Several kinds of attacks could be mounted against a network bank. An intruder might try to break into the bank application by pretending to be an administrator or a customer service representative -- in other words by attempting to send data packets that appear to come from an inside machine. This type of attack -- network address spoofing -- would be foiled by the filtering router, which drops outside packets with an inside source address.
User identity spoofing is another possibility. All customer identities and passwords reside in a database on the bank server, so no one can pretend to be a bank customer; inaccurate passwords or unrecognized identities are denied access. Because the password is sent encrypted by SSL, transactions are safe as long as customers ensure the secrecy of their own passwords.
An attacker might also try to break into the bank's database and alter or add customer passwords. But an outside attacker will not have access to those databases because they are stored in the internal environment, protected by the trusted operating system's separation mechanism. Furthermore, access to these databases is limited by the trusted operating system's privilege mechanism.
Finally, a common attack against network platforms involves replacing network services with Trojan Horses -- software that may subvert the machine on which the service runs. A trusted operating system minimizes the amount of damage such a rogue program can cause. First, the filtering router eliminates all but SSL-protected HTTP traffic. The HTTP server also examines each information packet before calling the trusted forwarding application to send the request to the bank. Any packet containing HTML code that could be used to run malicious programs is eliminated during these steps. Finally, all processes run with the minimum set of privileges necessary, greatly limiting the extent of any possible breach. The firewall limits traffic to customer service machines to e-mail only, reducing the chance that an unauthorized program could be introduced to the system by that route.
Although the possibility of external attacks causes the most talk, a bank is more at risk from an attack by an employee or someone with access to the internal server. To secure against this, Security First Network Bank uses HannaH, trade name for a network security product developed by Security First Technologies.
HannaH, developed as a tool to help corporate users create their own private networks across the Internet, provides strong authentication, permitting users to identify the server machine or PC being accessed Access control can be configured to restrict access to or from hosts, subnets, network services, and users. The system immediately detects any attempt to insert, modify, or destroy network traffic and provides a detailed audit, so that attacks can be traced as they occur.
All transactions are documented by the trusted operating system. Customer service PCs also run a special virus protection program, Troy, so that no unauthorized software can be added to a machine and no code can be introduced through the floppy drive.
An Internet bank insured by the Federal Deposit Insurance Corp. (FDIC) is subject to the same Federal regulations as other kinds of banking institution. Federal auditors visit regularly to verify the physical security of the site and assess the administration, data management, and programming. Internal process regulations have needed few adjustments for Internet-based banks. One of the few new rules requires every link from the banks Web site to any other address on the Web to be verified to prevent inappropriate links or implied relationships not meeting regulatory standards.
Some regulations may need to be changed for Internet banks. Reg E for example, stipulates that in every electronic transaction, the customer must be able to receive a receipt -- as at an ATM -- and that each transaction must be verified by a written statement in 30 days. In an Internet bank, the account register, updated with account activity, is the statement. A statement mailed once a month not only costs the bank more than it does to maintain the account but is outdated when it arrives.
Another regulatory requirement is the Community Reinvestment Act, which requires banking institutions to participate in and support the communities they serve. For Internet banks the problem is not compliance but the definition of "community" Since an Internet bank may have customers in all 50 states through its virtual branch, enforcing of the Community Reinvestment Act presents a puzzle for regulators.
The final regulatory issue concerns the entire banking industry. The growing number of non-bank financial service providers, such as credit card companies, e-pay systems, and smartcard vendors, are free of Federal bank regulations. Rules for banks should be reviewed to keep up with changes in financial technology. Where technologies can become obsolete in 18 months, and where at least two years are needed to implement new regulations, problems may arise if strong measures are not adopted soon.
Currently, average modem speeds top off at 28.8 kb/s, which can make Internet access discouragingly slow. Integrated services digital network (ISDN) lines can soon bring Internet access to homes at rates of 64-128 kb/s. Other technologies such as asymmetric digital subscriber line and cable modems will soon offer speeds at 500 kb/s and higher.
In parallel development are Web browser "appliances" already being introduced to market. Fast dial-tone browsers will eventually make the Internet as readily available as the dial tone of a telephone. These browsers are entering gear like TV sets and phones, and they serve as vehicles for paging, sending e-mail, placing phone calls, and so on. This is not an incremental change for the banking or other industries The Internet will fundamentally change how we do business. Soon, surfing the Web will be as simple as channel surfing on television. When Joe Couch Potato can do his banking during the football game's commercials, electronic commerce will have reached critical mass. That day is right around the corner.
Note: Virtual Financial Manager and Troy are registered trademarks of security First Technologies.
____________________
About the author
Michael C. McChesney is chief executive officer of Security First Network Bank's wholly owned subsidiary, Security First Technologies, Atlanta, Ga. (formerly Five Paces Inc. and SecureWare Inc., which he co-founded in 1994 and 1986, respectively). Previously, he was a senior associate at Investments Orange Nassau, Boston, responsible for venture capital investments for the $50 million fund.
Today, over two million people in the world pay most of their bills from their checking accounts, but without writing paper checks. Instead, they sit down at their computers, enter a series of bill payment transactions to be conducted, and dial a local number to transmit their instructions to one of a number of service providers, the largest of which is CheckFree Corp., Atlanta, Ga. Then on the date the bill is due, their account is debited and the indicated funds are electronically transferred to the payee's bank account. If the payee's account is not set up to accept electronic transfers (a birthday check for a nephew, for example), a paper check is automatically issued and mailed by the service provider.
With the development of a new electronic payment network, banks in the 1970s began offering a number of electronic funds transfer services. Some of the banks concentrated on providing corporations with the ability to debit the bank accounts of agreeable customers through the Federal Reserve's Automated Clearing House (ACH) system, the U.S. national organization that in 1978 permitted a bank to electronically exchange transaction information (such as the writing of a check) with any other bank in the United States.
For example, a consumer could request that regularly occurring fees -- like a newspaper subscription or club dues -- be deducted automatically from a checking account and paid. Before that, the only way to send money electronically from one person to another was through a wire transfer: banks using the Federal Reserve's Wire Network to settle accounts with each other could also use it to send money between individuals, typically charging over $10 per transaction.
Other banks began to allow their customers to pay bills through a standard telephone, typically for a limited list of recipients.
The first bank-independent bill payment system originated in 1981, when CheckFree was set up to help health clubs automatically collect monthly dues from their members' checking accounts. The company used the ACH system and received fees from the health clubs.
Over the next few years, CheckFree expanded into numerous industries, including the on-line service industry.
In 1986, CheckFree began developing a system for customers to pay all, not just a select few, of their bills electronically by keying instructions into their personal computers. The system was released in 1988. Soon after, designers of personal financial manager products, such as Quicken and Managing Your Money, integrated on-line bill payment into their software.
The past few years have seen a flurry of activity in the technology of automatic bill payment. In 1995 Visa Interactive, Herndon, Va., a wholly owned subsidiary of Visa International, announced its remote Windows-based banking software, which enabled financial institutions to offer bill payment and banking services to customers with checking accounts. The PC program can pay bills as instructed by the customer, track and reconcile account activities, transfer funds between a customer's accounts, allow customers to verify account balances on-line, and exchange data with other personal-finance programs that the customer may have on his computer, like Quicken and Managing Your Money.
In March 1996, Microsoft Corp. announced the Open Financial Connectivity (OFC) specification. This allows banks and third-party processors, such as CheckFree and Visa, to build direct connections to Microsoft Money, another personal-finance program, for bill payment, account transfers, and checking balances through the computer. This is an open specification, in that any bill-paying service provider can use it to make its system compatible with Microsoft Money.
Microsoft's latest release of Money (Money '97) gives banks the option to connect directly to customers through the OFC specification using either the Internet or a dial-up phone connection. Money implements the specification through standard Internet protocols (HTTP or TCP/IP) and standard Internet security protocols to connect to the bank's or a third party's (like CheckFree's) server.
In September 1996, Intuit Inc., Menlo Park, Calif., the company that developed Quicken, said it would develop Open-Exchange, another open interface standard. Open-Exchange builds on Internet protocols and industry standards to enable the exchange of financial data and transaction instructions between consumers, businesses, financial advisors and institutions, and government organizations.
In a typical bill-paying transaction with CheckFree [see diagram], a user at a PC keys in information concerning the payee -- such as name and address, billing account number, and other items. A fixed, recurring payment, like a mortgage, can be paid automatically each month. If the payment or date varies, the user must key in the amount and date each time.
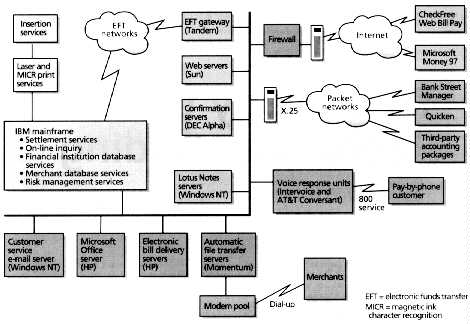
Depending on the method of access to CheckFree's on-line payment system -- which may be over the Internet, a packet network, or an electronic funds transfer network -- information is received and routed to the appropriate server, processed, and confirmation routed back through the same channel to the user.
After entering the payment due date and amount, the user clicks to transmit instructions through a local telephone number to CheckFree's server. Digital Equipment Alpha computers at CheckFree verify the user's identity, check the instructions to ensure that they are correct (for example, that a user is not trying to pre-date a bill payment by changing the system clock on his PC), and then return a confirmation number that can serve as proof, like a canceled check, that the transaction took place.
Some customers, sponsored by financial institutions, must have enough funds in their account to cover the bills, preventing overdrafts. For these customers, a Tandem computer [again, see diagram] communicates with the customer's bank over a private line or national or regional automatic teller machine network -- these instructions are not transmitted over the less-secure Internet. The bill payment information (the payer, payee, amount, and date) is then transferred to CheckFree's mainframe computers for processing. Payments are processed through major electronic funds transfer networks, such as MasterCard's Remittance Processing System (RPS) and the ACH System. Payments also can be sent through direct electronic data interchange (EDI) connections to a merchants' account.
The next significant technology hurdle in this form of electronic commerce is bill presentment. The delivery of a bill -- simply the amount owed, date due, and detail billing information -- by electronic mail has been in a pilot at CheckFree for over a year. Full presentation of bills, complete with graphics so they resemble paper copies of bills sent across the Web using hypertext transfer protocol, is currently being tested. Eventually, the consumer will be able to click on a button to say "Pay on the due date." This arrangement allows customers to review bills and authorize payment electronically, and automatically have a record of all bills received and payments made.
-- Mark A. Johnson & Howard Baulch
___________________
Mark A. Johnson is president of the Business Services Division of CheckFree Corp., Atlanta, Ga. Howard Baulch is executive vice president of systems and software development for CheckFree in Columbus, Ohio.
An abundance of information on Internet banking is available on the Web. For information about the companies involved, see: Security First Network Bank (www.sfnb.com), Security First Technologies (www.s-1.com), the Integrion Financial Network (homepages.ihug.co.nz/~crump/Integrion/), CheckFree Payment Services (www.checkfree.com/newcons. html), and Peachtree Software (www.peachtree.com/echeck.html).
A newsletter, Cyberbanking, deals with banking on the Internet and reports how early-adopting banks are utilizing the Net to improve service to their customers. The bimonthly is published by Bill Orr, 2070 Gregg Hill Rd., Waterbury Center, VT 05677; e-mail, orrbc@sover.net. An annual subscription is US $125.
For more details on the security and cryptography involved, see Netscape Data Security (www.netscape.com/newsref/ref/netscape-security.html), Cryptography FAQ (www.rsa.com/rsalabs/faq/index.html), The SSL Protocol (home.netscape.com/info/security-doc.html), and RSA's Frequently Asked Questions (www.rsa.com/rsalabs/faq/faq_misc.html#misc.9).
For general information about electronic bill payment, see "Electronic Bill Payment: Facts And Fiction," Vol. 1, Feb. 28, 1996 (www.ramresearch.com/crdflash/cf2_28h.html), and Electronic Bill Payments, Bill Payment Council Activities, Aug. 7, 1996 (www.nacha.org).
Steven M. H. Wallman
U.S. Securities and Exchange Commission
The Internet and other communications technologies are changing the way financial markets operate
Innovative technology holds great promise for the financial markets, where it makes lighter work of raising capital. With new means of communications and new uses for existing technologies such as the Internet companies can disseminate information about stock offerings more efficiently, easily, cheaply, quickly, and with greater interactivity than ever before. Several companies have already conducted offerings entirely over the Internet. Many other issuers use advanced communications to help investors receive information.
Improvements in technology are also fostering novel approaches to trading securities in the secondary markets. Technology can lower the cost of transactions and increase the liquidity of previously thinly traded stocks. It can provide greater transparency in pricing and reduce error rates. Some companies have recently set up Internet sites where interest in acquiring shares from existing shareholders may be expressed by potential investors without recourse to traditional markets. Perhaps more importantly, technology permits qualitatively different types of trading structures to emerge.
Since all these developments can improve the way capital markets work, they are good news for investors issuers and the economy. They also change the way these markets work, affecting the activities of customers, brokers, regulators, and even those persons intent on committing fraud. In the future, more changes will occur if technology fosters integration of the diverse U.S. marketplaces into a truly national market system -- a possibility foreseen 20 years ago, in amendments to the Securities Exchange Act of 1934. Eventually, an international market system will evolve.
Trading starts with an investor's decision to take part in a transaction -- a determination based on information in the marketplace, the official filings of issuers the advice of brokers and so forth. Advances in communications technology have obviously facilitated this process. Eventually, paper disclosure documents will largely be supplanted by electronic versions, since they enable issuers to reach possible investors at a lower marginal cost and with interactive and better disclosure.
Technology has also smoothed the primary offering process, in which securities are offered to investors directly by an issuer or through an underwriter. The Internet, for example allows issuers to distribute the required information directly to possible investors at less time and cost than paper delivery requires. In October 1995, the U.S. Securities and Exchange Commission (SEC) issued a release discussing the issues raised by the Internet and other technologies in this context; few difficult technical or regulatory concerns were presented.
How customer orders are executed in todays secondary markets depends on many factors, such as the type of order and the market where it is sent for execution. Despite many permutations there are basically just market orders and limit orders. By entering a market order, the customer expresses an intent to buy (or sell) the security at the prevailing market price. A limit order is a notice of intent to buy (or sell) at a specified price for a specified time.
By and large, limit orders are executed whenever the market price reaches the limit order price. For example, if a customer places a one-day limit order to purchase stock at $49, and the stock currently trades at an asking price of $50, the order will remain unexecuted unless someone is willing to sell the stock for $49. If the order is not executed on that day, it expires.
Technological advances offer the possibility of a new type of order, which might be called a dynamic order. This would be similar to traditional contingent orders -- orders that have parameters, conditions, or constraints that determine whether a transaction will occur and at what price. But they would be dynamic in that the conditions for a series of orders would have to be satisfied simultaneously. For example, an investor might enter into a system a "dynamic" order to sell 1000 shares of a stock within a certain price range, but only if at the same time another order to buy 1000 shares of a different stock occurs at a price no greater than a set price, and provided moreover that a certain market index stays within a specified range.
With available computing power many orders like this can be entered into a system that would proceed through a series of algorithms and iterations to determine if an order can be matched with others. If it could, all the matchable orders would be executed. This type of order would allow portfolio managers and others to engage in sophisticated trading strategies, to hedge risk exposure on a portfolio-wide basis, and to take into account co-variances among stocks or other assets and ensure appropriate portfolio-wide management. Systems of this sort may soon be in operation.
Currently, an order can be executed in many different marketplaces. A customer can designate an order-execution method either by instructing the broker how to execute the trade or by directly inputting orders in certain proprietary trading systems. In the absence of instructions from the customer -- the norm for retail accounts -- the executing broker may determine where and how to execute the order by using algorithms or simply checking for the best price in selected marketplaces.
In the United States and many other countries, one traditional kind of marketplace for securities has been an exchange. A traditional exchange has members, detailed trading rules and listing requirements for stocks traded on it. Besides the primary U.S. stock exchanges (the New York Stock Exchange [NYSE] and the American Stock Exchange [AMEX], also in New York City) there are five regional stock exchanges in the United States: the Boston, Chicago, Cincinnati, Pacific, and Philadelphia exchanges. Also, there are exchanges for trading other investment instruments, such as options, as well as many exchanges elsewhere in the world.
Exchanges differ significantly. When an order is routed to the NYSE, for example, it is transmitted electronically or physically delivered to the "specialist post" where that stock is traded. Each stock traded on the exchange has one "specialist" (In theory there could be more.) The specialist firm ensures an orderly market for that security and executes all orders received in that stock.
For stocks trading at prices above $1, the specialist reports the current price quote for that security in increments of an eighth of a dollar (12.5 cents). The price quote ultimately determined by supply and demand, generally consists of the number of shares ordered, the highest bid price (the price at which someone is willing to buy the stock), and the lowest ask price (the price at which someone is willing to sell it). Assuming a quote of "1000 XYZ at $50 1/8 bid and 2000 at $50 3/8 offered," the specialist stands ready to execute an order of as many as 1000 shares of the stock from anyone who wants to sell for 50 1/8 and an order of up to 2000 shares of the stock to anyone who wants to buy for 50 3/8.
The difference between these two prices is termed the spread (which typically ranges from one-eighth to one-half of a dollar -- generally, the more liquid the market for the stock and the lower its price, the smaller the spread). The specialist must ensure that trades are executed at prices no worse than the best quote. Transactions may be crossed between them if orders to buy and sell between the quotes arrive reasonably contemporaneously "on the floor." (For instance, if someone is willing to sell 1000 shares for 50 1/4, and someone else is willing to buy 1000 shares for 50 1/4, a trade would be executed at 50 1/4.)
On the NYSE, part of the trading process has been automated. Certain small orders can be transmitted electronically over data communication lines from a member firm's trading desk (located anywhere in the world) to the NYSE SuperDot system which routes them directly to the specialists display book. Only odd-lot orders (orders smaller than 100 shares) are executed automatically by the system [Fig 1, left].
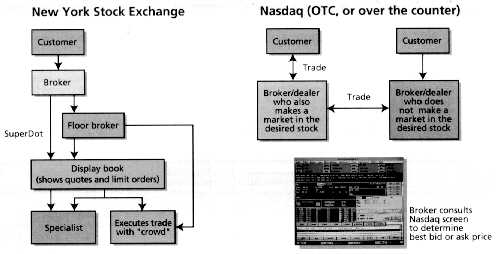
[1] At the New York Stock Exchange [left], a customer gives an order to a broker, who sends it directly to the specialist's display book via the SuperDot system (where it is executed if the market price matches the order's terms) or phones it to the firm's floor broker. That broker can either execute the trade with another floor broker who has an offsetting order or hand the order to the specialist. The specialist executes it if it matches the market price, or enters it on the display book for execution later when the market price is right. At Nasdaq [right], a broker-dealer who is a market maker for a stock can execute a trade against its own inventory or else execute a trade with other market makers.
Securities not listed on an exchange are traded in the over-the-counter (OTC) market, which has no physical trading center instead consisting of the network of broker-dealers willing to "make a market" in OTC securities. These "market makers" publish quotes, generally in eighths, for specific securities and stand ready to buy and sell them for their firm's own account with customers or other broker-dealers. Each market maker sets its own quotes. The "best bid and offer" price represents the highest amount any market maker is willing to pay for a stock and the lowest amount at which any market maker (whether the same firm or a different one) is willing to sell. Usually, the more heavily a stock is traded, the more market makers there will be.
Long ago, brokers had to call market makers to obtain their quotes, but in 1971, Nasdaq changed this process for many OTC stocks. Nasdaq is an electronic network that displays the quotes at which market makers are willing to trade [Fig. 1, right]. It does not automate the trading process or execute trades, except for small retail orders executed automatically at the best price through the Small Order Execution System. Generally, trades must still be negotiated by phone, although in some cases they may be negotiated electronically through the SelectNet system of the National Association of Securities Dealers Inc. (NASD), Washington, D.C. .
Besides exchanges and the OTC market there have traditionally been two more broad categories of markets. One consists of OTC market makers that make markets in exchange-listed securities. The other is now substantial, consisting of directly negotiated customer-to-customer trades, typically between institutions.
Thanks to technology, trading can be facilitated by electronic proprietary trading systems operated by registered broker-dealers. Currently, there are two types matching services and crossing services [Fig. 2].
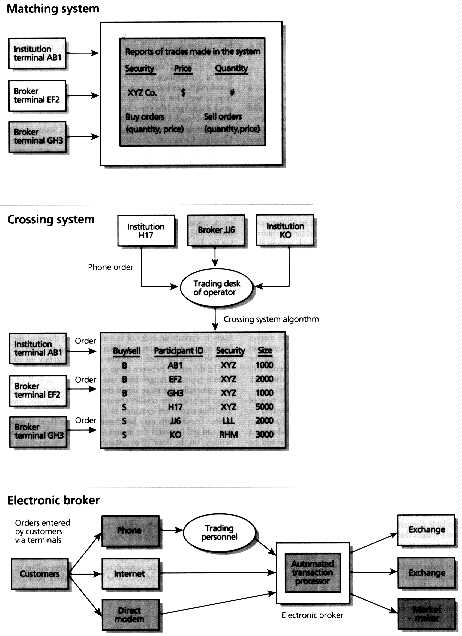
[2] In a matching system [top], customers enter orders on terminals for anonymous display to others. Some systems match offsetting orders automatically: in others, would-be buyers "hit" orders displayed on the screen, then execute a trade with the displayer.
In a crossing system [center], unpriced or priced orders (depending on the system) are entered by customers on terminals or by phone at the operator's trading desk. At a given time, the system algorithm crosses unpriced orders at a price determined from another market -- the midpoint of the bid/ask spread on an exchange -- or by performing a "call auction" if the orders are priced.
At an electronic brokerage [bottom}. customers route orders and receive confirmation through an Internet connection, for instance. Their broker then routes the orders to an exchange or market maker to be executed.
Matching service systems like Instinet are designed to allow participants to use an electronic communications network to enter orders for stocks listed on an exchange or in the OTC market. Most systems display orders anonymously; participants can view orders but do not know who entered them. Orders are firm so that when another participant enters an executable contra order, a trade occurs and the participants are bound by it.
Generally, a participant can also execute a trade by "hitting" a bid or offer displayed on screen. Some services let participants post indications of interest, as opposed to firm orders, so that they can use the system to negotiate a transaction directly. New rules, put into effect by the SEC at the start of 1997, are meant to ensure that participants in public markets who do not subscribe to a private matching service will in many cases, know the best bid/ask entered into the private system.
Crossing service systems generally "cross" customer orders at a single price determined by the system. Those prices can be established by derivation from the prevailing price for the security in other markets through a procedure termed a call auction, or otherwise. One example of the first type of system, Posit, automatically crosses all executable orders, usually at the midpoint of the public bid ask price for the security, at predetermined occasions (several times daily, either while the markets are open, or after hours).
The second type of system crosses executable orders at a so-called auction price the single price at which the greatest number of buy and sell orders can be executed at a price equal to or better than the limit price entered by each participant. (This price for buyers would be a price equal to or lower than their limit order while for sellers it would be equal to or higher than their limit order.) Once that price has been determined, all eligible orders are executed at the auction price. Participants can view limit orders posted on the system and add or delete them as the cutoff time for the call auction approaches. The Arizona Stock Exchange (run by AZX Inc, Phoenix) is a single-price call auction system.
In addition, registered broker-dealers, primarily discount brokerages, allow customers to route orders electronically, rather than having to call or visit a live broker. While this is a beneficial development for investors, lowering costs and providing realtime information and other benefits, it does not materially change the way these trades are executed. Essentially, such systems merely make entry to the trading mechanism more efficient. The electronic brokerage determines where to route the orders [Fig. 2, bottom].
If a trade occurs, the specialist or executing broker-dealer reports the trade information to be displayed on the "consolidated tape," designed to report publicly trades in securities listed on the exchanges and on Nasdaq, even if the trade occurred in a matching or crossing system. Once a trade is executed, it must clear and settle. Clearance involves confirming the security, the number of shares, their price, the time and the buyer and the seller in a transaction. Settlement is the fulfillment, by each party, of the obligations of the trade.
A clearinghouse compares records of the trade to ensure that all its aspects (price quantity, buyer, and seller) agree, determining the net amount of securities and cash due from its participating broker-dealers. Next, the settlement process ensures that the trade is paid for, frequently by the wire transfer of funds. Finally, the process ensures that stock ownership records reflect the name of the new owner.
Technology should change the clearance and settlement process. In 1995, the standard settlement time was reduced from five business days (trade+5, or T+5) to three business days (T+3). Eventually technology should allow for same-day (T+0), and even real-time settlement, which will improve the stability of the markets and the economy by further removing the risk of default on trades. In addition at T+0, the risk of counterparty failure should be limited, which would reduce the level of capital needed to operate in the markets.
If investors do not insist on negotiable paper stock certificates, all transfers of ownership can be reflected with a simple change to a depository's computer records, thereby facilitating the shift to T+0. Improved fund transfer technology, electronic banking and "electronic cash" could make payment almost instantaneous. Moreover, even now investors can use credit or debit cards to purchase many securities and credit card companies or their successors may become more heavily involved in the securities guarantee function in the future.
The U.S. stock trading system is quite complex [Fig. 3, left], with vast numbers of market players and many marketplaces. All of them must carry out their assigned tasks involving millions of transactions a week.
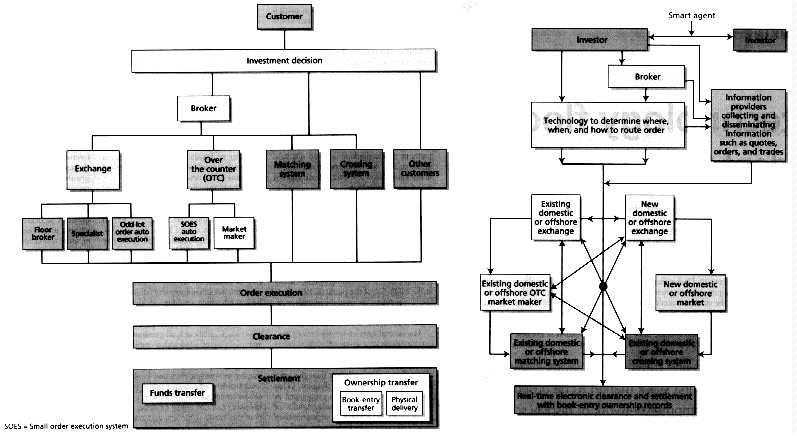
[3] In today's U.S. equity market system [right], trades can be made in a number of marketplaces, including an exchange and a matching system. After a trade has been executed, it must clear and settle -- the phrase for the three-day-long transfer of funds and ownership.
The equity market of the future [far right] may be ruled by investor-to-investor trading (no intermediaries) and may embrace investor-to-investor smart agent technology and multiple competing marketplaces offering a variety of functions. Technology will interconnect all the players and enable each to execute orders differently, while orders will be settled in real time.
Many components of the U.S. market structure have been in place since the early 20th century. The Securities Exchange Act of 1934 (the Exchange Act) regulates markets, brokers, and dealers and generally requires companies whose stocks are traded on an exchange or on Nasdaq, as well as other companies if they satisfy certain conditions, to provide periodic disclosure. The act established a system for regulating market participants that in part reflects the nature of the securities markets in the 1930s.
In the '60s and '70s, amendments to the Exchange Act modernized the securities laws and provided a blueprint for a national market system for traded securities. More than 20 years ago, the U.S. Congress stated that "new data processing and communications techniques create the opportunity for more efficient and effective market operations" and called for electronically linking together various marketplaces for securities trading Some progress has been made toward that goal, but more work remains to be done. Many other countries have replicated elements of the U.S. regulatory scheme, and as stock transactions are becoming increasingly globalized, these issues have worldwide impact.
At the Federal level the United States currently regulates the securities markets through a partnership between government and industry. Although the SEC oversees the markets, it does so in part through a system of "self-regulation" that grants the exchanges and the NASD responsibility for regulating their members and trading practices. Now that technology has opened up more opportunities for investors to deal with each other directly, without much mediation by a broker-dealer, more and deeper thought must be given to the current regulatory scheme.
If trading moves away from so-called fully intermediated markets, the SEC will have less ability to leverage scarce governmental resources with those of the self-regulating organizations. If transactions can occur without a broker or organized exchange as an intermediary, the SEC loses some of its eyes and ears and private sector compliance staff.
The United States also must think about how it will oversee the regulated players in its markets. For one thing, the Exchange Act contains a broad definition of "exchange," although the SEC has interpreted the term more narrowly. Many other market centers have developed over time but are not regulated as exchanges. Specifically, Nasdaq is not regulated as an exchange but is subject, by statute, to many of the same types of requirements. Most proprietary trading systems are regulated under the broker-dealer regulations. The only call auction exchange in existence, the AZX, is exempt from most requirements of the Exchange Act by virtue of AZX's classification as a "limited-volume" exchange.
As technology progresses, the line between alternative markets and traditional exchanges will continue to blur. Moreover, technology has created linkages between domestic and offshore markets, thereby raising the issue of what regulations apply if those offshore facilities become easily accessible to U.S. investors.
Since no end is in sight to the emergence of novel types of markets, the country should ask why various markets should be regulated so differently under U.S. laws. The eventual solution will be to move to goal-oriented, flexible regulations that make sense in a world of rapid technological change. Goal-oriented regulation would focus on the functions performed by the market center and regulate with respect to those functions, not the entire center itself.
Consequently, a market center that engaged in some but not all activities of an exchange would be regulated with respect to those activities, rather than (as at present) being subject either to all or to none of the regulations applicable to an exchange, depending on how the market center was defined. For example, market centers that only discovered prices might be subject to surveillance, audit trail, and public reporting requirements, but not to governance or capital requirements.
Regulators also must ensure that innovations do not create greater potential for fraud or systemic risk. Clearly, technology makes possible more complex frauds or circumvention of rules. There is also great concern about computer failures and system-wide failures.
Technology's continued revolution of the securities trading process should, of course, be encouraged. Ultimately, technology will turn U.S. markets into a reflection (although a rather updated one) of the "national market system" that was envisioned by Congress in 1975.
For that process to be complete, a number of things will have to happen. All market participants and market centers will need to be interconnected or accessible; that is, any participant in one market should be able to see and access the orders and quotes of any other participant, who could be anonymous, in another. Markets will eliminate artificial constraints on price competition. Finally, marketwide time priority, as well as any other factors participants like to add through algorithms they select, could help promote the competition.
Some of today's market intermediaries will survive, although they may have to adapt their operations. For example, intermediaries will still provide the valuable role of ensuring "immediacy" for investors who seek it when an investor wants to sell a company's stock, an intermediary frequently buys it because a purchaser may not be available at that time. At some point, there will be enough liquidity from buyers and sellers, or enough investors who will not want immediacy, to eliminate the need for this intermediary function for some stocks. But someone would still have to ensure that trades clear and settle, that the books are kept, and that the issuer of the stock is told who now owns it.
Existing technology holds hope of another development that would benefit investors by improving prices: decimalization. Generally, U.S. markets have traded in minimum increments of an eighth of a dollar, which makes it harder for investors to obtain better prices, because, for many stocks, eighths are likely to be too large. With a more flexible pricing structure, market makers or specialists could reduce the quoted spread more easily, and investors placing limit orders would be better able to compete. It now costs 12.5 cents to place a better limit order; decimalization would allow investors to do this in finer increments.
Decimalization is inevitable. Although technology is obviously not a necessary condition for decimalization, it does make decimalization more likely to occur sooner by permitting more market centers -- including those based outside the United States that trade in finer increments like decimals -- to compete more easily with those in the United States, thereby placing pressure on U.S. markets to be more competitive.
As U.S. market centers become more interconnected through technology with each other and with global markets the market system will begin to accommodate such demands as around-the-clock trading and may eventually provide for price-time priority across markets.
The market innovations generated by technology to date have been positive because they made markets better suited to their users. Different classes of investors have different needs, and any one investor may have different needs at different times and for different orders.
Some observers have predicted the rise of a consolidated marketplace described as a black box into which all trades will be sent for execution -- a single market that will dispose of all trades without market fragmentation and with increased customer-to-customer trading. To date, technology has not led to a consolidation of markets. In fact, new specialized marketplaces have come into being. Moreover, a black box structure, operating under one set of procedures, may not be best for all stocks or all customers. More probably the market of the future will comprise a global collection of diverse, interconnected marketplaces that permit investors to choose the one that makes the most sense for their needs. Technology also will permit more investor-to-investor trading, without intermediaries
Specifically, new technologies such as "smart agents" will expand the choice of trading methods that require little intermediation. For example, using smart agents -- programs designed to act as agents of their principals -- a market participant could enter an order to purchase at a specified price that could change over time according to an algorithm selected by the participant Sellers could enter similar contra side orders with their smart agents. The smart agents would then seek each other out over the Internet by "visiting" selected Web sites or else through search engine techniques.
When smart agents encounter contra-side agents dealing in the same security (or securities that the principal might say are sufficient substitutes, such as any automobile stock if the principal wants to change its exposure to the auto sector), they would negotiate with each other according to their own algorithms If a "deal" can be struck, the agents will report back to their principals that a transaction has occurred, and at the same time automatically notify the transfer agent of the stock and funds to be exchanged. With such technology, investors anywhere in the world could engage in transactions with little or no intermediation and very low marginal costs.
Potentially different types of markets could therefore encourage innovation through competition. Some markets will be full-service marketplaces; others will provide only certain services, and others will be ill-defined -- such as smart agents on the Internet. Technology will allow orders to be routed to the most appropriate market.
So the market of the future is likely to be a glass box of markets with different but transparent trading opportunities accessible through technology. The result will be seamless electronic trading, around the clock and around the world, with investors buying and selling individual stocks currencies commodities and mixed portfolios. Trades will be based on a variety of parameters. Liquidity will be provided primarily by investors, as opposed to intermediaries. Settlement will occur in real time. Multiple types of competing markets and market centers will provide multiple services. Transaction costs will fall to competitive levels on a worldwide basis [Fig. 3, right].
Technology will help us achieve this goal, but foresight and thoughtful proactive regulation are also necessary. Let us hope that, if the technical community keeps providing the former, the government will try hard to provide the latter.
______________________
About the author
Steven M.H. Wallman is a commissioner on the U.S. Securities and Exchange commission (SEC). Earlier, he was a partner in the Washington, D.C., law firm Covington & Burling. As a matter of policy, the SEC disclaims responsibility for private publications or statements by its members or employees.
Use of Electronic Media for Delivery Purposes, Securities Act Release No. 33-7233 (Oct. 6, 1995), offers interpretive guidance from the U.S. Securities and Exchange Commission (SEC) on how issuers can satisfy their disclosure-delivery obligations under the U.S. Federal securities laws when relying on electronic media. It also offers guidance to companies considering on-line offerings.
Development of a National Market System, Securities Exchange Act Release No. 34-14414 (Jan. 26, 1978), explains the SEC's initial ideas on ways to create a national market system.
Market 2000: An Examination of Current Equity Market Developments (January 1994), from the SEC's Division of Market Regulation, has excellent descriptions of the current U.S. market structure, proprietary trading systems, and regulatory issues. It also looks at possible future developments.
The U.S. Office of Technology Assessment's Electronic Bulls and Bears (1990) is a report to the U.S. Congress on automation, the use of technology in the U.S. securities markets, and regulatory issues. Valuable background information on how the markets operate is included. The report is available on a CD ROM, "OTA-Legacy," from the Superintendent of Documents, Box 371954, Pittsburgh, PA 15250 7974; 202-512-1800; fax, 202-512-2250; price, $23.
[Added by JYA: See on-line source for OTA publications:
Electronic Bulls and Bears: U.S. Securities Markets and Information Technology (September 1990)Trading Around the Clock: Global Securities Markets and Information Technology (July 1990) ]
Further information from the SEC can be found on the Web at www.sec.gov.
Alfred R. Berkeley III
The Nasdaq Stock Market Inc.
On-line trading technology evolves at the first stock market to be based on a network of display screens
Over the years electronics technology has revolutionized virtually every securities market, most notably The Nasdaq Stock Market Inc. Nasdaq, a trademarked name, was the world's first market to handle trading not on an exchange floor but through a computer network linking display screens. But since its advent in 1971, changes in telecommunications and computer technologies have been ongoing, profound, and complex.
As a screen-based market, Nasdaq (which originally stood for National Association of Securities Dealers' Automated Quotations) has striven to stay on top of those developments. It is in the process of completing a US $180 million systems migration program -- the largest single telecommunications and computer project undertaken by a U.S. stock market. The effort has involved replacing the entire Nasdaq system with a standards-based client-server network while moving from analog to digital network technology and upgrading the core systems to process 500 transactions a second -- a rate that enables the market to handle at least a billion shares a day. With these systems, Nasdaq has the flexibility to constantly improve operational efficiency and regulatory oversight
In light of Nasdaq's ongoing growth, that transaction capacity is critical. But in the long run the value of technology lies not in being able to do more work more quickly, but in the opportunity to innovate. Nasdaq's history is in itself an example of how technology can drive innovation. At its most basic level, screen-based trading eliminates physical limits on who can be in the market. Investors and brokers in New York City, London, Singapore, or anywhere else can have access to the same trading information at the same time. The result is a kind of democratization of markets because no one gains an advantage by being in a certain location.
This decentralized approach makes it possible to have multiple market makers -- the name for dealer firms that put their own capital behind a stock. At the traditional exchanges where buyers and sellers meet on a trading floor, each company's stock has a single specialist making a market in that stock. On Nasdaq, however, there are virtually no limits to the number of market makers. The average Nasdaq stock has 11 market makers, and some of the largest companies' stocks -- such as Microsoft or MCI -- may have more than 50 vying for investors' orders.
This competing network of dealers is a central strength of a screen-based market. Open competition is the key to efficient pricing and to ensuring that investors get the best possible price and execution for their orders. In addition, academic studies have shown that Nasdaq's multiple market-maker system increases liquidity (that is, the dollar volume of trading that can occur without affecting the price of a stock) With a number of dealers committing capital to a given security -- and thereby spreading any risk -- the market has the capacity to absorb large increases in volume without the need for trading halts.
The open, competitive nature of Nasdaq will be enhanced by its implementation of the new order-handling rules that the U.S. Securities and Exchange Commission (SEC) has set to take effect Jan. 20. Under these rules, market makers must display investors' limit orders in their quotes when the orders are priced better than the market makers quote. Also under the new SEC rules, market makers must display their most competitive quote publicly, not merely in a proprietary trading system. These rules make things better for investors. They give investors access to the best possible price and permit investors to have their interest in buying or selling shown to the entire world on some 300 000 Nasdaq terminals. Technology will be the key to the implementation of the new SEC rules, and Nasdaq is working with market participants to interface its systems and theirs so that this comprehensive quotation display can take place. Concurrently, Nasdaq is completing work on a proposed trading system called NAqcess that will automate the processes required by the SEC's rules.
Technology is not only an enabler of competition -- it is also an effective tool for ensuring that competition remains fair A screen-based market is really an open, electronic community. It tends to be very transparent -- anyone on the network can see precisely what is taking place, as it takes place.
This transparency is enhanced by an array of computer systems that monitor the market and act as powerful complements to on-site compliance visits. For example, a system called StockWatch Automated Tracking (SWAT) uses sophisticated statistical models to continuously compare real-time market activity with historical trading patterns. If the SWAT system spots any discrepancies in prices or volumes, it flags that information for market surveillance analysts. At the same time, the system pulls up relevant stories from the Associated Press and Reuters newswires to help analysts determine if the cause is something in the news.
A new generation of technology is also at work in the market regulation performed by Nasdaq's sister subsidiary, NASD Regulation. Now in operation, for instance, is a recently completed system called Research and Data Analysis Repository (Radar). When the SWAT system detects an unusual movement in a stock, Radar rapidly pinpoints which securities firms are responsible for that trading, the precise time of each trade, how much was bought or sold, and the account involved.
Nasdaq has taken advantage of the Web technology to launch an Internet site that offers an array of current market data and index tracking (www.nasdaq.com) to investors worldwide. Quotations for all Nasdaq stocks are offered on a 15-minute delay and a glossary of financial information explains market terminology and concepts. There are also hot links to the World Wide Web sites of some 2200 Nasdaq companies.
With its new technology, Nasdaq is in a position to develop new information-based products and services. The data routinely generated by trading activity can be analyzed to yield information targeted to the markets customers. For instance, Nasdaq can give companies on-line reports that compare their stocks with others like them or that track who is most active in their securities.
A key element of this new technology is Nasdaq Workstation II [see screen shot below]. Through it, brokerage firms may access Nasdaq quote and execution services, may merge Nasdaq data with feeds from in-house systems and outside vendors, or may rework that data with in-house software tools.
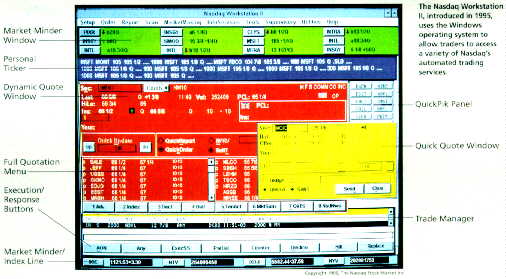
The Nasdaq Workstation II, introduced in 1995, uses the Windows operating system to allow traders to access a variety of Nasdaq's automated trading services.
Rapid growth of screen-based trading is expected to continue Therefore, in April 1996, the Nasdaq Board approved construction of a $33 million data center next door to its current facility in Trumbull, Conn. The center is intended to help increase Nasdaq system capacity from one billion shares a day to two billion.
Based on success of this order, we believe that Nasdaq's experience provides a model for how technology can be harnessed by securities markets. Indeed, in recent years, more and more markets around the world have moved to screen-based trading, and that trend continues. According to the Federation des Internationale des Bourses de Valeurs, Paris, of the 45 developed stock markets in the world only three still rely exclusively on a trading floor. The rest are either entirely screen-based (28), or employ screen-based trading to supplement floor transactions (14).
In the '80s, for instance, the London Stock Exchange converted to screen-based trading as part of the "Big Bang" securities industry reforms. Even before that event, the Exchange had designed SEAQ, an automated quotation system modeled after Nasdaq. On the Pacific Rim, the Stock Exchange of Singapore patterned an automated system, Sesdaq, after Nasdaq, and in Japan, Jasdaq was also developed using Nasdaq as a prototype.
When work began in the '90s on a pan-European stock market, Nasdaq was again adopted as a model because a decentralized, screen-based market would permit participation from any part of Europe. One initiative is Easdaq, the European Association of Securities Dealers' Automated Quotations system, which began operating in 1996. A second pan-European, screen-based market project, Euro.NM, is joining France's Nouveau Marche, already in operation, with what will be the New Market of the Brussels Stock Exchange and the Neuer Markt of the Deutsche Borse.
The move to free market economies in Central and Eastern Europe and the former Soviet Union has stimulated a great deal of capital market development there. Russia's nascent national electronic market was built with Nasdaq assistance and uses software licensed from Nasdaq. A similar initiative is under development in Ukraine. The Nasdaq model and software are also the foundation of Rasdaq, supporting Romania's privatization program.
The common element among these initiatives and others is the deployment of automated screen-based trading systems giving affordable access to market participants wherever they are located, eliminating the need for a trading floor and reducing transaction costs. Automation is used to bring all market participants together in a fair and orderly way without physically congregating in one place to shout for orders in an open outcry auction.
Note: StockWatch Automated Trading, Research and Data Analysis Repository, and Nasdaq Workstation II are registered service marks (SM) of The Nasdaq Stock Market Inc.
______________________
About the author
Alfred R Berkeley III has been president of The Nasdaq Stock Market Inc., Washington, D.C., since June 1996. For five years before that, he was managing director and senior banker of the corporate finance department of Alex. Brown & Sons Inc., Baltimore, Md., where his focus was large companies in computer software and electronic commerce. From 1989 to 1991, on leave from Alex. Brown, he was on the executive committee of Safeguard Scientifics Inc. and chairman of a number of its subsidiaries. Among earlier posts at Alex. Brown, he was head of information services, supervising the upgrade of computers, systems development, telecommunications, and video technology.
The Nasdaq Handbook, revised edition (printed by Probus Publishing, Chicago, 1992), contains articles by securities industry professionals, corporate executives, regulators, and academics on such topics as the structure, technology, companies, investment opportunities, and economic contributions of The Nasdaq Stock Market. The handbook may be purchased for $32.50 from NASD MediaSource, which may be contacted at 301-590-6142.
The Nasdaq Stock Market's Web site (www.nasdaq.com) supplies stock quotations and news-wire business information on a 15-minute delayed basis, as well as current stock index values and links to approximately 2000 Web sites of Nasdaq companies.
Mike ter Maat
American Bankers Association
Electronic cash may end government monopolies on the lucrative business of minting money
For all the hype over electronic cash one point is usually left out it may never come to pass. It all depends on the economics of e-cash, and that's a complicated mix of issues -- including whether producers can find an opportunity for profit, whether consumers will accept it as money, and whether governments will allow it to flourish. If all the stars don't line up, it could go the way of the geodesic dome -- just another big idea with few important applications.
Electronic cash includes electronically stored value designed for use either in a single transaction or in many. E-cash meant for repeated use is also called electronic currency. Currency and other kinds of e-cash convey value in and of themselves rather than merely representing value residing elsewhere, such as a deposit account. By contrast, electronic checks and debit cards do not store intrinsic value and thus are not considered e-cash, which can be used in transactions off-line and with no transfer of physical material.
The business of making money can be lucrative -- one reason national governments around the world have kept the action to themselves for most of this century. The world's largest issuer of currency is the U.S. Federal Reserve System (the "Fed"), which has more than US $400 billion in paper bills outstanding, two-thirds of it circulating outside the United States. When issuing new currency, the Fed trades it for interest-bearing U.S. Treasury securities. The resulting interest accruing to the Fed -- in effect, the "float" on outstanding dollar bills -- amounts to some $20 billion a year. The government saves this money in interest charges because it can print cash that it uses to buy back a part of the federal debt.
These earnings are the modern-day equivalent of what used to be called seignorage the sums monarchs of old would clear for minting coins. Seignorage is the difference between the selling price of currency -- its face value -- and the printing costs, which today are pretty small compared to the face value. One of the major incentives for banks and other private institutions to issue electronic cash would be the chance to earn seignorage by selling e-cash. E-cash would be sold to customers for old-fashioned paper dollars or something else of value, such as money transferred from a deposit account. It would then be used in transactions before being returned to the issuer, at which point it would be exchanged back into paper dollars or an account balance
Earnings for the issuer would come in the form of interest on investment of the money that would bc paid for e-cash. These interest earnings, accumulating while the e-cash remained outstanding, would be the issuers' incentive to produce and sell e-cash products so useful to the economy that they would remain in circulation for a long time before being redeemed. To turn a net profit, an issuer would have to keep in circulation enough e-cash to pay the costs of developing and managing the product. For a number of reasons, that's easier said than done.
First of all the development costs can be enormous. Firms like Mondex in the UK, DigiCash in the Netherlands, Danmont in Denmark, and MasterCard, Visa, and Citibank in the United States, have invested huge amounts developing electronic payment systems intended to act as cash substitutes.
Managing the product could also turn out to be expensive. Consider what would happen to seignorage earnings if currency issuers had to pay interest on their e-cash -- that's right, interest on cash. It will certainly be technically feasible in the future, and if there is competition among various issuers of e-cash, market forces may demand that interest be paid. Consumers would love to get it, but if it were payable at rates comparable to those of other investments, seignorage profits to issuers would be completely wiped out, and with it much of the incentive to develop e-cash systems.
A further incentive for e-cash producers, retailers, and others forming links in the transaction chain is the possibility of reducing the costs of processing transactions that now involve paper currency [Fig 1]. Because these costs would be so low one major use of e-cash -- the so-called killer application -- may be Internet transactions involving small amounts of money. Such small transactions have never been economically feasible with more expensive, paper-based systems. But in the future small purchases of information or entertainment (for instance, financial statistics, movie reviews, and photographs) may become commercially viable. Whole new industries could be spawned by coupling this new transaction capability to the Internet's new content-delivery system. Those with a stake in delivering this kind of content will have great incentives to develop and deploy e-cash systems.
[1] Electronic systems are cheaper to operate. The costs per transaction shown here include all those incurred by banks, retailers, and others forming the links in the transaction chain.
Perhaps the most compelling argument for e-cash is the potential for improved service. Banks compete hard for deposits by offering services that are typically more important than interest rates check processing, statement services, and ATM (automated teller machine) access, for example. Similarly, the customer of the future may expect stored-value cards and other products that use e-cash so the bank of the future may have to provide them whether or not these services can pay for themselves. This may sound far fetched, but it is a little-known fact that ATM services are provided by banks today at a significant loss.
Nonfinancial firms also have incentives to issue e-cash as a service to their retail customers. For example, telephone companies are issuing prepaid cards to assist consumers as they travel; convenience stores are offering prepaid cards to build customer loyalty; and transit authorities are issuing prepaid cards to help customers enter and exit their systems more expeditiously.
The examples of prepaid phone cards and convenience store cards represent the first stage of e-cash development two-party stored-value systems [Fig. 2, top]. Customers can use this type of product only to pay for services rendered or goods sold by the stored-value issuer itself. Because the only parties involved are the issuer and the customer, such products are viable only for issuers with something to sell at the retail level.
[2] E-cash may pass through several stages of development. Two-party stored-value systems [top] permit customers to pay only for services rendered or goods sold by the issuer itself. Three-party (closed-loop) stored-value systems [center] can be used by customers to pay not just the issuer but any participating retail vendor. Currency-like (three-or-more party, or open-loop) stored-value systems [bottom] would allow customers to pay not only participating retail venders but also anyone willing to accept e-cash as payment.
The next stage of e-cash development would involve three-party stored-value (or closed-loop) systems in which customers can pay for goods or services sold by retailers other than the issuer of the card [Fig. 2, center]. This makes e-cash practical for a broader range of issuers, including those with no retail goods or services to sell.
Widespread acceptance among retailers will be essential for the success of three-party stored-value products. Banks, with their strong merchant relationships and government regulation for safety and soundness, may be among the few kinds of firms capable of issuing such products commercially. While other major institutions may be able to offer these products, their customers would have to monitor the financial safety and soundness of the issuer in some way. A three-party stored-value system is to be tested jointly this year in New York City by Chase Manhattan, Citibank, MasterCard, and Visa. Transit authorities and universities that are attempting to broaden their existing two-party systems to include local vendors are also issuing such products.
As with two-party stored-value systems, the float would be earned in the interval between issuance of the e-cash and its return to the issuer. In this case, the stored value would be presented to the issuer by a retail vendor for legal-tender cash or credit to an account. And as with two-party stored value, too, this period is likely to be relatively brief, since the product could be used in only one retail transaction, which is why the system is referred to as "closed loop." The final stage of e-cash development will involve the creation of a currency-like system in which stored value circulates through several transactions. Such open-loop stored-value systems [Fig. 2, bottom], would allow customers to pay not only participating retail vendors but also individuals willing to accept the e-cash as payment. Because open-loop e-cash would not have to be returned to the issuer after just one transaction it would circulate for longer periods, boosting both the amount outstanding and its profitability.
The product would be designed without linkage to a bank account and could therefore be traded off-line among all individuals with the appropriate hardware. As compared with closed-loop three-party systems, open-loop ones would likely require issuers with even more household recognition and credibility. This requirement may effectively limit successful issuers to banks and perhaps certain other government-regulated organizations.
As in the case of closed-loop systems, the float would be earned from the time the stored value was issued until the point when the value was returned to the issuer either by individuals or retailers. In an open-loop system, this period is potentially indefinite and apt to be quite long in practice. Indeed, some people speculate that once such a system has been established and accepted, e-cash could even survive the financial failure of its issuer.
The leading developer of a currency-like stored-value product is the British firm Mondex International Ltd. London which grew out of a project at National Westminster Bank. Franchising participation rights throughout Europe and North America, Mondex has signed up several banks plus AT&T. The Dutch firm DigiCash BV, Amsterdam, and the U.S. firm CyberCash Inc., Reston, Va., are also developing stored-value products to act as cash substitutes, though their main focus has been Internet deployment. Mondex would also be card-based.
Issuers of e-cash can expect it to have a life cycle similar to that of most new products [Fig. 3, left]. During the early stages of development, large investments may be necessary before any returns are forthcoming. If the product is to be successful, at some point customer acceptance and product development both become sufficient to accelerate returns on investment. As products reach full maturity additional investment brings little additional return. This is the position of most paper-based payment systems today. Such "legacy" systems have reached high levels of efficiency and typically cannot yield significant improvements no matter how much new investment they consume.
[3] E-cash can be expected to have a life cycle similar to that represented by an S-shaped curve [left]. During early stages of development, large investments may be vital before returns are forthcoming. When the "knee" in the S-curve is reached, returns accelerate as a function of investment size -- a turning point that corresponds to the critical mass of market acceptance [curves at right].
Consumer acceptance is shown as a function of investment in point-of-sale (POS) equipment [blue curve]. A certain number of merchants must have it before any acceptance by consumers can be expected. And no matter how pervasive merchant POS gear becomes, total consumer acceptance is virtually impossible.
Merchant investment in POS e-cash equipment is shown as a function of consumer e-cash acceptance [red curve]. Any merchant investment presupposes at the least some pre-existing consumer acceptance, and total merchant acceptance is never achievable.
The critical mass needed for market development needs a certain level of consumer and merchant acceptance [lower-left intersection of the two curves]. Lower levels of consumer or merchant acceptance will not produce a sustained market [depicted by path of arrow A]. Any level of consumer or merchant acceptance that is above the critical mass will result in market growth [path of arrow B].
The market will eventually reach its equilibrium size [upper-right intersection of the two curves].
Before any market dependent upon consumer acceptance can take off, a large number of them must be convinced that the product is worthwhile. But they will only be interested in acquiring e-cash if they can use it in transactions -- a lot of transactions. That means that retailers will have to be willing to accept e-cash and to invest in hardware and software at the point of sale (POS), as they did for credit card payment systems. Retailers will not be willing to make those investments until they see that consumers are willing to use e-cash -- so there is a "chicken-and-egg" problem. Which comes first, consumer acceptance or merchant investment? The answer, of course is both which means that a critical mass of consumer and merchant participation must be established before an e-cash system can take off. When that finally happens, if it ever does, new consumers and merchants will he drawn to the system by its success [Fig. 3, right].
The key to any monetary regime is the confidence of the consumers and participating institutions. Holders of currency need to know that it will be acceptable to others and keep its value over time -- and their confidence can be undermined by any number of apprehensions.
One is the fear of inflation. In the modern era, where local money has lost the confidence of the public it has been mainly as a result of high inflation caused by over-issuance of currency. The ability to earn seignorage creates an incentive for issuers to circulate increasing amounts of currency, leading to greater levels of inflation. When this happens to local currency, foreign currencies are often brought in and adopted by local consumers and merchants to conduct transactions and provide a store of value. The foreign currencies of choice are issued by governments that have learned the lesson that controlling inflation yields the long-term benefits of economic stability. Consumers contemplating whether to accept e-cash issued by either a government or private institution should wonder if the issuer has learned this lesson.
Another consumer concern is the fear of a financial failure. In most advanced nations, bank deposits are insured by the government against loss in the event of a bank's failure. The government agency providing that insurance in the United States, the Federal Deposit Insurance Corp. recently announced its belief that e-cash will not be similarly insurable, because it is not tied to a deposit account. Consumers must therefore consider the possibility that the issuer of their e-cash might collapse. The collapse of an issuer would beg the question of whether anyone would continue to accept the e-cash. Would other financial institutions redeem it?
Because banks are the most likely issuers of e-cash, one question is whether the safety-and-soundness regulation to which they are subject is sufficient to put consumers' minds at ease. Given the likelihood that only small amounts of money will be stored electronically for any one consumer, this protection may well be enough. In the past, currency was routinely issued by the private sector; consumer acceptance varied widely [see "Private currency brief examples," next page].
Consumer acceptance can also be undermined by the fear of fraud. The currency issuer requires protection from the age-old problem of counterfeiting. If e-cash issued by either a government or a private institution could be replicated illegally, it might be extremely difficult to detect and stop because counterfeit e-cash could be impossible to differentiate from the genuine article. Since e-cash would be cheap to reproduce, counterfeiting may give rise to an enormous amount of phony money. That could destroy the financial soundness of the currency's true issuer which might have to redeem the counterfeit currency. Because such a meltdown could completely undermine consumer confidence in the system, experts in cryptology, including government agencies, are working with potential issuers of e-cash to find ways to prevent counterfeiting
The wild card in the future of e-cash is the important role played by governments. The Federal Reserve and other regulators of the U.S. payment system have stated their intention to stay out of these markets to the greatest possible extent, thereby allowing products to develop in an unbiased and unencumbered fashion. However earnest such statements may be, certain issues can be settled only by governments, and when they are markets will be affected in unpredictable ways. These issues include requirements for consumer disclosure and liability, as well as ways of dealing with transactions that are attempted but not completed. Indeed, whole areas of commercial and consumer law in all countries will have to be rewritten to accommodate developments that were not even contemplated when most existing laws were drafted.
The most contentious issue of all may be deciding which firms should be allowed to issue e-cash. While the market might be made most competitive by allowing anyone to do so, the possibility that an issuer might fail and therefore be unable to redeem its currency poses risks to all participants in the system. These risks can be largely mitigated by subjecting issuers to the type of safety-and-soundness regulation that most countries impose only on banks. However, many regulators believe that such supervision can be conducted only by requiring issuers to actually be banks. The European Monetary Institute (EMI) -- representing the central banks of the European Community -- has recommended that non-banking organizations should be allowed to issue stored-value cards only on an exceptional, case-by-case basis.
Governments can also influence the development of the market by taking the lead in using e-cash itself. The U.S. Congress, for example, has required the Treasury Department to conduct all transactions -- except tax refunds -- electronically by 1999. As a result, thousands of firms will be forced to install systems to handle the transition from paper-based payments.
Millions of individuals receiving government entitlements will also be brought up to speed through the U.S. governments Electronic Benefits Transfer (EBT) program, which will require recipients to use stored-value cards carrying an array of benefits, including cash and food stamps. Through EBT, a demographic group that has not been effectively reached by many other payment technologies will be propelled directly into the 21st century.
Finally, most national governments today claim a monopoly over the issuance of currency. Giving up that status may be costly in terms of seignorage, yet this may be the only way to make markets as competitive as they can be. Private markets, for example, are more likely than governments to develop interest-bearing e-cash, as private issuers competing for balances may need to pay interest to keep customers.
Before merchants invest in POS equipment they will have to know what to buy. If e-cash is not standardized, they will be acquiring equipment that might be rendered obsolete when changes are made to e-cash itself, the business protocols involved in using it, or the hardware necessary to process it. As for consumers, they will not want to carry more than one e-cash wallet or keep different types of e-cash in their PCs to conduct transactions with different merchants.
For these and other reasons, institutions with interests in seeing the e-cash market develop will have to work together to standardize many processes involved in electronic commerce. MasterCard and Visa have demonstrated their willingness to cooperate by creating the Secure Electronic Transactions (SET) protocol for transmitting credit card data over the Internet [See "Locking the e-safe"]. If this is a sign of things to come there is reason to be optimistic.
Nonetheless, if different firms or groups of firms develop incompatible systems, users may have to choose one over another After those choices have been made, they may be difficult or expensive to reverse. In other words, such systems will in effect have "captured" their customers. This would retard technological progress because products and services with a captive customer base do not have to sustain the level of innovation normally seen in competitive markets. All systems should therefore be compatible, allowing them to compete for merchants and consumers without forcing the market to make irreversible decisions.
For example, home PC electronic-commerce software developed by one vendor should be easy to replace with software developed by any other vendor, as well as compatible with the software used by all financial service providers. Otherwise, there will be a risk that a software provider with a large market share might try to impose universal compatibility by forcing everyone to switch to its system. The dominant firm could control many aspects of home-based electronic commerce, slow down the pace of innovation, and even charge monopolistic prices.
To provide a competitive environment, e-cash systems should be designed to encourage a large number of institutions to compete head-to-head on a level playing field. This goal will probably mean that potential issuers of e-cash will have to be allowed to plug into fully developed support systems even after they are already up and running thus permitting latecomers to save money by avoiding the development costs incurred by early players. This may mean that early players will have to be motivated solely by the opportunity to establish an advantage in consumer acceptance.
Many futurists bullish on e-cash are afraid to ask a simple question: how much worse off would we be without e-cash? The alternative is not necessarily a permanent paper-based system but, rather, an electronic-payment system capable of replacing paper currency in whole or in part, but without acting as currency itself.
On the Internet, for example, electronic commerce may develop quite efficiently simply by using credit card or bank account numbers that represent each customer's account. Because these systems are quickly developing an ability to work reasonably well off-line, they could have tremendous cost advantages over on-line credit or debit card systems. In off-line systems settlement orders instructing the payer's bank to transfer funds to the payee's bank are batched and processed at a later time; in on-line systems, settlement takes place immediately, before the transaction is consummated, requiring more expensive electronic communications.
With the development of the SET protocol, the implementation of off-line Internet systems may accelerate over the next few years. In POS transactions, off-line debit cards are bringing costs down below the levels associated with credit card transactions [Fig 1]. As for convenience, there may be little difference to consumers between e-cash and off-line debit cards.
______________________
About the author
Mike ter Maat, an engineer at heart and by academic training, is a senior economist with the American Bankers Association, Washington, D.C., where he has worked on a wide range of issues, including electronic payment systems. Earlier he served as a commercial loan officer at the Goldome Bank for Savings, New York City, and at Carteret Savings Bank, Morristown, N. J. He has consulted on financial operations and economics to the World Bank, the International Finance Corp., the Overseas Private Investment Corp., and the U.S. Office of Management and Budget. He subsequently worked on federal budget issues at the Office of Management and Budget and was a communications specialist for the Bush reelection campaign in 1992.
[Three note images omitted]
At least 60 countries and colonies have had experience with competitive private currency, most notably Scotland (1716-1844), (1817-1914) and the United States (1837-1930). Hong Kong still has a private -- though not very competitive -- currency system, based on notes issued by two local commercial banks [top] Most scholars think that many of these episodes were largely successful, though each was in the end replaced by currency issued by government-controlled central banks. Even the Hong Kong experience is to end this year with the transfer of authority to China.
In the United States, during the days of the state bank note model, also known as the Free Banking Era (1837-63), there was no national standardized currency; each bank printed and issued its own notes [bottom]. Moreover, each state had its own statute governing the currency of its banks. Common elements in state bank laws included requirements for banks to hold in reserve state-issued bonds totaling 100 percent of the currency they issued and to redeem their currencies on demand at par value in gold or silver.
Nonetheless, bank currency was often accepted only at less than face value, either because a bank was deemed unsafe or because redemption was impeded by the physical distance to the bank. The financial safety of banks depended largely on the quality of the underlying state-issued bonds rather than on other characteristics of the banks themselves.
The U.S. national bank note model (1863-1930) imposed national uniformity on both the appearance and the legal regulation of bank-issued currency [middle]. The Federal government printed the notes, but banks were allowed to stamp the notes with their own names, to put them into circulation, and to continue earning seignorage. National bank notes were subject to 111 percent reserve requirements -- for each $9 in notes a bank issued, it had to hold $10 in Federal government bonds. The standardization of bank notes achieved its objective: a currency that was accepted at par value throughout the country.
Notwithstanding this success, the national banking system ultimately failed because of structural problems in the way reserves were maintained. Rural banks held them in larger city banks, which in turn counted those reserves toward their own reserve requirements. When rural banks withdrew their reserves during economic contractions, city banks found themselves holding insufficient reserves and reacted to their liquidity problems by calling in short-term loans, thereby exacerbating the economic contraction. The creation of a central bank -- the U.S. Federal Reserve -- resolved this problem by requiring banks to maintain their reserves with the Fed. Although the national banking system was replaced by the Federal Reserve System in 1914, national banks did not lose their circulation privileges until 1930.
-- Keith Leggett, American Bankers Association
Report of the Payment System Task Force, a publication of the American Bankers Association, Washington, D.C., discusses various recommendations on the major competitive and public policy issues that will affect future payment systems. Call 202-663-5000 for a copy.
"Increasing Returns and the New World of Business," by W. Brian Arthur, Harvard Business Review, July-August 1996, explains the modern economics of standardization and scale applicable to high-technology markets.
Emerging Electronic Methods for Making Retail Payments (Congressional Budget Office, Washington, D.C., June 1996) discusses the economic and public policy issues created by emerging payment technologies. Contact Linda Schimmel at 202-226-2809.
Creating the Value Network: Fifth Annual Special Report on Technology in Banking, published by Ernst & Young LLP, 1996, describes the state of technology and the pace of change in retail banking service-delivery systems. The person to call is Tonya Brooks-Taylor at 617-859-6346.
Banking and Technology Issues, published by Fried, Frank, Harris, Shriver & Jacobson (Washington, D.C., 1996), is a collection of papers discussing the legal and regulatory issues being introduced by new payment technologies. To get in touch with Thomas P. Vartanian, the editor and managing partner, call 202-639-7200.
"How Would the Invisible Hand Handle Money?" by George A. Selgin and Lawrence H. White, in the Journal of Economic Literature, Vol. XXXII (December 1994), pp. 1718 1749), examines the literature on the lessons that historical markets offer for private currency.
Michael A. ter Maat's "A Cross-Sectional Analysis of the Development of Corporate Equity Securities Markets," a doctoral dissertation at George Washington University (1991), analyzes the need for a critical mass in the development of financial markets. Contact the author at 202-663-5354.
Howard Anderson
The Yankee Group
Electronic wallets. Internet-driven mail and electronic cash. Credit cards that are debit cards capable of being refilled with electronic money spendable like pocket change. Banks that not only have no branches but exist solely in cyberspace. Indeed, we are entering a strange new world. Discount brokers want you to power up your computer, access your portfolio, and trade your stocks -- all electronically. Brokerage houses want to be your banker, and banks want to be your broker.
It is value, in electronic form. In the old days, silver certificates pieces of paper -- promised the bearer that the "bill " could be redeemed for real silver. Electronic money takes that IOU and reduces it to an electronic form. It will evolve from existing technology from the credit cards that most middle-class people carry now.
No: e-money will threaten every major bank, upsetting the balance of power between financial institutions, retailers, and consumers. It will hobble governments as it undercuts their ability to control the flow of money with monetary policy.
To begin with "money" and "information" are one and the same thing. If we can store, forward, and manipulate information -- and we do every day -- we can do the same thing with money. Combine that ability with the awesome future power of the Internet, which in a few years will be available to 30 percent of U.S. homes, and computers, networks, and money will begin to converge, starting the process of undermining the financial status quo.
Example: Its Feb 1, 2003. You are sitting at your personal computer, which is attached to the Internet scanning vacation spots for a summer holiday. After you find a likely resort, you take a video tour through its rooms, and then immediately transfer US $500 (previously downloaded into your computer from a bank or a bank-substitute) from your computer to the resort's account to hold your place. Or you are shopping for a new car and by jumping on a chat line find out what other buyers think about a certain model. Then you put your requirements up for bid with two dozen local dealers -- buying it from the least expensive of them -- without leaving your living room.
It is happening already. Some 40 million U.S. homes have personal computers and 25 percent of them are connected to an on-line service that gives them Internet access. Banks as we know them have been obsolete for years, rivaling even the U.S. Postal Service as an antiquated remnant of an older world. Both banks and post offices centralized distribution, information, and credibility. Thanks to networks and computers, e-money makes it possible to decentralize and distribute those functions. At first, it will look like an extension of today's technology; in reality, it will be a revolution. Think about what a "home ATM" would be like. One could get "money" in an electronic form, make "deposits," and transfer or receive funds and e-mail at any time from anyone.
Of course not. The Yankee Group categorizes 16 million households in the United States as "Technologically Advanced Families." They will be the early adopters for this time- and labor-saving service. No doubt there will be the usual glitches, some level of fraud, and the occasional horror story -- but right behind those 16 million households are another 32 million that will also begin to use electronic money. Certainly there will be the usual pitfalls and obstacles, the obligatory security nightmares, but the logic of electronic money will stomp over these impediments.
The brain trusts at major banks, even now, suspect that the existing bank model is 30 years out of date and obsolete. A bank today needs no branches no employees, and perhaps no ATMs -- just a series of computers with connections to the world. Such a bank would not issue checks, but it would dispense information, lend money, and move data. Banking lifecycles are only 30 years long. It is time to reinvent the bank.
Bill Gates's Microsoft Network is doing just that. Citicorp, NationsBank and Bank of America as well as Fidelity and Charles Schwab, are conducting embryonic tests right now. Such new companies as CyberCash, Digicash, and Mondex are attempting to align themselves with brand names like Visa and American Express to build credibility. This year, the venture capital industry will raise $4.8 billion in new funds and 60 percent of this will go into computer, software, and Internet start-ups.
Every government wants the ability to control the national economy through monetary policy -- by restricting credit when the economy is overheated and loosening credit when the economy is sluggish. But what will happen when someone wants a construction or car loan, posts a request on the Internet, and receives a response from 150 banks near-banks, and quasi-banks around the world?
Today, countries have central banks that lend money to private banks and regulate monetary policy by fiat; but tomorrow, that monopoly power is stripped if quasi-banks around the world can perform the same financial function.
The treasurers offices of large companies sweep all their accounts of excess money every morning and reinvests that by the end of the day. With the right software it will be possible to do the same thing at home. If an overseas bank is paying interest rates that are 3 percent higher than those of its domestic competitors tonight, the intelligent agent program, tied to an on-line account, may lend money to the foreign institution. Tying networks to home software and to money will be the catalyst.
This e-money revolution doesn't have to be ubiquitous to have serious reverberations. Remember, it's not just banks and governments; whole industries, notably, telecommunications, have communications lines, customer files, and a desire to utilize those networks to create new value. Regulatory barriers are going to fall because technology itself makes them obsolete. Just as the Internet and fax machines make it much harder for even dictatorial governments to embargo the news, governments will be powerless to stop flows of electronic money.
If raw communications should become a profitless commodity the owners will move higher up on the "food chain" where they can make money on the value added. If communications companies can issue credit cards as they do now, they can issue debit cards. Other major non-banking companies would also like to move into this business. Will consumers accept them? Will they forego checkbooks to move funds over the Internet? What's in it for the consumer?
Lets face it although e-money will require changes in consumer behavior, the whole transition is going to be a lot less risky than it looks now. The best brains in America are on the problem. The infrastructure is almost in place. The Internet is uniquely capable of handling both the volume and the data transfer. The applications do not need a vast amount of bandwidth. Three years from now 100 million people in the United States will have direct Internet access. Security problems will never be totally solved, but they will be relegated to the "annoyance" category, like cellular phone fraud.
As much as governments would like to do so, they will essentially be powerless. Everyone needs banking, but not everyone needs banks. Each consumer will have multiple options. If cyberbankers merely lend out money they have on electronic deposit, the regulatory issue will be moot. But the U.S. Federal Reserve System allows banks to lend out several times what they actually have on hand. Once near-banks, quasi-banks, or non-bank banks are joined to the network, new forms will emerge. Only 15 years ago Merrill Lynch got together with Bank One and found a loophole in the arcane banking laws. Sears Roebuck issued the Discover Card and created Sears Bank and Trust. If a retailer can own a bank, why can't a telephone company or a software company do so? Today's banks underwrite counter-party risks that are compensated by high fees for late credit card payments. That issue has yet to be addressed in cyberland. Perhaps some sort of limited liability, like a high-deductible insurance cooperative, will emerge.
Inevitable yes, easy no. There are major problems transferring funds and making sure that people are really who they claim to be. Cryptographers are going to have a field day. Companies like First Virtual and CyberCash will have to show that their technologies work before anyone will trust them.
With credit cards. Today many people carry enough plastic in their wallets to build a small boat. Banks and credit card companies will begin to convince, indeed, "bribe" us, to give up our credit cards (with their "free" float) for debit cards. That will be the easy part. These institutions will begin by making float available -- for a while -- on debit cards, and making it harder to obtain on credit cards.
The most technologically sophisticated U.S. households -- about 16 percent -- will migrate to smartcards, which will carry both information and "money." Theoretically, one might be able to plug a smartcard into a computer, replenish one's money supply, and use it to pay tolls on the highway.
Sure. The whole issue of digital signatures and public-key encryption will take three years to resolve. Whenever there are too many solutions, too many standards, innovative companies wait and see. Its a lot easier to put the industry's full weight behind a generally accepted standard solution -- and that is coming.
If your 16-year-old wants to buy software today, she has to go to a store. Soon, your kid will send a code from her PC to a bank that will take the money out of her account and authenticate the message. Then the bank will send the money directly to an electronic software retailer via a private key. The electronic software store will know that "good funds" are on hand because this will be confirmed through the bank's public key, which the store will resubmit electronically to the bank, simultaneously sending the new software to your kid over the Internet.
Exactly! But let's go one step further. Why involve a middleman at all? Already, we have about US $45 billion moving through electronic commerce. What is to prevent companies from dealing directly with each other -- or with consumers? We will have to build bulletproof verification and validation procedures, but the gears are already in motion. Remember the consumer has a number of relationships with a wide variety of companies -- such as Bank of Boston, Visa, and Bell Atlantic, but also Netscape, Intuit, WalMart, Fidelity, and Merrill Lynch. Who is to say that the loyalty of one is higher than another?
In 10 years perhaps 12-15 percent of all transactions will take place electronically. Then the pace will speed up. It takes about five years to get 1 percent of households to adopt a new technology, but only about another year to get the second 1 percent. From then on, the pace of adoption grows geometrically. Today, 80 percent of U.S. households have VCRs and a large percentage of the population uses ATM machines. These technologies took years to get that first 1 percent of penetration.
Today, 70 percent of Internet users see e-mail as its primary benefit, and 30 percent view the World Wide Web as the chief reason to go on-line. By the year 2000, 50 percent will see e-mail as the primary driver and 40 percent will regard WWW access as the critical advantage, but that last 10 percent will be undertaking commercial transactions using e-money. At this point the revolution will already have a strong foothold. Remember that e-money is just e-mail for money.
You got it.
_____________________
About the author.
Howard Anderson is managing director of the Yankee Group, a Primark company (with offices in Boston, London, Tokyo, and Sydney) that analyzes the intersection of technology and consumer behavior. He can be reached at handerson@yankeegroup.com.
[End of Technology and the Electronic Economy]